BKDR_TDSS.KARU
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Backdoor
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
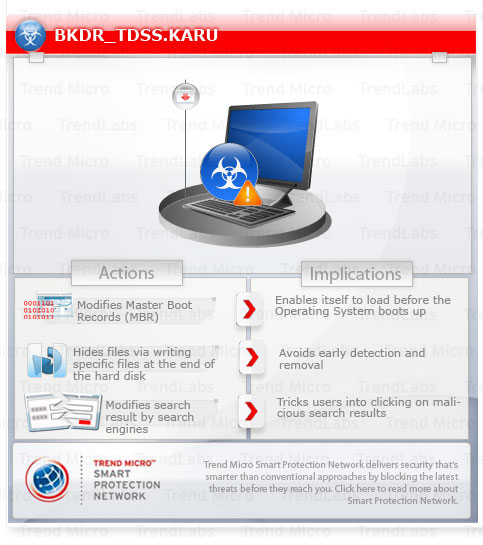
This backdoor is noteworthy as this is a new TDSS TDL4 malware that modifies the Master Boot Record and monitors the browsing activities of the user. It may also download other malicious files further compromising the affected system.
To get a one-glance comprehensive view of the behavior of this Backdoor, refer to the Threat Diagram shown below.
This backdoor adds mutexes to ensure that only one of its copies runs at any one time.
It monitors the browsing habits of the user and send the information to specific URLs when certain strings are found in the Web address.
It also modify the search results returned by search engine to trick users into clicking malicious links, and/or displaying advertisements.
It modifies the Master Boot Record (MBR) of the affected system to enable itself to load before the Operating System boots up.
It also connects to certain URLs to download other malicious files, and display advertisement.
This backdoor may be downloaded by other malware/grayware from remote sites.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
143,360 bytes
DLL
06 Apr 2011
Downloads files, Drops files, Creates mutexes, Modifies Master Boot Record (MBR)
Arrival Details
This backdoor may be downloaded by the following malware/grayware from remote sites:
- WORM_OTORUN.ASH
It may be downloaded from the following remote site(s):
- http://{BLOCKED}.112.139/service/scripts/files/aff_{parameter}.dll
Installation
This backdoor adds the following mutexes to ensure that only one of its copies runs at any one time:
- Global\3006345f-6baf-4669-a7e1-aaa310564be9
- Global\9e6af8f3-75f3-4b67-877a-c80125d7bc08
- Global\a68d7de8-eba6-4a54-90e0-9cb9d93b3ed7
- Global\cc51461b-e32a-4883-8e97-e0706dc65415
- Global\452fefe0-a06e-400f-8d6b-6a12a0a09d4b
- Creates the mutex Global\9e6af8f3-75f3-4b67-877a-c80125d7bc08 if the path of the executable file does not contain any of the following strings:
- explo
- firefox
- chrome
- opera
- safari
- netsc
- avant
- browser
- mozill
- wuauclt
Other System Modifications
This backdoor adds the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\
Internet Explorer\main\FeatureControl\
FEATURE_BROWSER_EMULATION
{executable name} = "8888"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings
maxhttpredirects = "8888"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings
enablehttp1_1 = "1"
It modifies the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings\
zones\3
1601 = "0"
(Note: The default value data of the said registry entry is 1.)
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings\
zones\3
1400 = "0"
(Note: The default value data of the said registry entry is {user-defined} .)
HKEY_USERS\.DEFAULT\Software\
Microsoft\Internet Explorer\International
acceptlanguage = "{local}"
(Note: The default value data of the said registry entry is {user defined}.)
Other Details
This backdoor connects to the following website to send and receive information:
- https://{BLOCKED}mak01.com/
- https://{BLOCKED}agcla.com/
- https://{BLOCKED}akq8x.com/
- http://{BLOCKED}1come.com/
- http://{BLOCKED}otcom.com/
- http://{BLOCKED}1kf-a.com/
- http://{BLOCKED}apcell.com/
- http://{BLOCKED}-acom.com/
- https://{BLOCKED}anno.com/
- https://{BLOCKED}im1.com/
- https://{BLOCKED}i71.com/
- https://{BLOCKED}ka.in/
- https://{BLOCKED}b6.com/
- http://{BLOCKED}cho.com/
- http://{BLOCKED}yt0.com/
- http://{BLOCKED}o81.com/
- http://{BLOCKED}o81.com/
- http://{BLOCKED}uke.com/
- http://{BLOCKED}i813ck.com/
- http://{BLOCKED}ckl1i1i.com/
- http://{BLOCKED}.193.171/
- http://{BLOCKED}.193.138/xxxx_{random number}/
It does the following:
- Monitors the browsing habits of the user and send the information to the mentioned URLs when the following strings are found in the Web address. It can also modify the search results returned by search engine to trick users into clicking malicious links, and/or displaying advertisements:
- .aol.
- .lycos.
- .search.com
- 2mdn.net
- 66.235.120.66
- 66.235.120.67
- abmr.net
- about.com
- adbureau.net
- adrevolver.com
- alexa.com
- alltheinternet.com
- alltheweb.com
- altavista.com
- aolcdn.com
- ask.com
- atdmt.com
- bing.
- blinkx.com
- compete.com
- conduit.com
- cuil.com
- dogpile.com
- doubleclick.net
- edgesuite.net
- entireweb.com
- everesttech.net
- exalead.com
- excite.com
- firmserve.com
- gigablast.com
- gstatic.com
- infospace.com
- ivwbox.
- iwon.com
- live.com
- lygo.com
- mamma.com
- metacrawler.com
- msn.com
- mytalkingbuddy.com
- othersonline.com
- powerset.net
- scorecardresearch.com
- superpages.com
- tribalfusion.com
- virtualearth.net
- wazizu.com
- webcrawler.com
- worthathousandwords.com
- yahoo
- yieldmanager.com
- yimg.com
- ytimg.com
- Modifies the Master Boot Record (MBR) of the affected system to enable itself to load before the Operating System boots up.
- Writes the following files at the end of the hard disk to hide its component files:
- \?\globalroot\{random}\cfg.ini - Contains the configuration for the BOT functionality of the malware.
- \?\globalroot\{random}\bckfg.tmp - backup copy of the configuration file.
- \?\globalroot\{random}\mbr - this is the code written in the Master Boot Record and executes ldr16.
- \?\globalroot\{random}\ldr16 - component loaded by the malware during OS boot-up. This is resposible for executing ldr32 or ldr64 depending on the Operating System.
- \?\globalroot\{random}\ldr32 - TROJ_TDSS.KARUL, Used by the malware to let the OS continue to boot without crashing by replicating the system library kdcom.dll.
- \?\globalroot\{random}\ldr64 - TROJ_TDSS.KARUL, Used by the malware to let the OS continue boot without crashing by replicating the system library kdcom.dll.
- \?\globalroot\{random}\drv32 - RTKT_TDSS.KARUD, Component used by the malware to hide itself and ensure the MBR is infected.
- \?\globalroot\{random}\drv64 - RTKT_TDSS.KARUD, Component used by the malware to hide itself and ensure the MBR is infected.
- \?\globalroot\{random}\cmd.dll - Also detected as BKDR_TDSS.KARU
- \?\globalroot\{random}\cmd64.dll - Also detected as BKDR_TDSS.KARU
- Connects to the above-mentioned URLs to download other malicious files, and display advertisement.
SOLUTION
8.900
7.956.08
07 Apr 2011
7.957.00
07 Apr 2011
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 4
Restore your system’s Master Boot Record (MBR)
To restore your system's Master Boot Record (MBR):
- Insert your Windows Installation CD into your CD-ROM drive or the USB flash drive then restart your computer.
- Press the restart button of your computer.
- When prompted, press any key to boot from the CD.
- When prompted on the Main Menu, type r to enter the Recovery Console.
(For Windows 2000 users: After pressing r, type c to choose the Recovery Console on the repair options screen.) - When prompted, type your administrator password to log in.
- Once logged in, type the drive that contains Windows in the command prompt that appears, and then press Enter.
- Type the following then press Enter:
fixmbr {affected drive}
(Note: The affected drive is the bootable drive that this malware/grayware has affected. If no device is specified, the MBR will be written in the primary boot drive.) - Type exit to restart the system.
Step 5
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\main\FeatureControl\FEATURE_BROWSER_EMULATION
- {executable name} = "8888"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
- maxhttpredirects = "8888"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
- enablehttp1_1 = "1"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\zones\3
- currentlevel = "0"
Step 6
Restore this modified registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\zones\3
- From: 1601 = "0"
To: 1601 = "1"
- From: 1601 = "0"
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\zones\3
- From: 1400 = "0"
To: 1400 = "{user-defined}"
- From: 1400 = "0"
- In HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Explorer\International
- From: acceptlanguage = "{local}"
To: acceptlanguage = "{user defined}"
- From: acceptlanguage = "{local}"
Step 7
Scan your computer with your Trend Micro product to delete files detected as BKDR_TDSS.KARU. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.

