Phishing, Other Threats Target Email and Video App Users
 Insights and analysis by Paul Christian Pajares
Insights and analysis by Paul Christian PajaresWe have seen several threats abusing tools utilized in work from home (WFH) setups. Cybercriminals are using credential phishing sites to trick users into entering their credentials into fake login pages of email and collaboration platforms and videoconferencing apps. Although these threats are not new, the need for better solutions is heightened due to the current experience and landscape.
[Related: The Rising Tide of Credential Phishing]
Here, we analyzed some of the tools that many companies use for WFH arrangements: Outlook on the web (formerly known as Outlook Web Access) and other Office 365 applications such as SharePoint, and videoconferencing apps WebEx and Zoom.
Phishing campaigns using Outlook on the web and Office 365 as lures
Credential phishing using Outlook on the web and Office 365 as bait has hit users in several countries. Data from our Smart Protection Network indicates over 50,000 phishing detections from January 2020 to April 27 of the same year, with the threats affecting users in the United States, Germany, Canada, Taiwan, Japan, Australia, Hong Kong, and other countries.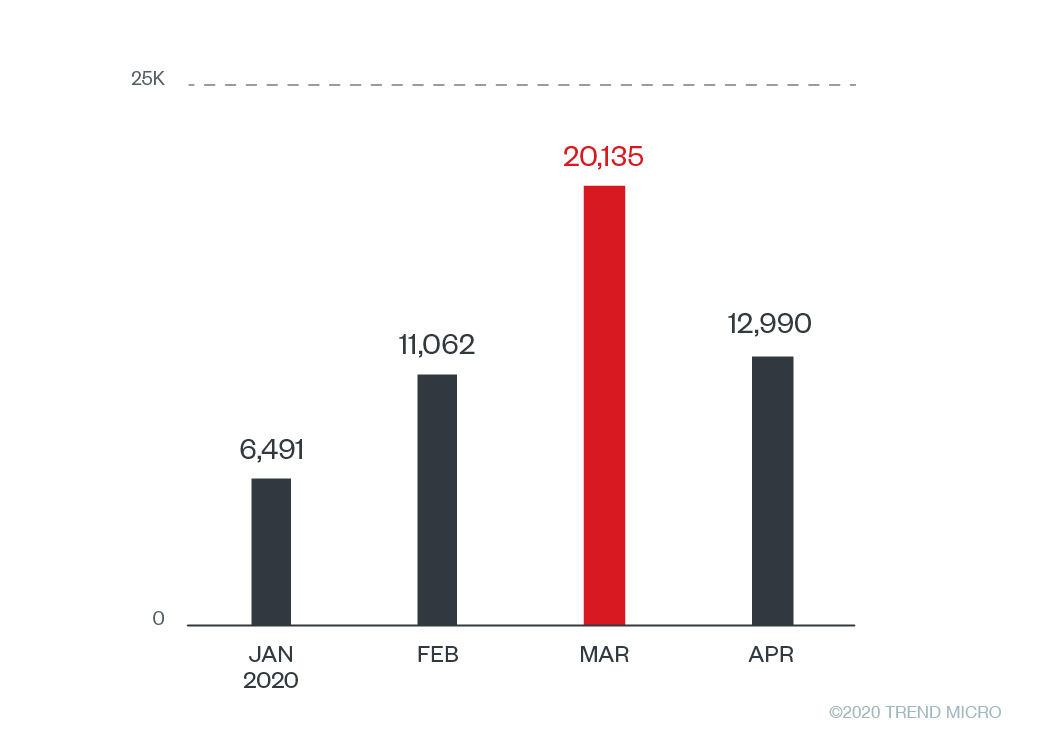
Figure 1. Phishing detections related to Office365 and Outlook from January to April 2020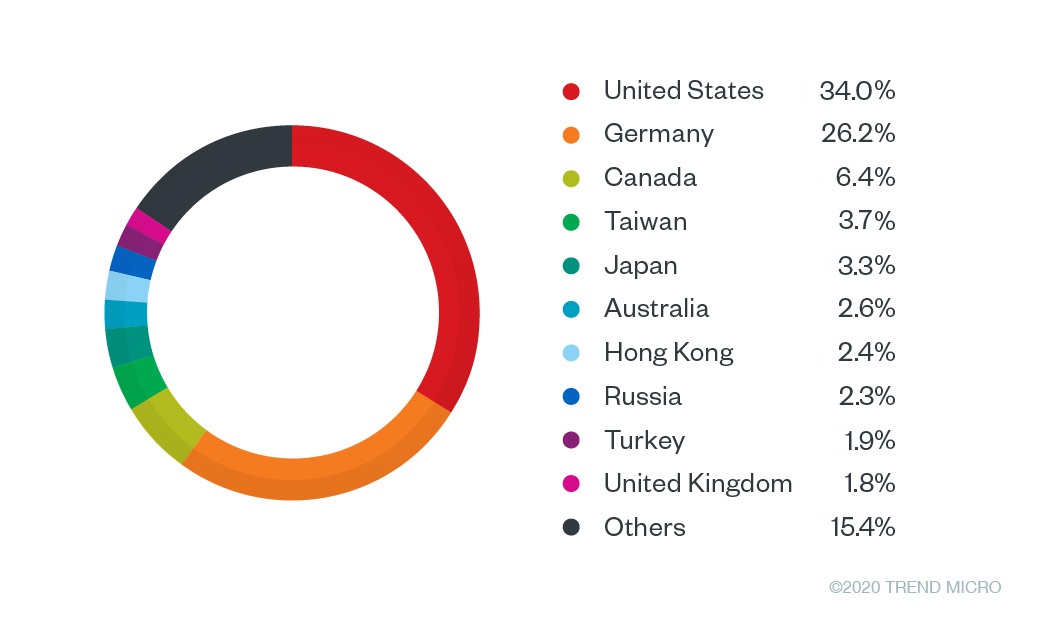
Figure 2. Top countries with users encountering phishing attempts related to Office365 and Outlook
Employees commonly use Outlook mailbox in the office but some use the Outlook for the web version when accessing email outside the office. If not careful, they may mistakenly attempt to log in to a phishing page designed to look like Outlook’s login page.

Figure 3. Fake login page of Outlook for the web
Many employees are accessing files and collaborating online through Office 365. Sites associated with this are also spoofed and used as phishing campaign lures. The 2019 Cloud App Security Report also found that the number of unique Office 365-related phishing links blocked in 2019 jumped to more than double 2018’s total, according to data from the Trend Micro Smart Protection Network infrastructure. We also found that these threats not only targeted users, but also those who have administrator accounts.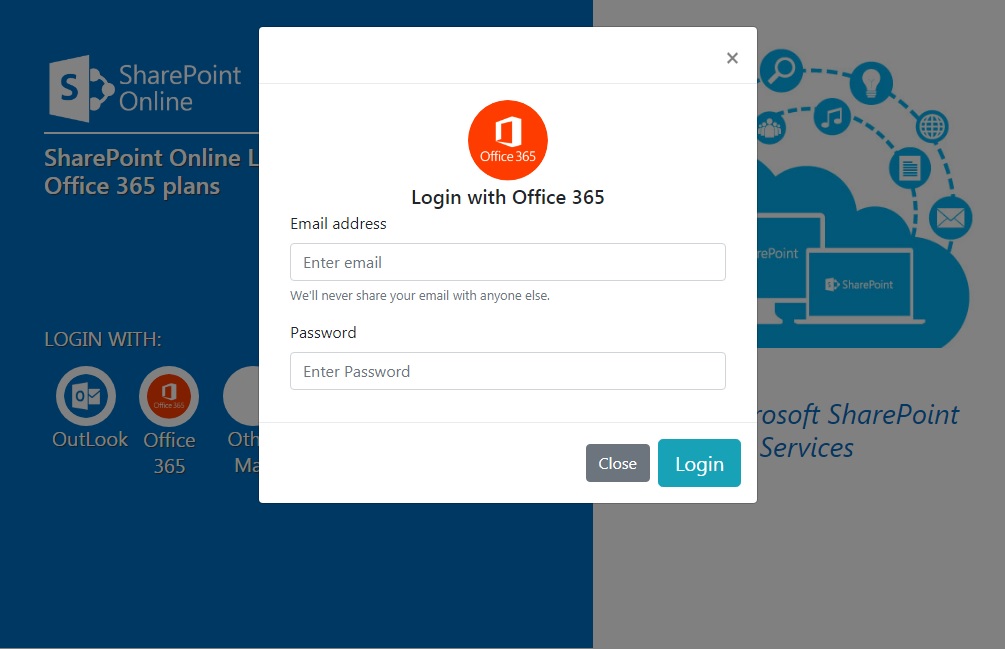
Figure 4. Fake Microsoft login page
Phishing campaigns and other threats using WebEx and Zoom as lure
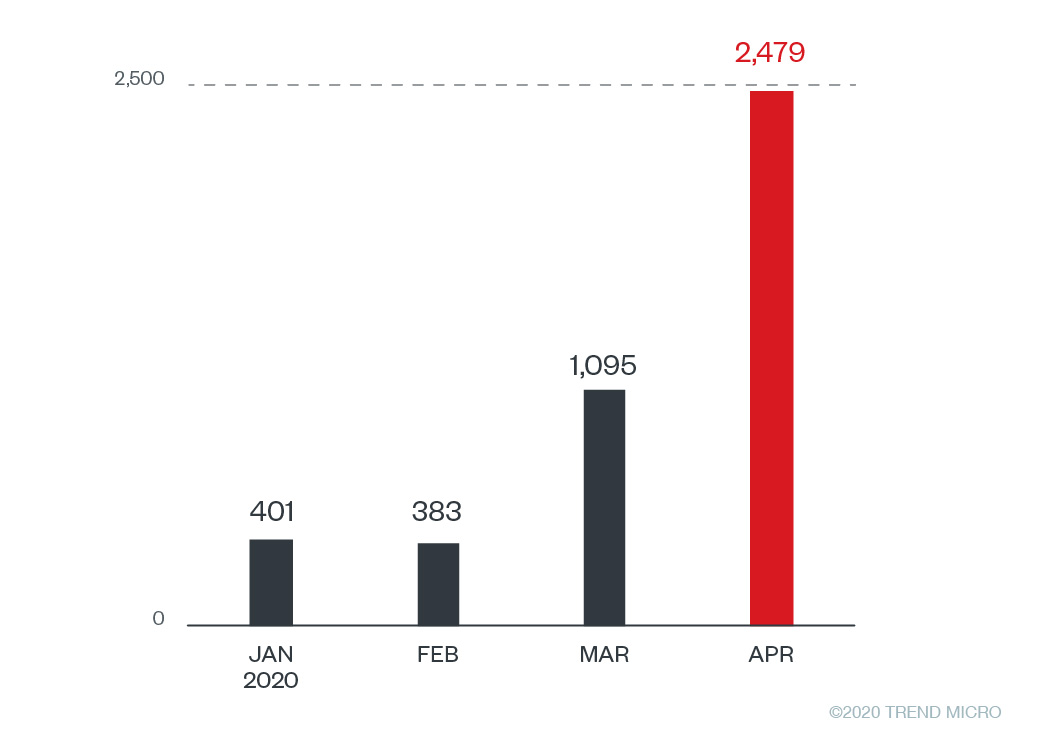
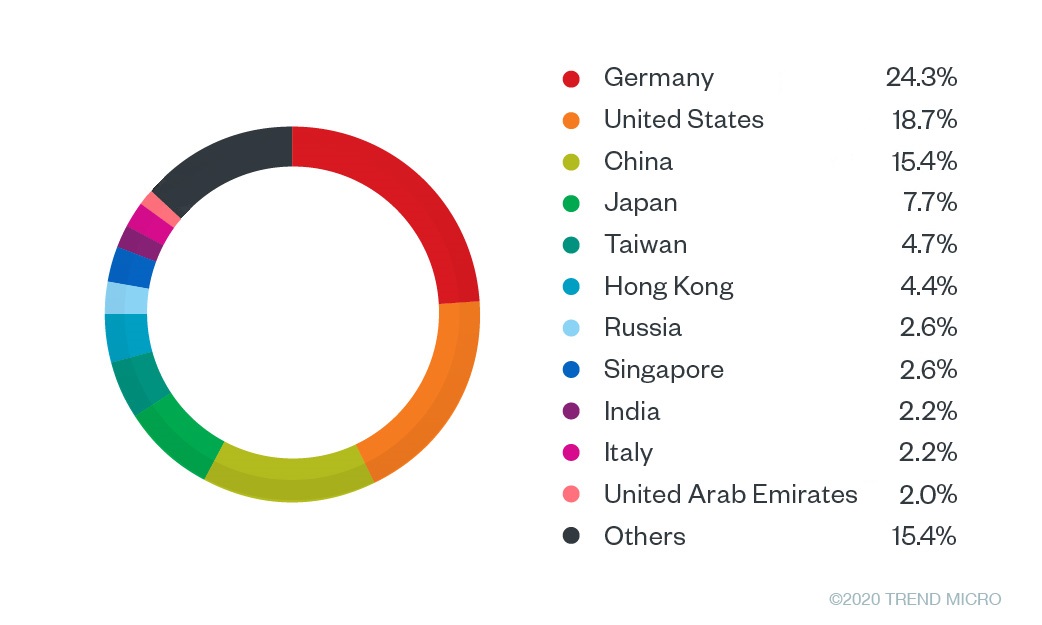
Figure 6. Top countries with users encountering phishing attempts and other threats related to Zoom and WebEx

Figure 8. Spoofed login page of Zoom
Threat actors either compromise legitimate sites or create malicious domains to host phishing pages. We traced the IP hosting locations of the sources of these domains and found that the United States has the highest unique IP count, with at 833. Trailing far behind is the Netherlands at 78 and Germany at 44.
Recommendations
- Never click links in emails coming from untrustworthy sources.
- Examine URLs embedded in emails by hovering the mouse pointer over it. This may reveal that it leads to another URL.
- Check for grammatical errors and spelling mistakes, which are common indicators that the email did not come from reputable companies.
- Even if a page looks like a legitimate login page, inspect the URL to confirm its legitimacy.
- Avoid sharing sensitive personal information online.
Indicators of Compromise
Phishing pages targeting Office365 and Outlook on the web users
- 0utlook-owa.eu-gb.cf[.]appdomain[.]cloud
- alfazos.linkpc[.]net.
- authe1-microsoftmailaccounts[.]ml
- comeliveonvacation[.]com/outlook/
- covid939[.]com
- eronginshop[.]com/owa/
- helpdeskowa[.]at[.]ua
- kitchoan.co[.]th/.owa/
- mailboxfull[.]website
- micosfotsharepoint[.]xyz
- microsharepont[.]cf
- microsharepont[.]tk
- my.sharepoint.lee.elegance[.]bg
- office365[.]it.support[.]emailblox[.]com
- outlook.winmail01[.]cn
- web-outlooks[.]com
- wwedvm[.]appspot[.]com/outlook/
Phishing pages targeting WebEx and Zoom users
- crag-group[.]com/zoom/
- darenthvaley[.]co[.]uk/zoom/index.html
- globalpagee-prod-webex[.]com
- globalpagee-prod-webex[.]com
- global-prod-meetsolutions[.]com
- webexhost[.]191078[.]ru
- zoom-appointment.myftp[.]org
Download sites of fake WebEx and Zoom apps
- d11udsutejoxdq.cloudfront.net/{redacted}/zoom-us-zoom_2544611106.exe
- d36rrippt2k8a8[.]cloudfront[.]net/{redacted}/cisco-webex-meetings[.]exe
- dlnow[.]co/cisco-webex-meetings
- zoom-download[.]com
- zoom-us-zoom[.]dlnow[.]co
Other malicious sites related to WebEx and Zoom
- cccconferzoom[.]com
- ccconferzoom[.]org
- meeting-zoom[.]hopto[.]org
- suppot-webex-cisco[.]com
- videoconferencestore[.]com
- zoomcloud[.]xyz
- zoomeetup[.]com
- zoomvirtualbackgrouns[.]com
| SHA-256 | Trend Micro Pattern Detection |
| 2e3fc390e6b74d86e3535cd2cc0fd864c8cae0b9434cce12063a289d03e7ba10 |
PUA.Win32.InstallCore.THCCABO
|
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks