Ensure that Amazon CloudFormation is used within your AWS account to automate your cloud infrastructure management and deployment. CloudFormation is the AWS service that promotes the concept of Infrastructure as Code (IaC), which practically means writing code using a descriptive language (JSON or YAML) to manage configurations and automate provisioning of AWS infrastructures in addition to deployments
This rule can help you with the following compliance standards:
- APRA
- MAS
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
excellence
With AWS CloudFormation you will spend less time managing your cloud resources so you can have more time to focus on your applications. CloudFormation has several features and benefits that will allow you to build highly available, reliable, and scalable web infrastructures and automate them based on your application needs. The CloudFormation service benefits include: support for a wide range of AWS resources, stack customization via input parameters such as EC2/RDS instance types, EBS volumes size and port numbers, a declarative and flexible way to define your templates (simple JSON/YAML formatted text files), a user-friendly Drag-and-Drop interface that lets you create, visualize and edit your CloudFormation templates, the control over your infrastructure using a descriptive language (Infrastructure as Code), the ease of use and the integration with your favorite development and management tools or with other Amazon services such as Simple Notification Service (SNS).
Audit
To determine if Amazon CloudFormation is used within your AWS account for resource management and automation, perform the following:
Remediation / Resolution
In order to make use of AWS CloudFormation, you must work with templates and stacks. The templates are created to describe your AWS resources and their properties. Whenever you create a stack, CloudFormation provisions the AWS resources defined in your templates. To create your first stack (using a sample template), perform the following:
References
- AWS Documentation
- What is AWS CloudFormation?
- AWS CloudFormation Concepts
- Get Started
- Creating a Stack on the AWS CloudFormation Console
- Selecting a Stack Template
- Specifying Stack Name and Parameters
- Setting AWS CloudFormation Stack Options
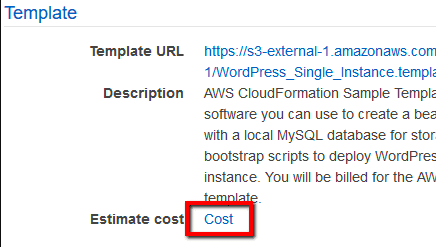
- Reviewing Your Stack and Estimating Stack Cost on the AWS CloudFormation Console
- AWS CloudFormation Best Practices
- AWS Command Line Interface (CLI) Documentation
- cloudformation
- describe-stacks
- create-stack


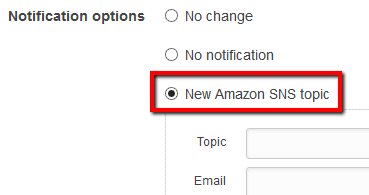 to enable it and create a new SNS topic and subscribe to it using your email address. In the Topic box enter a name for the new SNS topic and in the Email box enter the email address where you want to receive notifications. You can also choose Existing Amazon SNS topic to use a pre-existing SNS topic from the dropdown list:
to enable it and create a new SNS topic and subscribe to it using your email address. In the Topic box enter a name for the new SNS topic and in the Email box enter the email address where you want to receive notifications. You can also choose Existing Amazon SNS topic to use a pre-existing SNS topic from the dropdown list:  or choose Existing topic ARN and type the Amazon Resource Name of an existing SNS topic, e.g. arn:aws:sns:us-east-1:123456789012:MySNSTopic.
or choose Existing topic ARN and type the Amazon Resource Name of an existing SNS topic, e.g. arn:aws:sns:us-east-1:123456789012:MySNSTopic.