- Knowledge Base
- Amazon Web Services
- Amazon API Gateway
- Rotate Expiring SSL Client Certificates
Ensure that the client-side SSL certificates used by your Amazon API Gateway REST APIs for secure authentication at the API integration endpoint level are rotated before their expiration date. The number of days before the SSL certificate expiration, when the rotation is required, is 30 days (default threshold), however, this value can be configured in the rule settings, on your Cloud Conformity account dashboard.
This rule resolution is part of the Conformity solution.
The SSL client certificates used by Amazon API Gateway service are valid for 365 days. To avoid any downtime for your Amazon API Gateway REST APIs, rotate the associated certificates before they expire.
Note: This conformity rule assumes that your Amazon API Gateway REST APIs have client-side SSL certificates already attached.
Audit
To determine if there are any SSL certificates that are about to expire soon, attached to your API Gateway REST APIs, perform the following actions:
Using AWS Console
01 Sign in to your Cloud Conformity account, access Rotate Expiring SSL Client Certificates conformity rule settings and identify the number of days before SSL certificate expiration, when the client-side certificate must be renewed.
02 Sign in to AWS Management Console.
03 Navigate to API Gateway dashboard at https://console.aws.amazon.com/apigateway/.
04 In the left navigation panel, select APIs to access the APIs listing page.
05 Choose the API that you want to examine, then click on its name (link) to access the API details.
06 In the selected API submenu, click Stages to list the stages created for the selected API.
07 Under Stages, choose the API stage that you want to examine, then select the Settings tab from the dashboard top panel.
08 On the Settings panel, in the Client Certificate section, identify and note the ID of the SSL certificate associated with the selected API stage, available in the Certificate dropdown.
09 Go back to the navigation panel and select Client Certificates.
10 On the Client Certificates listing page, search for the SSL certificate entry identified at step no. 7 and check its expiration date, e.g.
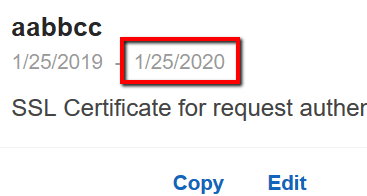
Based on the SSL certificate expiration date and the value identified at step no. 1, determine if the selected certificate needs to be rotated. If the selected client-side SSL certificate is about to expire soon, follow the instructions outlined in the Remediation/Resolution section to rotate the SSL certificate as quickly as possible.
11 Repeat steps no. 7 – 10 for each API stage created for the selected API.
12 Repeat steps no. 5 – 11 to verify other Amazon API Gateway APIs available in the current region.
13 Change the AWS region from the navigation bar and repeat the audit process for other regions.
Using AWS CLI
01 Sign in to your Cloud Conformity account, access Rotate Expiring SSL Client Certificates conformity rule settings and identify the number of days before SSL certificate expiration, when the client-side certificate must be renewed.
02 Run get-rest-apis command (OSX/Linux/UNIX) using custom query filters to list the IDs of the APIs available in the selected AWS region:
aws apigateway get-rest-apis --region us-east-1 --output table --query 'items[*].id'
03 The command output should return a table with the requested information (i.e. API IDs):
---------------- | GetRestApis | +--------------+ | aabbccaabb | | abcdabcdab | | abcdabcdab | +--------------+
04 Run get-stages command (OSX/Linux/UNIX) using the ID of the API that you want to examine as identifier and custom query filters to get the name(s) of the API stage(s) created for the selected API:
aws apigateway get-stages --region us-east-1 --rest-api-id abcdabcdab --output table --query 'item[*].stageName'
05 The command output should return the requested API stage name(s):
---------------- | GetStages | +--------------+ | Production | | Testing | | Development | +--------------+
06 Run get-stages command (OSX/Linux/UNIX) using the name of the API stage that you want to examine as identifier and custom query filters to return the ID of the SSL client certificate associated with the selected API stage:
aws apigateway get-stages --region us-east-1 --rest-api-id aabbccaabb --query 'item[?(stageName==`Production`)].clientCertificateId'
07 The command output should return an array with the requested certificate ID:
[
"aabbcc"
]
08 Run get-client-certificate command (OSX/Linux/UNIX) using the ID of the client certificate returned at the previous step as identifier and custom query filters to return the timestamp when the selected certificate will expire:
aws apigateway get-client-certificate --region us-east-1 --client-certificate-id aabbcc --query 'expirationDate'
09 The command output should return the requested timestamp:
1579948577
10 The value returned by get-client-certificate command at the previous step is using the Unix/epoch time format, which represents the number of seconds that have passed since midnight UTC of 1 January 1970. To convert the returned value into a human-readable format, run the following command (replace the Unix timestamp with your own timestamp returned at step no. 8):
date -d @1579948577
11 The command output should return the RI purchasing date in a human-readable format:
Sat Jan 25 10:36:17 UTC 2020
Based on the SSL certificate expiration date returned by the command output and the value identified at step no. 1, determine if the certificate needs to be rotated. If the selected client-side SSL certificate is about to expire soon, follow the instructions listed in the Remediation/Resolution section to rotate the SSL certificate before this expires.
12 Repeat step no. 6 – 11 for each API stage created for the selected API.
13 Repeat steps no. 4 – 12 to verify other Amazon API Gateway APIs available in the current region.
14 Change the AWS region by updating the --region command parameter value and repeat steps no. 1 – 13 to perform the entire process for other regions.
Remediation / Resolution
To rotate an SSL client certificate that is about to expire soon, perform the following actions:
Using AWS Console
01 Sign in to AWS Management Console.
02 Navigate to API Gateway dashboard at https://console.aws.amazon.com/apigateway/.
03 In the left navigation panel, select APIs to access the APIs listing page.
04 Choose the API that you want to examine, then click on its name (link) to access the API details.
05 In the left navigation panel, select Client Certificates.
06 Click Generate Client Certificate button from the dashboard top menu to create a new SSL client certificate.
07 Once the certificate is created, click Edit and provide a descriptive title in the Description box, then click Save to apply the changes.
08 Update the backend server or service to include the new SSL certificate. Do not remove the existing client certificate yet from the server/service configuration.
09 In the navigation panel, select APIs to open the APIs listing page.
10 Choose the API that you want to reconfigure, then click on its name (link) to access the API configuration.
11 Within the API submenu, click Stages to list the stages available for the selected API.
12 Under Stages, choose the API stage that you want to reconfigure and select the Settings tab to access the selected stage configuration settings.
13 In the Client Certificate section, select the ID of the client-side SSL certificate created at step no. 4 from the Certificate dropdown list, then click Save Changes to apply the changes.
14 Update the backend server/service to remove the old SSL certificate (i.e. the one that is about to expire).
15 Now that the new client-side SSL certificate is active at the API stage level and backend server/service level, delete the old certificate from the Amazon API Gateway service dashboard:
- Go back to the console navigation panel and select Client Certificates.
- Choose the SSL certificate that is about to expire and click Delete Client Certificate (i.e. x button) to initiate the removal process.
- Within the Delete Client Certificate dialog box, click Delete <certificate-id> to remove the selected client certificate from the API Gateway service.
16 Repeat steps no. 9 – 15 to rotate SSL certificates for other API stages created in the selected API.
17 Repeat steps no. 3 – 16 to reconfigure other Amazon API Gateway APIs available in the selected region.
18 Change the AWS region from the navigation bar and repeat the entire process for other regions.
Using AWS CLI
01 Run generate-client-certificate command (OSX/Linux/UNIX) to generate a new a client-side SSL certificate for Amazon API Gateway service:
aws apigateway generate-client-certificate --region us-east-1 --description "New Client SSL Certificate Amazon API Gateway API"
02 The command output should return the SSL certificate metadata:
{
"clientCertificateId": "abc123",
"expirationDate": 1579948577,
"createdDate": 1611497555,
"pemEncodedCertificate": "-----BEGIN CERTIFICATE----- ... -----END CERTIFICATE-----",
"description": "New Client SSL Certificate Amazon API Gateway API"
}
03 Update the backend service or server to include the new SSL certificate. Do not remove the existing client certificate yet from the service/server configuration.
04 Run update-stage command (OSX/Linux/UNIX) using the name of the API stage that you want to reconfigure as identifier (see Audit section part II to identify the right stage) to attach the new SSL certificate, created at the previous steps, to the selected API stage:
aws apigateway update-stage --region us-east-1 --rest-api-id aabbccaabb --stage-name 'Production' --patch-operations op=replace,path=/clientCertificateId,value=abc123
05 The command output should return the command request metadata:
{
"clientCertificateId": "abc123",
"tracingEnabled": false,
"stageName": "Production",
"cacheClusterEnabled": false,
"cacheClusterStatus": "NOT_AVAILABLE",
"deploymentId": "cbacba",
"lastUpdatedDate": 1548413501,
"createdDate": 1548406766,
"methodSettings": {}
}
06 Now you can update the backend service/service to remove the old SSL certificate (i.e. the one that is about to expire).
07 Once the new client-side SSL certificate is active at the API stage level and backend service/server level, remove the old certificate from the API Gateway service by executing the delete-client-certificate command (OSX/Linux/UNIX) with the ID of the SSL certificate that you want to delete as identifier (the command does not produce an output):
aws apigateway delete-client-certificate --region us-east-1 --client-certificate-id aabbcc
08 Repeat steps no. 4 – 7 to rotate SSL certificates for other API stages created in the selected API.
09 Repeat steps no. 1 – 8 to reconfigure other Amazon API Gateway APIs available in the selected region.
10 Change the AWS region by updating the --region command parameter value and repeat the entire process for other regions.
References
- AWS Documentation
- Amazon API Gateway FAQs
- Use Client-Side SSL Certificates for Authentication by the Backend
- AWS Command Line Interface (CLI) Documentation
- apigateway
- get-rest-apis
- get-stages
- get-client-certificate
- generate-client-certificate
- update-stage
- delete-client-certificate
