Identify any non-root Amazon EBS volumes that appear to be idle and remove them from your account to help lower the cost of your monthly AWS bill. By default, an EBS volume is considered "idle" when meets the following criteria:
- The total number of VolumeReadOps and VolumeWriteOps recorded per day for the last 7 days has been less than 1 (one) on average.
The AWS CloudWatch metrics used to detect idle EBS volumes are:
- VolumeReadOps and VolumeWriteOps - the total number of disk I/O operations in a specified period of time (Units: Count).
Note 1: This rule can be applied to all AWS EBS volume types (gp2, io1, st1 and sc1). However, the rule excludes EBS boot (root) volumes.
Note 2: You can easily change the default threshold for this rule on Cloud Conformity console and set your own value for each condition, i.e. VolumeReadOps and VolumeWriteOps, as well as adjusting the time period, such as the last 7 days, to configure the volumes idleness based on your specific requirements.
Note 3: For this rule Cloud Conformity assumes that your EBS volumes are tagged using a "Role" tag that provides visibility into their usage profile and help you decide whether it`s safe or not to delete them.
Note 4: Backup your data - once an EBS volume is deleted, the data available on it will be completely lost. Since EBS snapshots are much more cost-effective because the volume data is stored as an object by the AWS S3 service, creating volume snapshots before removal is highly recommended.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
optimisation
Idle EBS volumes represent a good candidate to reduce your monthly AWS costs and avoid accumulating unnecessary usage charges.
Audit
To identify any non-root idle AWS EBS volumes currently available in your AWS account, perform the following:
Remediation / Resolution
Option 1: Delete any AWS EBS non-root volumes that are currently running in the idle mode. To remove the specified volumes, perform the following actions:
Option 2: Disable the rule check. If the selected idle EBS volume is needed (its role within your application stack/environment is important), you may want turn off the conformity rule check for the specified EBS volume from the Cloud Conformity console.
References
- AWS Documentation
- Trusted Advisor Best Practices (Checks)
- Monitoring the Status of Your Volumes
- Amazon EBS Metrics and Dimensions
- Device Naming on Linux Instances
- Device Naming on Windows Instances
- AWS Command Line Interface (CLI) Documentation
- ec2
- describe-volumes
- create-snapshot
- delete-volume
- cloudwatch
- get-metric-statistics

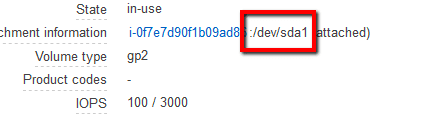
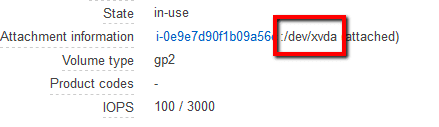
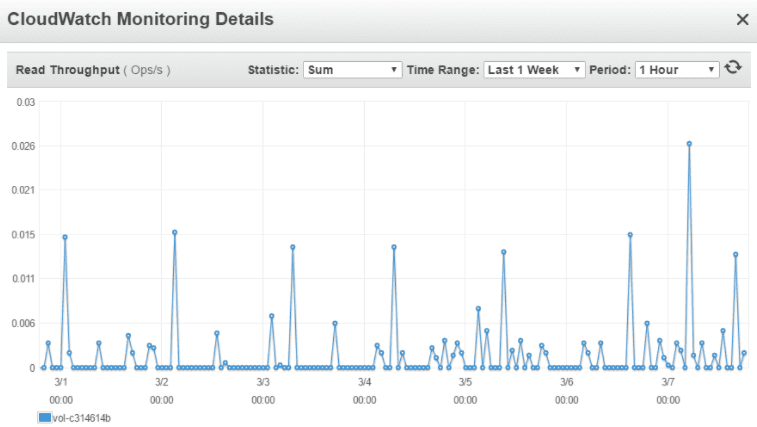 , the selected EBS volume qualifies as candidate for the idle resource. Click Close to return to the dashboard.
, the selected EBS volume qualifies as candidate for the idle resource. Click Close to return to the dashboard.