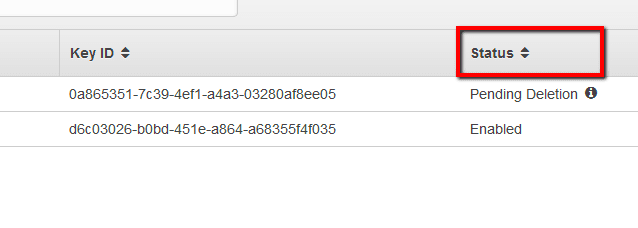
Identify any disabled AWS KMS Customer Master Keys (CMK) that have been accidentally or intentionally scheduled for deletion in order to prevent losing any data encrypted with these keys.
This rule can help you with the following compliance standards:
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
When a CMK is deleted, all data encrypted under that key becomes unrecoverable. However, AWS does not remove the key instantly, instead enforce a waiting period between 7 and 30 days to verify whether the key is still needed to decrypt the data and allows you to recover the key by canceling the scheduled delete action.
Audit
To determine if you have any KMS Customer Master Keys (CMK) scheduled for deletion, perform the following:
Remediation / Resolution
AWS Key Management System allows a waiting period between 7 and 30 days before the key is completely deleted and unrecoverable. The deletion can be canceled any time before the selected waiting period expires. To cancel any KMS CMK scheduled for deletion, perform the following:
References
- AWS Documentation
- What is AWS Key Management Service?
- AWS Key Management Service Concepts
- Deleting Customer Master Keys
- AWS Command Line Interface (CLI) Documentation
- kms
- list-keys
- describe-key
- cancel-key-deletion