BLADABINDI
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
BLADABINDI was first spotted in June 2013 as a prevalent malware in Middle Eastern region. It is also known as njRAT, a remote access Trojan (RAT) built in .NET Framework. The malware allows attackers to execute commands on the infected host, log keystrokes, and remotely turn on the webcam and microphone of victim. It was developed by the Sparclyheason group to be used in their largest attacks way back 2014.
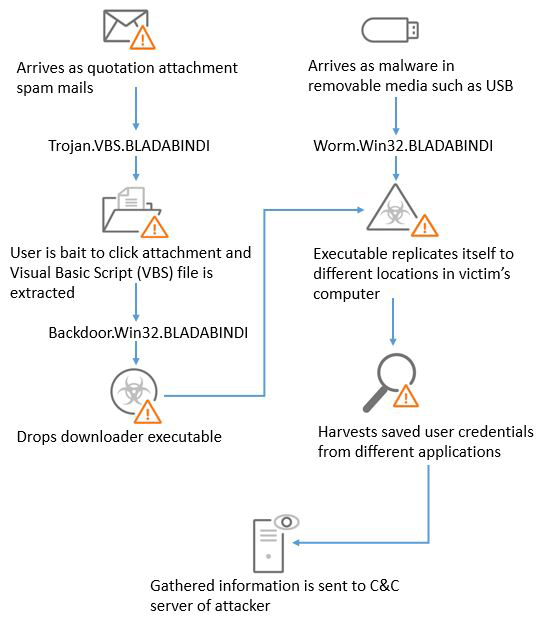
It is now distributed by spam email with fake payment receipts, invoices, and product quotation requests. The malware can access the machine through a security vulnerability, or via removable devices such as a Universal Serial Bus (USB) drive. The current BLADABINDI malware targets computers running on Windows system by copying the original names of genuine Windows files to disguise itself on the infected machine and bypass detection.
It does the following:
- Bypasses detection by mimicking names of genuine Windows files
- Steals system information including usernames and passwords, and other personal and confidential information
- Scans for camera drivers and installs plugin to secretly record the user
- Captures screenshots and logs keystrokes
- Steals Internet browser credentials
- Performs process, file, and registry manipulations
- Disables Task Manager, Registry Editor, and Folder Options
It is capable of the following:
- Information Theft
- Backdoor Commands
- Propagation
- Disabling Usage Capability
BLADABINDI follows the typical infection below: