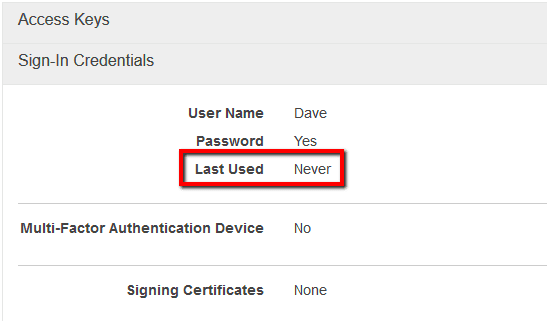
Identify and remove any unused AWS IAM users, which are not designed for API access, as an extra security measure for protecting your AWS resources against unapproved access.
This rule can help you with the following compliance standards:
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
Removing unused IAM users can reduce the risk of unauthorized access to your AWS resources and help you manage the user-based access to the AWS Management Console more efficiently.
Audit
To identify any IAM users that have never been logged in, currently available in your AWS account, perform the following:
Remediation / Resolution
To remove any unused IAM users from your AWS account, perform the following:
References
- AWS Documentation
- AWS Identity and Access Management FAQs
- Managing IAM Users
- AWS Command Line Interface (CLI) Documentation
- iam
- list-users
- list-access-keys
- delete-user