Trojan.CVE201711882
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
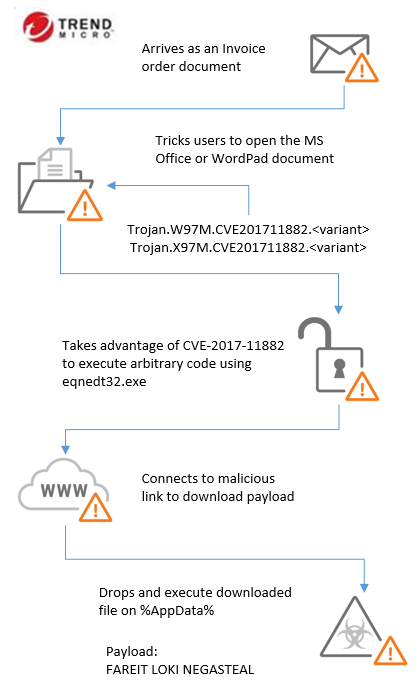
This is the detection for malware that exploit Microsoft Office Memory Corruption Vulnerability (CVE-2017-11882). This malware usually arrives via malicious spam campaigns as a weaponized Microsoft Office document. The targeted platforms are MS Office 2007, 2010, 2013, 2016, and Office 365.
CVE-2017-11882 is a remote code execution vulnerability that can enable an attacker to execute arbitrary code on the compromised machine. The vulnerability resides in an MS Office component called Equation Editor, an out-of-process COM server hosted by eqnedt32.exe, which was compiled on November 2009 and still being used in supported versions of MS Office without further recompilation. This vulnerability was patched by Microsoft on November 14, 2017. However, it’s still being actively used in attacks.
Cybercriminals using this vulnerability usually take advantage of current events in its malicious spam campaigns. This is to trick users into opening these malicious emails and clicking on its attachments. These attachments are documents such as Word, Excel, or Rich Text Format (RTF) files to leverage the vulnerability and download malware payload on the compromised machine. This vulnerability serves as a downloader for information stealer malware such as FAREIT, LOKI or NEGASTEAL.
The malware routines include:
- Downloads information stealer malware such as FAREIT, LOKI or NEGASTEAL
- Uses Equation Editor to download and execute the malware payload
It typically follows the infection chain below: