DRIDEX
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
DRIDEX is a banking Trojan that was first seen in 2011 and is still in the wild up to this day. It was created from the source code of the BUGAT, also known as CRIDEX, banking Trojan. This malware arrives in a system as an email attachment or in some variants arrives as exploit downloads.
It is capable of performing browser attacks via web injects to steal information such as credentials, certificates, and cookies from the compromised system. Most variants contain keyloggers, which allowed user information to be used in fraudulent banking transactions. It is also capable of downloading additional modules from its C&C to the compromised system.
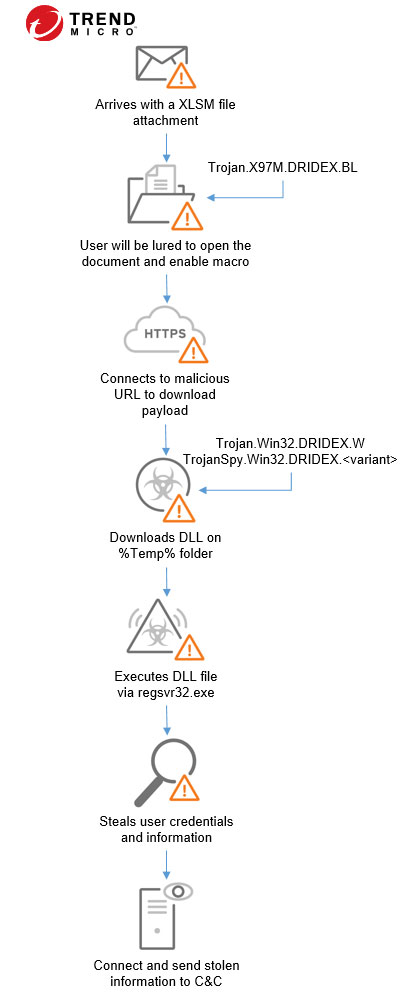
In a recent campaign, the email uses spoofed account from a courier company and uses an invoice attachment to lure the victim into opening it. The attached XLSM file has document presented as an invoice to deceive the victim. It has a button - VIEW or VIEW AND PRINT - that could be used if the macro is enabled. Clicking on the button will also execute the malicious code. It connects to a link that downloads a file with a ZIP or RAR extension however the file downloaded is a DLL. It will be executed using regsvr32.exe and the malware will connect to the C&C server.
It is known to:
- Steal user credentials, financial and banking information
- Execute backdoor commands from a remote malicious user to connect to malicious websites for sending and receiving information
A typical DRIDEX infection chain is as follows: