Social Engineering Facilitates Tax Season Malware Attacks
March 04, 2011
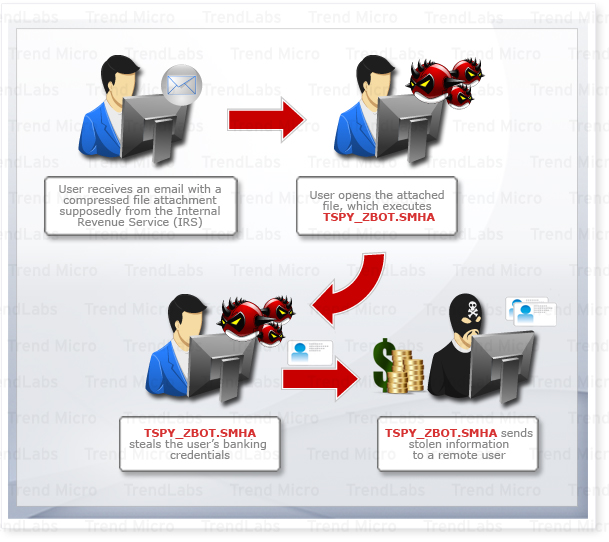
January is when most countries kick off the tax season, which makes it a favorite cybercriminal target to make money. Thanks to social engineering, a popular tactic wherein an attack is tailored to coincide with widely celebrated occasions, observed holidays, and popular news, cybercriminals earn a lot from their victims. This tax season is no different, as we received spam samples that attempted to pass themselves off as a message from the U.S. Internal Revenue Service (IRS).
The spam bears the subject "IRS Notification—Fiscal Activity ID #7 numbers" and comes with a .ZIP file attachment. It entices the recipient to open the attachment and to print the .DOC file that it contains. In reality, the file contains a malware detected as TSPY_ZBOT.SMHA that is capable of stealing the user's banking credentials.
Like other ZBOT variants, TSPY_ZBOT.SMHA detects whenever an affected user accesses target online banking sites for which it steals information like personal identification numbers (PINs), account numbers, and the like.
This is not the first attack that took advantage of the tax season. In fact, on April 22, 2009, we posted a blog entry on IRS scams that coincided with the deadline for filing tax returns in the United States. This run featured the FORM W-8BEN, an edited copy of the certificate that the recipient should complete and submit. Unlike the original form, this asked the recipient to give out additional information like bank account numbers and PINs.
A similar attack ensued on June 19 of the same year. In this run, Australians received spam that supposedly came from the Australian Taxation Office (ATO). It asks recipients to print, fill in, and send the attached file via email to the office so they can become eligible for tax returns. This was, of course, a phishing scam. Printing the file triggered the sending of users’ personal information to a remote user.
Apart from ZeuS, there is yet another malware family that users should take notice of: SpyEye, a family of malware that has similar functions to that of ZeuS, but has some extra features that make it just as formidable and alarming. Once dubbed as the 'ZeuS Killer', the first variants actually uninstalled or deleted ZeuS variants from an affected system should it detect them before executing its malicious routines. It uses and hooks APIs in the affected system in order to hide itself from detection, as well as offered cybercriminals an easy-to-use user interface which made information and financial theft more accessible to even nontechnical users.
This rivalry between ZeuS and SpyEye turned into something more malicious for users as the creators of both malware decided to merge into one cybercriminal entity, thus creating a hybrid that was specifically tailored to steal banking information quickly, efficiently and silently. TSPY_SPYEYE.CE is an example of the merger, sporting features from both ZeuS and SpyEye, able to connect and download its latest upgraded version as well as various components to make it more efficient and invisible in a system. Taxpayers should exercise more caution due to this merger's existence.
Tax season is still a hit among cybercriminals as it continues to be used in social engineering email seen in 2013 and 2014. Apart from the US and Australia, UK is also targeted by tax-related spam. These spammed messages carry malware attachments that mostly belong to UPATRE.
How do these threats infect users' systems?
TSPY_ZBOT.SMHA may be downloaded unknowingly from malicious websites or dropped by other malware onto the systems of unsuspecting users. It may also arrive as a .ZIP file spam attachment. Like TSPY_ZBOT.SMHA, TSPY_SPYEYE.CE may be downloaded unknowingly from malicious websites or downloaded by other malware/spyware/grayware from remote sites onto the systems of unsuspecting users. Both malware have been designed to steal users’ online banking information from the systems they infect.
What happens when the threats infect a system?
TSPY_ZBOT.SMHA injects itself into processes running in memory to hide its malicious routines. It opens a random port to allow a remote user to access and execute commands on the infected system. Its core function is to steal sensitive banking information by retrieving data like personal certificates, FTP credentials, Internet session cookies, and Adobe Flash Player data from infected systems.
TSPY_SPYEYE.CE, meanwhile, injects a remote thread to running processes as soon as it is executed. It steals information and sends it to a remote user by hooking application programming interfaces (APIs). It also performs a host of other routines like updating its configuration file, downloading its latest version, logging keystrokes, and filling in form data—all to better perform its functions. It is also capable of modifying an infected system’s browser settings.
UPATRE malware, being a downloader, downloads a ZBOT/ZEUS variant. The downloaded ZBOT/ZEUS variant, in turn, downloads a Cryptolocker variant.
How do these threats affect users with their malicious routines?
Both malware steal users' online banking information and sends this to remote users for future use. The fact that these ride on the tax season increases their chances of managing to steal pertinent information due to the predictable rise in the number of online banking transactions. Users may find their bank accounts drained of money or their credit cards charged with unknown and exorbitant bills.
For computers affected by the UPATRE malware, apart from stolen information, users may have to deal with encrypted files.
How can these threats be removed from an infected system?
Affected users can remove these malware from their systems by disabling System Restore, closing all open browser windows, and scanning their systems with their registered Trend Micro product.
Are Trend Micro product users safe from these threats?
Yes, the Trend Micro™ Smart Protection Network™ protects users from these malware by preventing spam from even reaching their inboxes with email reputation technology. It also blocks user access to malicious sites via the Web reputation technology. Finally, it prevents the download and execution of malicious files onto users' systems with the aid of file reputation technology.
What can users do to prevent these threats from affecting their computers?
Users must remain vigilant against all kinds of social engineering tactics. Besides installing an effective security solution, they should also exercise caution when opening email messages or when downloading attachments from unknown senders. Since ZBOT, SPYEYE, and UPATRE malware perpetrators constantly find new ways to trick victims into giving out personal information, users are advised to always observe safe computing practices.
The spam bears the subject "IRS Notification—Fiscal Activity ID #7 numbers" and comes with a .ZIP file attachment. It entices the recipient to open the attachment and to print the .DOC file that it contains. In reality, the file contains a malware detected as TSPY_ZBOT.SMHA that is capable of stealing the user's banking credentials.
Like other ZBOT variants, TSPY_ZBOT.SMHA detects whenever an affected user accesses target online banking sites for which it steals information like personal identification numbers (PINs), account numbers, and the like.
This is not the first attack that took advantage of the tax season. In fact, on April 22, 2009, we posted a blog entry on IRS scams that coincided with the deadline for filing tax returns in the United States. This run featured the FORM W-8BEN, an edited copy of the certificate that the recipient should complete and submit. Unlike the original form, this asked the recipient to give out additional information like bank account numbers and PINs.
A similar attack ensued on June 19 of the same year. In this run, Australians received spam that supposedly came from the Australian Taxation Office (ATO). It asks recipients to print, fill in, and send the attached file via email to the office so they can become eligible for tax returns. This was, of course, a phishing scam. Printing the file triggered the sending of users’ personal information to a remote user.
Apart from ZeuS, there is yet another malware family that users should take notice of: SpyEye, a family of malware that has similar functions to that of ZeuS, but has some extra features that make it just as formidable and alarming. Once dubbed as the 'ZeuS Killer', the first variants actually uninstalled or deleted ZeuS variants from an affected system should it detect them before executing its malicious routines. It uses and hooks APIs in the affected system in order to hide itself from detection, as well as offered cybercriminals an easy-to-use user interface which made information and financial theft more accessible to even nontechnical users.
This rivalry between ZeuS and SpyEye turned into something more malicious for users as the creators of both malware decided to merge into one cybercriminal entity, thus creating a hybrid that was specifically tailored to steal banking information quickly, efficiently and silently. TSPY_SPYEYE.CE is an example of the merger, sporting features from both ZeuS and SpyEye, able to connect and download its latest upgraded version as well as various components to make it more efficient and invisible in a system. Taxpayers should exercise more caution due to this merger's existence.
Tax season is still a hit among cybercriminals as it continues to be used in social engineering email seen in 2013 and 2014. Apart from the US and Australia, UK is also targeted by tax-related spam. These spammed messages carry malware attachments that mostly belong to UPATRE.
How do these threats infect users' systems?
TSPY_ZBOT.SMHA may be downloaded unknowingly from malicious websites or dropped by other malware onto the systems of unsuspecting users. It may also arrive as a .ZIP file spam attachment. Like TSPY_ZBOT.SMHA, TSPY_SPYEYE.CE may be downloaded unknowingly from malicious websites or downloaded by other malware/spyware/grayware from remote sites onto the systems of unsuspecting users. Both malware have been designed to steal users’ online banking information from the systems they infect.
What happens when the threats infect a system?
TSPY_ZBOT.SMHA injects itself into processes running in memory to hide its malicious routines. It opens a random port to allow a remote user to access and execute commands on the infected system. Its core function is to steal sensitive banking information by retrieving data like personal certificates, FTP credentials, Internet session cookies, and Adobe Flash Player data from infected systems.
TSPY_SPYEYE.CE, meanwhile, injects a remote thread to running processes as soon as it is executed. It steals information and sends it to a remote user by hooking application programming interfaces (APIs). It also performs a host of other routines like updating its configuration file, downloading its latest version, logging keystrokes, and filling in form data—all to better perform its functions. It is also capable of modifying an infected system’s browser settings.
UPATRE malware, being a downloader, downloads a ZBOT/ZEUS variant. The downloaded ZBOT/ZEUS variant, in turn, downloads a Cryptolocker variant.
How do these threats affect users with their malicious routines?
Both malware steal users' online banking information and sends this to remote users for future use. The fact that these ride on the tax season increases their chances of managing to steal pertinent information due to the predictable rise in the number of online banking transactions. Users may find their bank accounts drained of money or their credit cards charged with unknown and exorbitant bills.
For computers affected by the UPATRE malware, apart from stolen information, users may have to deal with encrypted files.
How can these threats be removed from an infected system?
Affected users can remove these malware from their systems by disabling System Restore, closing all open browser windows, and scanning their systems with their registered Trend Micro product.
Are Trend Micro product users safe from these threats?
Yes, the Trend Micro™ Smart Protection Network™ protects users from these malware by preventing spam from even reaching their inboxes with email reputation technology. It also blocks user access to malicious sites via the Web reputation technology. Finally, it prevents the download and execution of malicious files onto users' systems with the aid of file reputation technology.
What can users do to prevent these threats from affecting their computers?
Users must remain vigilant against all kinds of social engineering tactics. Besides installing an effective security solution, they should also exercise caution when opening email messages or when downloading attachments from unknown senders. Since ZBOT, SPYEYE, and UPATRE malware perpetrators constantly find new ways to trick victims into giving out personal information, users are advised to always observe safe computing practices.