TrojanSpy.Win64.GARYSTEAL.A
UDS:Trojan.Win64.Agent.a (KASPERSKY); Trojan:Win64/GaryStealer.A!MTB (MICROSOFT)
Windows


Threat Type: Trojan Spy
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Trojan Spy arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It executes commands from a remote malicious user, effectively compromising the affected system.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Trojan Spy arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
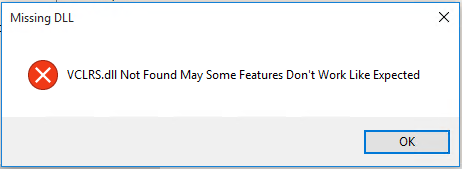
This Trojan Spy displays the following fake error messages:
Backdoor Routine
This Trojan Spy executes the following commands from a remote malicious user:
- Create startup persistence
- Perform stealer capabilities
- Execute arbitrary commands
- Display alert messages
- Retrieve running processes
- Execute files on disk or in memory
- Access and write to the clipboard
- Perform a random task
- Download and execute additional payloads
- Terminate itself
- Delete itself
It connects to the following URL(s) to send and receive commands from a remote malicious user:
- {BLOCKED}.ngrok.io:18560
Information Theft
This Trojan Spy gathers the following data:
- Host information
- Access privilege level
- OS information
- Network information
- Browser data
- Cryptocurrency wallet data
Other Details
This Trojan Spy connects to the following website to send and receive information:
- {BLOCKED}.ngrok.io:18560
It does the following:
- It sends an HTTP GET request to the following URL as a build validator:
- http://{BLOCKED}grok.io:18560/api/v1/bulla/?id=cln0hnnun0000rxwn99y3ueza&data={Encrypted Unix Time}
- It checks if the following virtual machine- or sandbox-related MAC addresses are present in the affected system:
- 00:1C:42
- 08:00:27
- 00:05:69
- 00:0C:29
- 00:1C:14
- 00:50:56
- 00:16:E3
- It performs random tasks once it detects virtual machine- or sandbox-related indicators are present in the affected machine:
- Send a ping to google.com:80
- Create a config file: %User Profile%\config.ini
- List files found on the %User Profile% directory
- List local IP addresses
- Send an HTTP GET request to https://www.web3api.com
- Print a random number
- Create a randomly named folder: %User Profile%\{Random Characters}.txt
- Print a random string
It checks if the following virtual machine- or sandbox-related registry keys are present in the affected system:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Hyper-V
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
VirtualMachine
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Virtual Machine\Guest\Parameters
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmicheartbeat
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmicvss
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmicshutdown
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmicexchange
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\PCI\VEN_1AB8*
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\PCI\VEN_80EE*
HKEY_LOCAL_MACHINE\HARDWARE\ACPI\
DSDT\VBOX__
HKEY_LOCAL_MACHINE\HARDWARE\ACPI\
FADT\VBOX__
HKEY_LOCAL_MACHINE\HARDWARE\ACPI\
RSDT\VBOX__
HKEY_LOCAL_MACHINE\SOFTWARE\Oracle\
VirtualBox Guest Additions
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\VBoxGuest
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\VBoxMouse
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\VBoxService
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\VBoxSF
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\VBoxVideo
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\PCI\VEN_5333*
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vpcbus
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vpc-s3
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vpcuhub
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\msvmmouf
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\PCI\VEN_15AD*
HKEY_CURRENT_USER\SOFTWARE\VMware, Inc.\
VMware Tools
HKEY_LOCAL_MACHINE\SOFTWARE\VMware, Inc.\
VMware Tools
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmdebug
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmmouse
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\VMTools
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\VMMEMCTL
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmware
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmci
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\vmx86
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\IDE\CdRomNECVMWar_VMware_IDE_CD*
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\IDE\CdRomNECVMWar_VMware_SATA_CD*
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\IDE\DiskVMware_Virtual_IDE_Hard_Drive*
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Enum\IDE\DiskVMware_Virtual_SATA_Hard_Drive*
HKEY_LOCAL_MACHINE\HARDWARE\ACPI\
DSDT\xen
HKEY_LOCAL_MACHINE\HARDWARE\ACPI\
FADT\xen
HKEY_LOCAL_MACHINE\HARDWARE\ACPI\
RSDT\xen
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\xenevtchn
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\xennet
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\xennet6
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\xensvc
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\xenvdb
It checks if the following virtual machine- or sandbox-related registry entries are present in the affected system:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion
ProductID = 76487-337-8429955-22614
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion
ProductID = 76487-337-8429955-22614
HKEY_LOCAL_MACHINE\HARDWARE\DEVICEMAP\
Scsi\Scsi Port 0\Scsi Bus 0\
Target Id 0\Logical Unit Id 0
Identifier = QEMU
HKEY_LOCAL_MACHINE\HARDWARE\Description\
System
SystemBiosVersion = QEMU
HKEY_LOCAL_MACHINE\HARDWARE\Description\
System
VideoBiosVersion = QEMU
HKEY_LOCAL_MACHINE\HARDWARE\Description\
System\BIOS
SystemManufacturer = VBOX
HKEY_LOCAL_MACHINE\HARDWARE\DEVICEMAP\
Scsi\Scsi Port 0\Scsi Bus 0\
Target Id 0\Logical Unit Id 0
Identifier = VBOX
HKEY_LOCAL_MACHINE\HARDWARE\DEVICEMAP\
Scsi\Scsi Port 1\Scsi Bus 0\
Target Id 0\Logical Unit Id 0
Identifier = VBOX
HKEY_LOCAL_MACHINE\HARDWARE\DEVICEMAP\
Scsi\Scsi Port 2\Scsi Bus 0\
Target Id 0\Logical Unit Id 0
Identifier = VBOX
HKEY_LOCAL_MACHINE\HARDWARE\Description\
System
SystemBiosVersion = VBOX
HKEY_LOCAL_MACHINE\HARDWARE\Description\
System
VideoBiosVersion = VIRTUALBOX
HKEY_LOCAL_MACHINE\HARDWARE\Description\
System\BIOS
SystemProductName = VIRTUAL
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\Disk\Enum
DeviceDesc = VBOX
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Services\Disk\Enum
FriendlyName = VBOX
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\
Services\Disk\Enum
DeviceDesc = VBOX
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\
Services\Disk\Enum
FriendlyName = VBOX
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\
Services\Disk\Enum
DeviceDesc = VBOX
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\
Services\Disk\Enum
FriendlyName = VBOX
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Control\SystemInformation
SystemProductName = VIRTUAL
It checks if the following virtual machine or sandbox related folder(s) or file(s) is present in the affected system:
- %System Root%\take_screenshot.ps1
- %System Root%\loaddll.exe
- %System Root%\symbols\aagmmc.pdb
- %System%\drivers\prleth.sys
- %System%\drivers\prlfs.sys
- %System%\drivers\prlmouse.sys
- %System%\drivers\prlvideo.sys
- %System%\drivers\prltime.sys
- %System%\drivers\prl_pv32.sys
- %System%\drivers\prl_paravirt_32.sys
- %System%\drivers\VBoxMouse.sys
- %System%\drivers\VBoxGuest.sys
- %System%\drivers\VBoxSF.sys
- %System%\drivers\VBoxVideo.sys
- %System%\vboxdisp.dll
- %System%\vboxhook.dll
- %System%\vboxmrxnp.dll
- %System%\vboxogl.dll
- %System%\vboxoglarrayspu.dll
- %System%\vboxoglcrutil.dll
- %System%\vboxoglerrorspu.dll
- %System%\vboxoglfeedbackspu.dll
- %System%\vboxoglpackspu.dll
- %System%\vboxoglpassthroughspu.dll
- %System%\vboxservice.exe
- %System%\vboxtray.exe
- %System%\VBoxControl.exe
- %System%\drivers\vmmouse.sys
- %System%\drivers\vmnet.sys
- %System%\drivers\vmxnet.sys
- %System%\drivers\vmhgfs.sys
- %System%\drivers\vmx86.sys
- %System%\drivers\hgfs.sys
- %System%\drivers\vmsrvc.sys
- %System%\drivers\vpc-s3.sys
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
SOLUTION
Step 1
Trend Micro Predictive Machine Learning detects and blocks malware at the first sign of its existence, before it executes on your system. When enabled, your Trend Micro product detects this malware under the following machine learning name:
-
Troj.Win32.TRX.XXPE50FFF076
Step 2
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 3
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 4
Search and delete files detected as TrojanSpy.Win64.GARYSTEAL.A
- %User Profile%\config.ini
Step 5
Search and delete these folders
- %User Profile%\{Random Characters}.txt
Step 6
Scan your computer with your Trend Micro product to delete files detected as TrojanSpy.Win64.GARYSTEAL.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.



