TROJ_CRYPWALL
Windows


Threat Type: Trojan
Destructiveness: Yes
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan adds the following folders:
- %System Root%\{7 characters from UID}
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.)
It drops the following files:
- %User Startup%\DECRYPT_INSTRUCTION.TXT
- %User Startup%\DECRYPT_INSTRUCTION.HTML
- %User Startup%\INSTALL_TOR.URL
(Note: %User Startup% is the current user's Startup folder, which is usually C:\Windows\Profiles\{user name}\Start Menu\Programs\Startup on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Start Menu\Programs\Startup on Windows NT, and C:\Documents and Settings\{User name}\Start Menu\Programs\Startup.)
It drops and executes the following files:
- %Desktop%\DECRYPT_INSTRUCTION.TXT
- %Desktop%\DECRYPT_INSTRUCTION.HTML
- %Desktop%\INSTALL_TOR.URL
(Note: %Desktop% is the desktop folder, where it usually is C:\Documents and Settings\{user name}\Desktop in Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\Desktop in Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
It drops the following copies of itself into the affected system:
- %System Root%\{7 characters from UID}\{7 characters from UID}.exe
- %Application Data%\{7 characters from UID}.exe
- %User Startup%\{7 characters from UID}.exe
(Note: %System Root% is the Windows root folder, where it usually is C:\ on all Windows operating system versions.. %Application Data% is the Application Data folder, where it usually is C:\Documents and Settings\{user name}\Application Data on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\Users\{user name}\AppData\Roaming on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.. %User Startup% is the current user's Startup folder, which is usually C:\Windows\Profiles\{user name}\Start Menu\Programs\Startup on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Start Menu\Programs\Startup on Windows NT, and C:\Documents and Settings\{User name}\Start Menu\Programs\Startup.)
Autostart Technique
This Trojan adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
{7characters from UID} = "%Application Data%\{7 characters from UID}.exe"
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
{6 characters from UID} = "%System Root%\{7 characters from UID}\{7 characters from UID}.exe"
Other System Modifications
This Trojan adds the following registry keys:
HKEY_CURRENT_USER\Software\Vocal AppWizard-Generated Applications
HKEY_CURRENT_USER\Software\Vocal AppWizard-Generated Applications\
{random}
HKEY_CURRENT_USER\Software\Vocal AppWizard-Generated Applications\
{random}\Recent File List
HKEY_CURRENT_USER\Software\Vocal AppWizard-Generated Applications\
{random}\Settings
Other Details
This Trojan connects to the following website to send and receive information:
- http://www.{BLOCKED}apmak.com/{random value}
- http://www.{BLOCKED}tringen.de/wordpress/{random value}
- http://www.{BLOCKED}psphotography.co.uk/blog/{random value}
- http://www.{BLOCKED}nguild.com/{random value}
- http://www.{BLOCKED}e.be/{random value}
- http://www.{BLOCKED}-schwarzenberg.de/wp-content/themes/fdp-asz/{random value}
- http://www.{BLOCKED}ntiques.co.uk/blog/{random value}
- http://www.{BLOCKED}erburg.ch/wordpress/{random value}
- http://www.{BLOCKED}info.com/wp-content/themes/mh/{random value}
- http://www.{BLOCKED}ifesupport.com/{random value}
- http://eportfolio.{BLOCKED}man.ca/blog/{random value}
- http://www.{BLOCKED}man.com/wp-content/themes/s431_Blue/{random value}
- http://{BLOCKED}tner.cz/{random value}
- http://www.{BLOCKED}mann.de/{random value}
- http://www.{BLOCKED}rda.com/blog-trabajos/{random value}
- http://www.{BLOCKED}r.at/jesneu/wp-content/themes/Girl/{random value}
- http://www.{BLOCKED}rideal.com.br/site/{random value}
- http://www.{BLOCKED}mes.com/{random value}
It encrypts files with the following extensions:
- .pdf
- .pdf
- .pot
- .pot
- .hta
- .xlt
- .xlt
- .pps
- .pps
- .xlw
- .xlw
- .dot
- .dot
- .rtf
- .rtf
- .ppt
- .ppt
- .xls
- .xls
- .doc
- .doc
- .xml
- .xml
- .htm
- .htm
- .html
- .html
- .hta
- .zip
- .dvr-ms
- .wvx
- .wmx
- .wmv
- .wm
- .mpv2
- .mpg
- .mpeg
- .mpe
- .mpa
- .mp2v
- .mp2
- .m1v
- .IVF
- .asx
- .asf
- .wax
- .snd
- .rmi
- .m3u
- .au
- .aiff
- .aifc
- .aif
- .midi
- .mid
- .wma
- .wav
- .mp3
- .wmf
- .tiff
- .tif
- .rle
- .png
- .jpeg
- .jpe
- .jpg
- .jfif
- .ico
- .gif
- .emf
- .dib
- .bmp
NOTES:
TROJ_CRYPWALL usually drops the following files in all folders where files are encrypted:
- DECRYPT_INSTRUCTION.TXT
- DECRYPT_INSTRUCTION.HTML
- INSTALL_TOR.URL
It opens the following ransom note DECRYPT_INSTRUCTION.HTML, which it also drops:
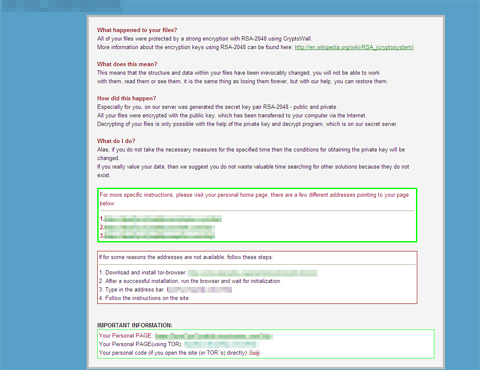
It demands payment for using decryption services:
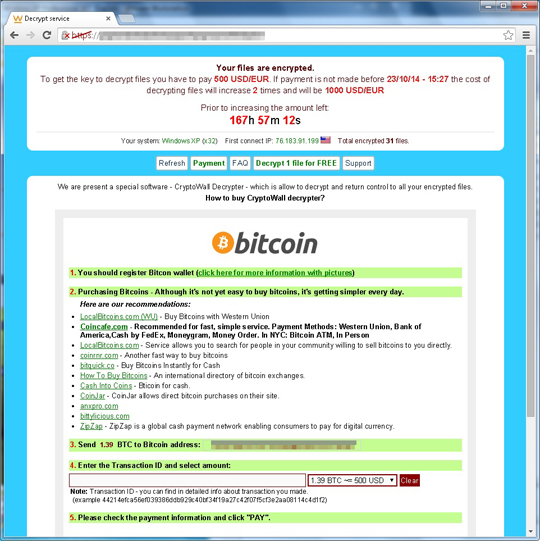
It deletes shadow copies by executing the following command:
vssadmin.exe Delete Shadows /All /Quiet


