Spam with Disguised Attachments Comes with Locky
March 29, 2016
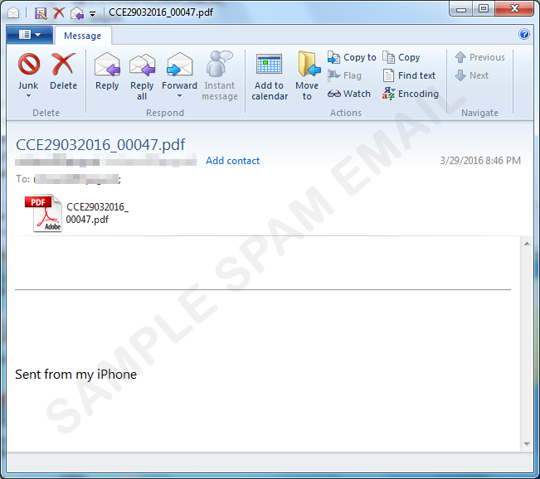
A new wave of spam that uses *.rar *.zip *.gif *.tiff *.docx *.pdf *.jpg is making its rounds.
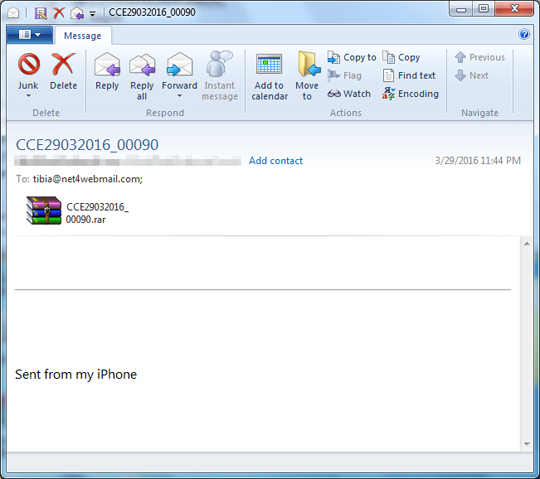
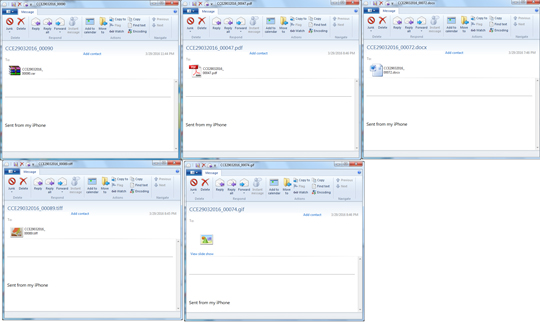
The attachment looks like it is renamed to lure recipients into clicking the attachment files. These attachments are archive files that come with a JavaScript file that drops a LOCKY malware, detected as JS_LOCKY.BQ.
It looks like this is similar to the spam wave found several days ago that also distributes Locky ransomware. See Malspam With JavaScript Attachment Leads To Locky Ransomware.
SPAM BLOCKING DATE / TIME: March 29, 2016 GMT-8
TMASE INFO
- ENGINE:8.0
- PATTERN:2228