Bredolab and FAKEAV Variants spreading via Spam Email Messages
How do users get this Web threat?
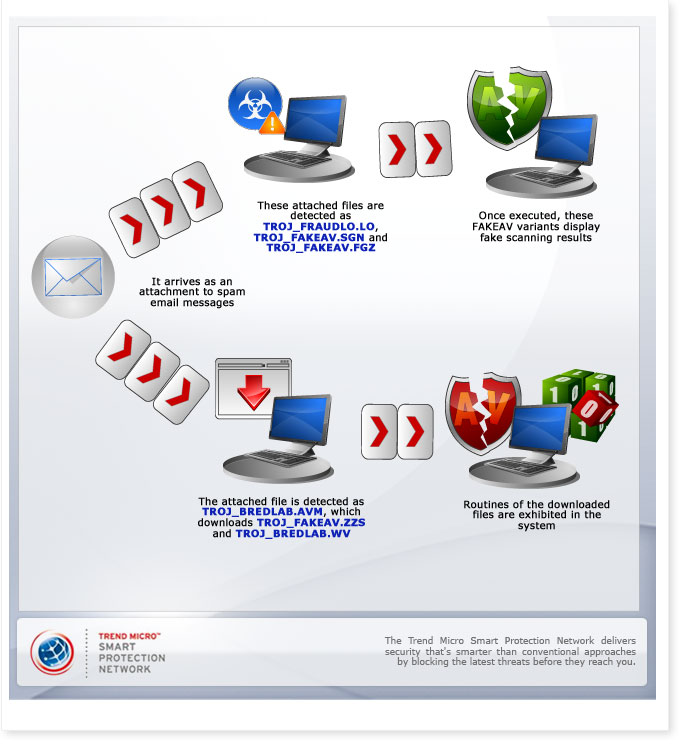
This threat arrives as an attachment to certain spam messages. TrendLabs has received different variations of these messages, including one that claims to be from Social Security, informing recipients that there were errors in their Social Security statement. Other versions include a puzzle, a wedding invitation, and a work resume.
What happens once it gets into a user's system?
Users are tricked into downloading these attachments, which are actually malicious files.
In some samples of these messages, the attached files are detected as TROJ_FRAUDLO.LO, TROJ_FAKEAV.SGN, and TROJ_FAKEAV.FGZ. These are FAKEAV variants, which are known to display fake scanning results in the affected system to persuade users into buying a rogue antivirus (AV) product. In the case of TROJ_FRAUDLO.LO, it also disables Task Manager, connects to a malicious URL and downloads its component files. Both TROJ_FAKEAV.SGN and TROJ_FAKEAV.FGZ connects to specific sites and downloads their respective component files.
TrendLabs has also received another set of these messages with attached files detected as TROJ_BREDLAB.AVM, which downloads other files onto the affected system. These downloaded files are detected as TROJ_FAKEAV.ZZS, which displays fake alerts to users and TROJ_BREDOLAB.WV, which adds a registry entry for it to run automatically every time users reboot their systems.
How are users affected by this threat?
For users who download the attached files, which are actually FAKEAV variants, they are tricked into purchasing a rogue antivirus product. Since buying these products typically requires users to provide account information, they also become victims of information theft.
On the other hand, systems infected by TROJ_BREDLAB.AVM become host to other malicious files which exhibit their respective routines on the affected system.
What is noteworthy about this threat?
This attack was tagged as noteworthy because of the increased volume of the related spam messages between July and August 2010. These messages were observed to deliver malicious attachments to users.
Are Trend Micro users affected by this threat?
Trend Micro users are protected from this thrat via Smart Protection Network, which secures users from the different components of this attack. With its Email Repuration Services, spam messages related to this attack are immediately blocked, preventing these from even reaching users' inboxes. For files detected as TROJ_FRAUDLO.LO, TROJ_FAKEAV.SGN, TROJ_FAKEAV.FGZ, TROJ_BREDLAB.AVM, TROJ_FAKEAV.ZZS and TROJ_BREDOLAB.WV, the File Repuration Service instantly detects and deletes these when found on the system.
What can users do to prevent this threat?
This threat can be easily prevented, especially if users refrain from opening and downloading attachments from dubious-looking email messages. If possible, delete messages from untrusted or unknown senders immediately from your inboxes and trash folders.