Ransom.MSIL.EGOGEN.THEBBBC
Trojan:MSIL/XWormRAT.A!MTB (MICROSOFT)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It adds certain registry entries to disable the Task Manager. This action prevents users from terminating the malware process, which can usually be done via the Task Manager.
It terminates itself if it detects it is being run in a virtual environment.
It encrypts files with specific file extensions. It drops files as ransom note. It avoids encrypting files with the following file extensions.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following files:
- %AppDataLocal%\discord.exe
- %Application Data%\ID
- %Application Data%\fondo_antiguo.jpg → Copy of current background
- %User Profile%\Pictures\image[Random 30 characters].jpg → deleted afterwards
- %User Startup%\BXIuSsB.exe
- %User Temp%\Adobe\BXIuSsB.exe
- %User Temp%\[Random 7 characters]_dat.log
- %Application Data%\delback.bat
- %User Startup%\update.bat
(Note: %AppDataLocal% is the Local Application Data folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Application Data% is the current user's Application Data folder, which is usually C:\Documents and Settings\{user name}\Application Data on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Roaming on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %User Profile% is the current user's profile folder, which is usually C:\Documents and Settings\{user name} on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name} on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %User Startup% is the current user's Startup folder, which is usually C:\Windows\Profiles\{user name}\Start Menu\Programs\Startup on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Start Menu\Programs\Startup on Windows NT, C:\Documents and Settings\{User name}\Start Menu\Programs\Startup on Windows 2003(32-bit), XP and 2000(32-bit), or C:\Users\{user name}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit), 10(64-bit).. %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It drops and executes the following files:
- %User Startup%\1.exe
- %User Startup%\archive.exe
- %User Startup%\Xarch.exe
- %User Startup%\teleratserver.exe
(Note: %User Startup% is the current user's Startup folder, which is usually C:\Windows\Profiles\{user name}\Start Menu\Programs\Startup on Windows 98 and ME, C:\WINNT\Profiles\{user name}\Start Menu\Programs\Startup on Windows NT, C:\Documents and Settings\{User name}\Start Menu\Programs\Startup on Windows 2003(32-bit), XP and 2000(32-bit), or C:\Users\{user name}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit), 10(64-bit).)
It adds the following processes:
- %Application Data%\Read Me First!.txt
- cmd "/c @echo off & echo github: https://{BLOCKED}t.me/{BLOCKED}69 & start https://{BLOCKED}t.me/{BLOCKED}69"
- vssadmin delete shadows /all /quiet
- bcdedit.exe /set {default} recoveryenabled no
- bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
- ping -n 1 -w 5000 {BLOCKED}.{BLOCKED}.254.254
- del "%User Startup%\BXIuSsB.exe"
It creates the following folders:
- %User Temp%\Adobe → deleted after encryption
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
Autostart Technique
This Ransomware adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
1 = %User Startup%\1.exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
archive = %User Startup%\archive.exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
Xarch = %User Startup%\Xarch.exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
discord = %AppDataLocal%\discord.exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
teleratserver = %User Startup%\teleratserver.exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
BXIuSsB = %User Startup%\BXIuSsB.exe
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\RunOnce
BXIuSsB.exe = %User Temp%\Adobe\BXIuSsB.exe
Other System Modifications
This Ransomware adds the following registry entries to disable the Task Manager:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
System
DisableTaskMgr = 1
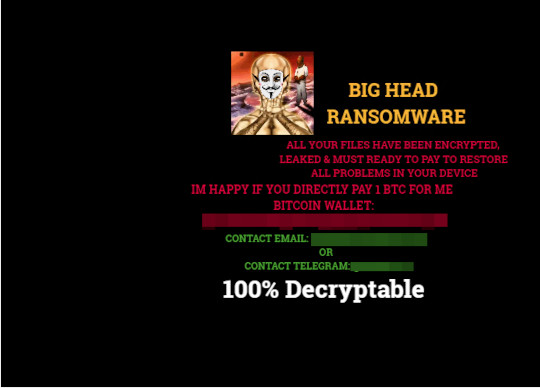
It changes the desktop wallpaper by modifying the following registry entries:
HKEY_CURRENT_USER\Control Panel\Desktop
Wallpaper = %User Profile%\Pictures\image[Random 30 characters].jpg
It sets the system's desktop wallpaper to the following image:
Process Termination
This Ransomware terminates the following processes if found running in the affected system's memory:
- taskmgr
- sqlagent
- winword
- sqlbrowser
- sqlservr
- sqlwriter
- oracle
- ocssd
- dbsnmp
- synctime
- mydesktopqos
- agntsvc.exeisqlplussvc
- xfssvccon
- mydesktopservice
- ocautoupds
- agntsvc.exeagntsvc
- agntsvc.exeencsvc
- firefoxconfig
- tbirdconfig
- ocomm
- mysqld
- sql
- mysqld-nt
- mysqld-opt
- dbeng50
- sqbcoreservice
Other Details
This Ransomware terminates itself if it detects it is being run in a virtual environment.
It does the following:
- It does not proceed with its encryption routine if one of the following conditions are met:
- Registry data under HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Disk\Enum contains the following strings:
- VBOX
- Virtual
- VMware
- Processes contain the following strings:
- VBox
- prl_
- srvc.exe
- vmtoolsd
- Registry data under HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Disk\Enum contains the following strings:
- It will drop this ransom note instead if it meets one of the following conditions:
- If the OS name contains "Serv" and System Language is one of the following:
- Arabic, Dutch, English, French, German, Italian, Korean, Portuguese, Spanish, Swedish, Bulgarian, Catalan, Czech, Danish, Greek, Estonian, Basque, Finnish, Hungarian, Japanese, Lithuanian, Norwegian, Polish, Romanian, Sami, Slovak, Slovenian, Turkish
- The number of encrypted files is greater than 5000
- Renames the encrypted files to [(Original File Name) converted to base64]
- It encrypts fixed, removable and network drives
- It terminates if the machine has the following system language:
- Russian
- Belarusian
- Ukrainian
- Kazakh
- Armenian
- Georgian
- Tatar
- Uzbek
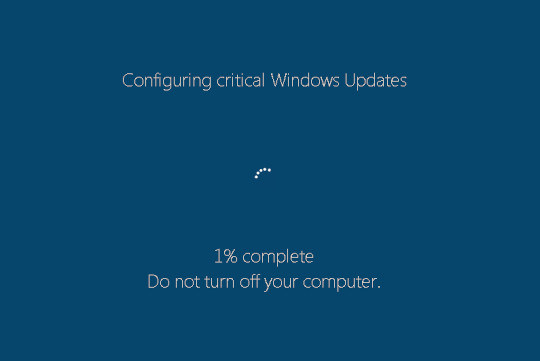
- Displays a fake Windows Update upon installation
Ransomware Routine
This Ransomware encrypts files with the following extensions:
- .r3d → if the file is in %Desktop% or its subfolders
(Note: %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It avoids encrypting files with the following strings in their file name:
- README_
It avoids encrypting files found in the following folders:
- WINDOWS
- RECYCLER
- Program Files
- Program Files (x86)
- Windows
- Recycle.Bin
- RECYCLE.BIN
- Recycler
- TEMP
- APPDATA
- AppData
- Temp
- ProgramData
- Microsoft
- Burn
It appends the following extension to the file name of the encrypted files:
- .poop → if the extension is ".r3d" and is in %Desktop% or its subdirectories
(Note: %Desktop% is the current user's desktop, which is usually C:\Documents and Settings\{User Name}\Desktop on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\Desktop on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
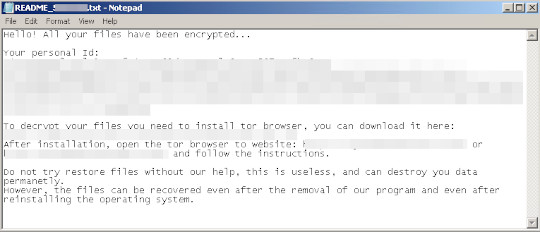
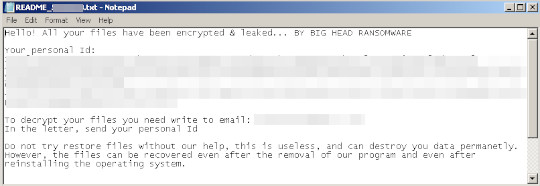
It drops the following file(s) as ransom note:
- [%Desktop% and its subdirectories]\Read Me First!.txt
- %Application Data%\Read Me First!.txt
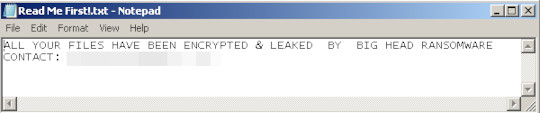
- [Drive Letter]\README_[Random 7 characters].txt
- [Encrypted Folder]\README_[Random 7 characters].txt
It avoids encrypting files with the following file extensions:
- .lnk
SOLUTION
Step 1
Trend Micro Predictive Machine Learning detects and blocks malware at the first sign of its existence, before it executes on your system. When enabled, your Trend Micro product detects this malware under the following machine learning name:
- TROJ.Win32.TRX.XXPE50FFF069
Step 2
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 3
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 4
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- 1 = %User Startup%\1.exe
- 1 = %User Startup%\1.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- archive = %User Startup%\archive.exe
- archive = %User Startup%\archive.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Xarch = %User Startup%\Xarch.exe
- Xarch = %User Startup%\Xarch.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- discord = %AppDataLocal%\discord.exe
- discord = %AppDataLocal%\discord.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- teleratserver = %User Startup%\teleratserver.exe
- teleratserver = %User Startup%\teleratserver.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- BXIuSsB = %User Startup%\BXIuSsB.exe
- BXIuSsB = %User Startup%\BXIuSsB.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- BXIuSsB.exe = %User Temp%\Adobe\BXIuSsB.exe
- BXIuSsB.exe = %User Temp%\Adobe\BXIuSsB.exe
- In HKEY_CURRENT_USER\Control Panel\Desktop
- Wallpaper = %User Profile%\Pictures\image[Random 30 characters].jpg
- Wallpaper = %User Profile%\Pictures\image[Random 30 characters].jpg
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System
- DisableTaskMgr = 1
- DisableTaskMgr = 1
Step 5
Search and delete these files
- %User Startup%\1.exe
- %User Startup%\archive.exe
- %User Startup%\Xarch.exe
- %User Startup%\teleratserver.exe
- %AppDataLocal%\discord.exe
- %Application Data%\ID
- %Application Data%\fondo_antiguo.jpg
- %User Profile%\Pictures\image[Random 30 characters].jpg
- %User Startup%\BXIuSsB.exe
- %User Temp%\Adobe\BXIuSsB.exe
- %User Temp%\[Random 7 characters]_dat.log
- %Application Data%\delback.bat
- %User Startup%\update.bat
Step 6
Search and delete this folder
- %User Temp%\Adobe
Step 7
Restore encrypted files from backup.
Step 8
Scan your computer with your Trend Micro product to delete files detected as Ransom.MSIL.EGOGEN.THEBBBC. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Step 9
Reset your Desktop properties
Did this description help? Tell us how we did.