01 Run list-topics command (OSX/Linux/UNIX) to retrieve the list with all the SNS topics available in the selected region and their Amazon Resource Names (ARNs):
aws sns list-topics
--region us-east-1
02 The command output should return the requested SNS topic ARNs:
{
"Topics": [
{
"TopicArn": "arn:aws:sns:us-east-1:
123456789012:cloud-conformity-sns-topic"
},
{
"TopicArn": "arn:aws:sns:us-east-1:
123456789012:aws-cloudtrail-sns-topic"
}
]
}
03 Run get-topic-attributes command (OSX/Linux/UNIX) to list the selected SNS topic policy using custom query filters and the ARN returned at the previous step as resource identifier:
aws sns get-topic-attributes
--region us-east-1
--topic-arn arn:aws:sns:us-east-1:123456789012:cloud-conformity-sns-topic
--query 'Attributes.Policy'
04 The command output should return the SNS topic policy document in JSON format:
{
"Version": "2008-10-17",
"Id": "__default_policy_ID",
"Statement": [
{
"Sid": "__default_statement_ID",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"SNS:Publish",
"SNS:RemovePermission",
"SNS:SetTopicAttributes",
"SNS:DeleteTopic",
"SNS:ListSubscriptionsByTopic",
"SNS:GetTopicAttributes",
"SNS:Receive",
"SNS:AddPermission",
"SNS:Subscribe"
],
"Resource": "arn:aws:sns:us-east-1: ... ",
"Condition": {
"StringEquals": {
"AWS:SourceOwner": "123456789012"
}
}
},
{
"Sid": "__console_sub_0",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"SNS:Subscribe",
"SNS:Receive"
],
"Resource": "arn:aws:sns:us-east-1: ... ",
"Condition": {
"StringEquals": {
"SNS:Protocol": "http"
}
}
}
]
}
Identify the
Effect and
SNS:Protocol elements defined within the policy statement and verify their value(s). If the
Effect value is set to
"Allow" and the
SNS:Protocol contains the
"http" value instead of "https" (as shown in the example above) or the
Effect element is set to
"Deny" and the
SNS:Protocol contains the "https" value, only the HTTP delivery protocol is enabled, therefore the access policy defined for the selected Amazon SNS topic is not secured, allowing unencrypted subscription requests to be made to the existing SNS subscription endpoints.
05 Repeat step no. 3 and 4 to verify the access control policy for other SNS topics available in the current region.
06 Change the AWS region by updating the --region command parameter value and repeat steps no. 1 - 5 to perform the audit process for other regions.

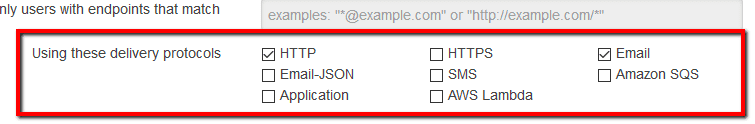
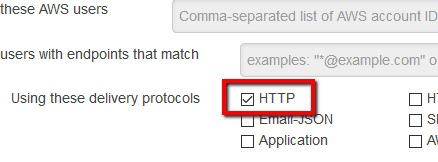
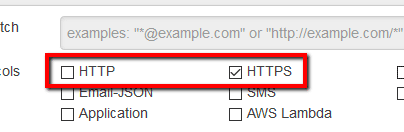 to enforce HTTPS-only subscriptions to the selected SNS topic endpoints.
to enforce HTTPS-only subscriptions to the selected SNS topic endpoints.