Expl_CVE20178570
September 04, 2019
PLATFORM:
Windows
OVERALL RISK RATING:
DAMAGE POTENTIAL:
DISTRIBUTION POTENTIAL:
REPORTED INFECTION:
INFORMATION EXPOSURE:


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
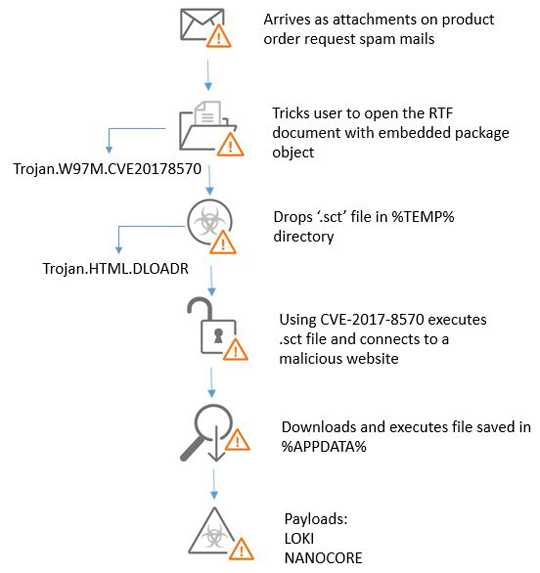
OVERVIEW
Some malicious Rich Text Format (RTF) documents used as spam attachments leverage the CVE-2017-8570 vulnerability of Microsoft Office to install malicious payload on the machine of victims. These spam and phishing emails use social engineering techniques such as fake product order requests and invoice documents to trick the victims to open the attachments. The exploit serves as a downloader to other high-profile malware such as Loki and Nanocore.
This exploit is capable of the following:
- Downloads high-profile malware namely Loki and Nanocore
- Uses composite moniker in the RTF file to execute a Windows Script Component (WSC) file or scriptlet (.sct) on the victim's machine
- Bypasses the Microsoft patch for CVE-2017-0199
This exploit typically follows the infection chain below: