PIXSTEAL and PASSTEAL Sport New Ways To Steal Data
December 03, 2012
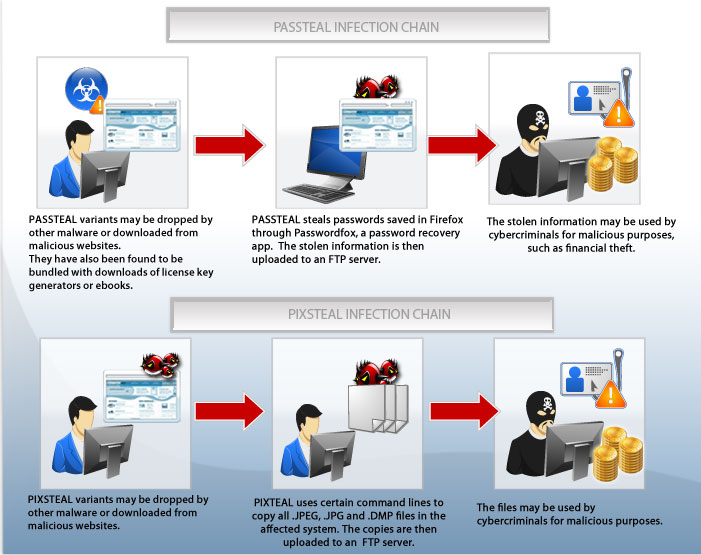
At the tail end of 2012, Trend Micro researchers received two malware samples that stole personal information in ways never seen before. TSPY_PASSTEAL.A steals passwords from browsers through a password recovery app while TSPY_PIXSTEAL.A copies all system image files and uploads them to an FTP server.
These information theft routines can only mean that cybercriminals are getting bolder with their creations. This poses a challenge for the security industry and end users alike.
How do PASSTEAL and PIXSTEAL enter systems?
PASSTEAL and PIXSTEAL arrive on systems as files dropped by malware, or unknowingly downloaded by users when visiting malicious sites.
PASSTEAL variants in particular have already infected more than 400 systems.
The malware was also noted to be planted in file-sharing websites, passed off as license key generators for software or bundled in an archive file alongside similar illegal software.
Other PASSTEAL variants were found passed off as e-book downloads of popular Young Adult (YA) novels.
What happens if I get infected with PASSTEAL/PIXSTEAL?
Computers infected by either the PASSTEAL or PIXSTEAL malware risk having compromised online accounts and losing stored personal information. Users may be in danger of financial loss, identity theft and reputation compromise.
PIXSTEAL infection may also cause the victim’s stolen images to be used for malicious purposes, such as being uploaded on pornographic websites or used for identity fraud/theft. The stolen images may also be used for blackmail and a potential cause of embarrassment for the victim.
How does PASSTEAL and PIXTEAL steal data? How are these routines different from the usual data-stealing routines?
Both PASSTEAL and PIXSTEAL’s information theft routines are different from the usual strain of information-stealing malware. Most malware usually resort to keylogging or page-spoofing in order to steal personal information, as is in the case of ZeuS and SpyEye.
TSPY_PASSTEAL.A steals information by using a password recovery app, Passwordfox, to extract saved login information from the internet browser Firefox. Once extracted, the information is saved into an .XML file through the use of the /sxml command line switch. The .XML file is used to create a .TXT file, which the malware then uploads to a File Transfer Protocol (FTP) server for storage.
TSPY_PIXSTEAL.A on the other hand steals information by running a hidden command line and copying all .JPG, .JPEG, and .DMP files on the affected system. .JPG and .JPEG files are the most common type of image files, while .DMP files are memory dump files that contain information on a system that stops unexpectedly.
Once the copying process is complete, the malware connects to an FTP server and uploads the first 20,000 files.
Why is PASSTEAL/PIXSTEAL dangerous?
Certain variants of PASSTEAL have been detected to steal information not only from other browsers besides Firefox, but also in other applications such as Steam and JDownloader.
PASSTEAL has also been noted to be able to perform this routine even when the user only logs onto websites that use secure connections (such as HTTPS or SSL). This makes PASSTEAL doubly dangerous.
PIXSTEAL can be considered a very dangerous threat since it has the potential to ruin someone’s online reputation by having their private photos posted on the Internet.
How do I know if I’m infected with PASSTEAL/PIXSTEAL?
To check whether or not you are infected with either of these malware, users can do the following:
For PASSTEAL:
- Run a search for a folder in your C:\ drive named “Documents”. It should contain an .XML file which contains a list of your passwords.
For PIXSTEAL:
- Run a search for .JPEG or .JPG files on your entire system. You should find copies of your existing images (no matter where they were originally stored) in the C:\ directory.
Users can further verify if they are indeed infected by running an antivirus scan.
My computer is infected. What do I do?
Running a Trend Micro solution on your infected computer will remove the PASSTEAL and/or PIXSTEAL malware. Trend Micro product users are protected from PIXSTEAL, PASSTEAL and their variants with the aid of the Trend Micro™ Smart Protection Network™. Trend Micro solutions PASSTEAL/PIXSTEAL infections. They also block access to sites that host the malware.
What can I do to avoid being infected by PASSTEAL and PIXSTEAL?
Users are advised not to indulge in activities that may expose them to malware. These activities include searching for and/or downloading illegal files such as pirated software, pirated e-books and license key generators. Cybercriminals have been known to pack malware such as PIXSTEAL and PASSTEAL with these files.
Users should also consider disabling the ‘save password’ function of their browsers, or clear any cookies/cache after every login session. This eliminates any chances of malware such as PASSTEAL from stealing login information from the browser. Use safe password practices, such as changing your passwords regularly or not relying on password saving functions found in browsers.
A password manager, such as Trend Micro™ DirectPass™, can also help protect against unwanted breaches that PASSTEAL can inflict.
For more tips on account and password safety, you can check out our e-guide here.
Expert Insights:
“Securing data — including files such as images — is every user’s responsibility. Part of that responsibility, of course, is to prevent being infected by malware.” – Raymart Paraiso, Threat Response Engineer