PALEVO Worm Leads to Info Theft, DDoS attacks
What are PALEVO malware?
|
Name |
Price (EUR) |
|
Basic
Flooder |
100 |
|
Slowloris
Flooder |
200 |
|
USB
Spreader |
100 |
|
MSN
Spreader |
100 |
|
Visit |
100 |
|
Reverse
Socks Simple |
100 |
|
Post Data
Grabber |
200 |
|
Connect
Hook |
200 |
|
Adware
Simple |
100 |
|
Cookie
Stuffer |
200 |
In terms of file structure, PALEVO worms use different encryption techniques to conceal their main executable files.
Despite the incarceration of the people behind the Mariposa botnet, TrendLabsSM engineers recently observed several PAELVO-related activities in the wild that we blogged about in the following entries:
- Malicious .SWF File May Trigger a DoS Attack
- Spam Sends Malicious Links to Skype Users
- Mariposa/PALEVO on the Rise Again
PALEVO
variants
arrive
on users’ systems via
several infection vectors.
They
may, for
instance,
get PALEVO
variants via peer-to-peer (P2P) file-sharing applications like Kazaa,
BearShare, iMesh, Shareaza, and
Emule.
Some
variants may also arrive via
removable drives and
via
instant-messaging (IM)
applications
like MSN
Messenger.
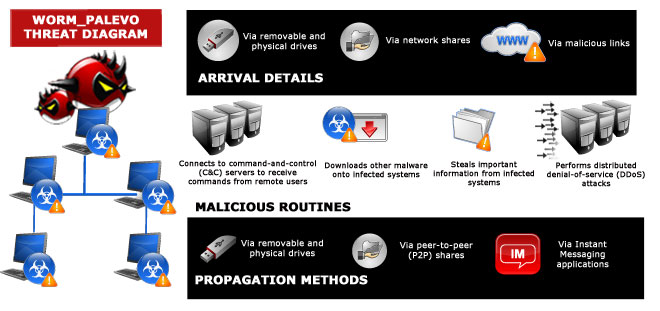
Typical of a worm, PALEVO malware may propagate via removal drives. These can be instructed by malicious users who control botnets’ command-and-control (C&C) servers to spread via MSN Messenger and other specific P2P applications.
PALEVO malware connect to specific sites to send and receive commands from C&C servers that are under the attackers’ control. Depending on the modules/features attackers bought, these may perform several tasks on infected systems, including downloading files, initiating IM applications, propagating via P2P sites and via removable drives, harvesting passwords from specific Web browsers, performing UDP and TCP flooding, scanning ports, and pushing adware to other infected systems.
PALEVO malware steal browser passwords, particularly for Internet Explorer (IE) and Mozilla Firefox. These may include passwords for personal (e.g., social networking sites), banking, and e-commerce sites.
Important data like site login credentials stored on infected systems can end up in the hands of the cybercriminals behind this threat. Unless immediately changed, these may be used to initiate unauthorized bank transactions, which can lead to actual monetary losses. Cyberbcriminals may also use the stolen personal data for several other malicious activities.
Because PALEVO variants access a C&C server, attackers can push other malware to other vulnerable systems. These also access specific sites to download updated copies of themselves, apart from downloading other malware. The infected systems then exhibit all of the behaviors of the downloaded malware, making the family a persistent threat.
Some PALEVO variants are capable of initiating DDoS attacks on several entities. These attacks, including those against servers, for instance, prevent systems from properly working and renders these inaccessible to authorized users.
News of a new botnet using a modified version of PALEVO malware for malicious activities. So far, this said botnet has infected systems in 172 countries, including the United States, Russia, Brazil, China, the United Kingdom, and Iran. Because PALEVO malware are still active, users must be on the lookout for related variants and should employ safe computing practices to prevent system infections and to ensure that their systems do not become parts of botnets.
Apart from
the
above-mentioned
possible
payloads,
some
PALEVO samples
may also vary in terms of structure and compression. As
such, we
may see
binary
samples
that deviate from the usual structure, which
can
make
detection challenging for
security researchers and analysts.
- Use and properly
configure
Windows Firewall for all incoming connections from the
Internet for
Windows-based systems.
- Disable AutoPlay
to prevent the
automatic
execution of malicious
executable files in
removable and
network
drives.
- Always keep systems up
to date by
downloading and applying the latest security
patches.
- Avoid clicking
dubious-looking URLs from unknown sources.
- Immediately
isolate infected systems from
networks to prevent further
infection.