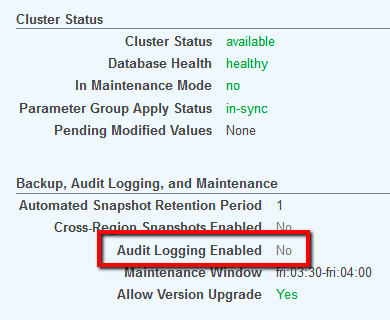
Ensure audit logging is enabled for Redshift clusters for security and troubleshooting purposes.
This rule can help you with the following compliance standards:
- PCI
- HIPAA
- GDPR
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
Once enabled, the Amazon Redshift Audit Logging feature starts recoding database usage information such as queries performed and connection attempts, logging data that can be extremely useful for security and compliance audits or troubleshooting sessions.
Audit
To determine if audit logging is enabled for your Amazon Redshift clusters, perform the following:
Remediation / Resolution
To modify your Amazon Redshift clusters configuration in order to enable audit logging for the databases provisioned within these clusters, perform the following:
References
- AWS Documentation
- Amazon Redshift FAQs
- Database Audit Logging
- Managing Clusters Using the Console
- Manage Clusters Using the Amazon Redshift CLI and API
- AWS Command Line Interface (CLI) Documentation
- redshift
- describe-clusters
- describe-logging-status
- enable-logging
- s3api
- create-bucket