Uncover Cloud Attacks with Trend Vision One and CloudTrail
By Yash Verma
By 2025, Gartner has projected that over half of enterprises’ expenditure on software, infrastructure, business process services, and system infrastructure will be directed toward cloud-based solutions. We have seen this trend in enterprise spending both during and after the pandemic, on top of how fast companies are shifting to the cloud. Figure 1 shows how the market size is increasing for cloud providers, especially for Amazon Web Services (AWS), which still holds the highest market share.
Additionally, researchers have predicted that over next 10 years, the market size for cloud will quadruple (Figure 2). Due to this upward trend in cloud adoption, attackers are no doubt also shifting their focus to cloud-related attack surfaces.
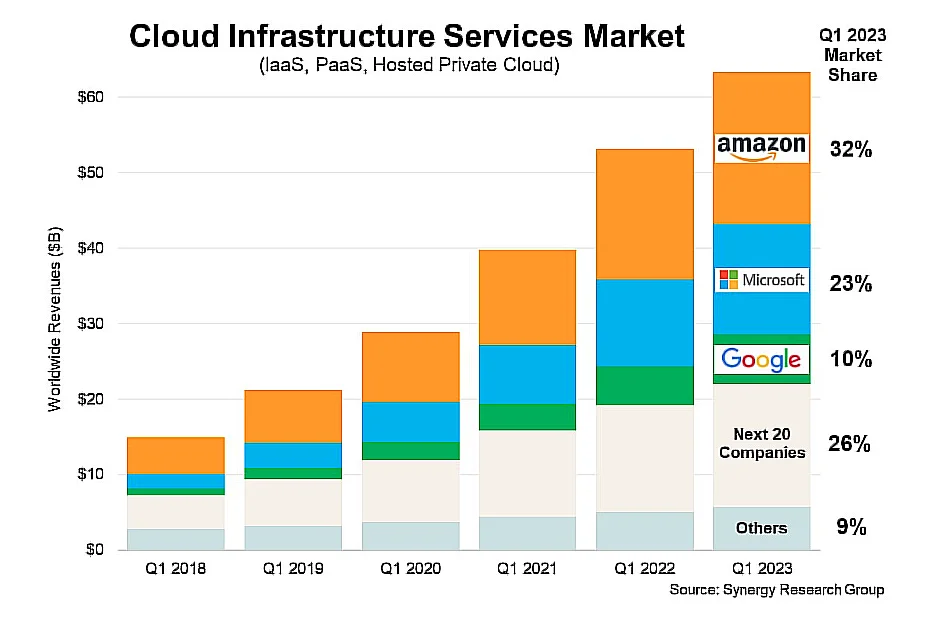
Figure 1. Cloud infrastructure services market in the first quarter of 2023
Source: Synergy Research Group
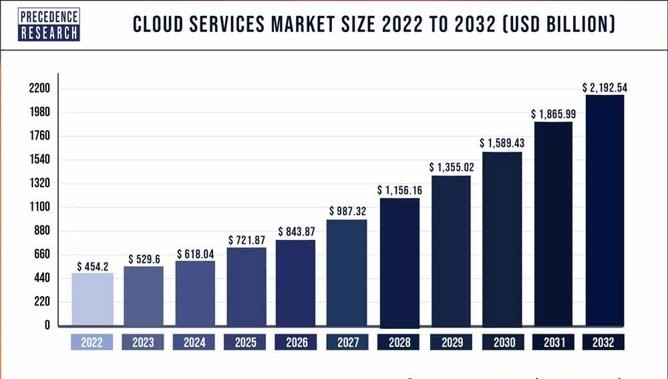
Figure 2. Projected size of the cloud services market from 2022 to 2032
Source: Precedence Research
Trends in attacks targeting AWS
As shown in Figure 3, there has been a notable surge in cyberattacks focused on cloud infrastructures in recent years, with AWS a prominent target. This timeline also highlights instances where major AWS customers have been disproportionately targeted, often attributed to misconfigurations. To gain insights into the prevalent attack vectors, it is imperative to examine the common methods attackers use to breach different AWS services with respect to the MITRE cloud matrix, which will be discussed further in this blog entry.
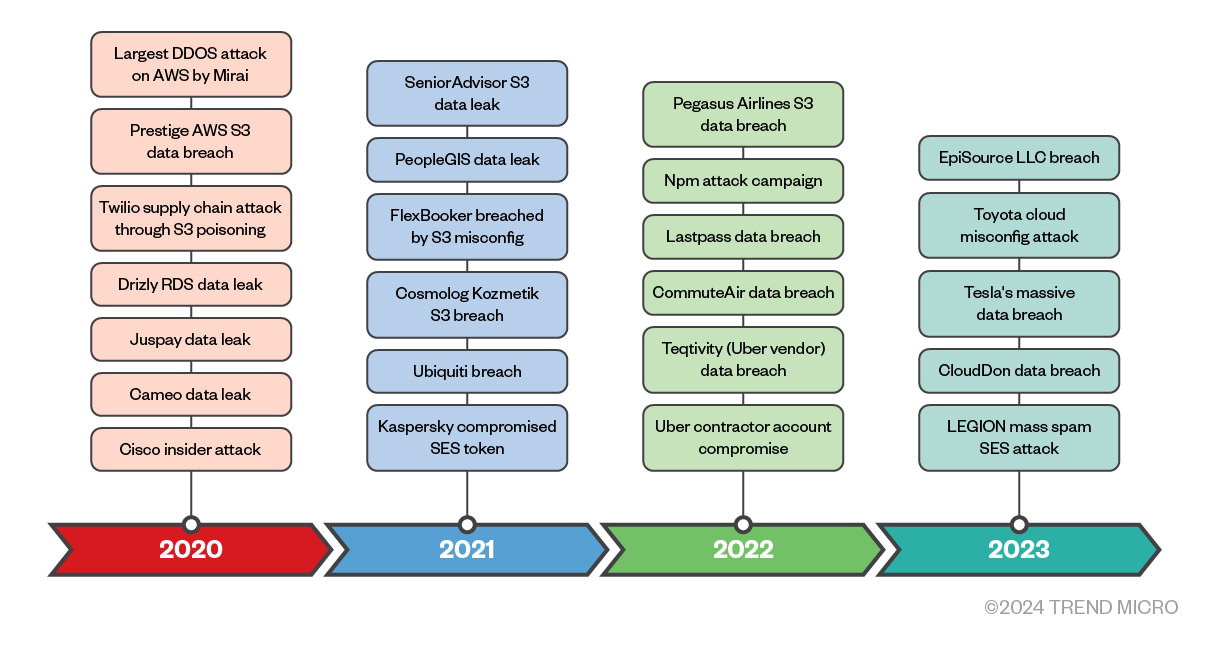
Figure 3. Historical overview of AWS security breaches
Source: Precedence Research
Deep dive into the CloudTrail log
AWS CloudTrail is a service that logs, monitors, and retains account activity related to actions across the AWS infrastructure to assist with visibility, compliance, security, and operational efficiency for AWS accounts. The different types of “trails” that CloudTrail offers are as follows:
- Management Events. These capture management operations performed on resources in an AWS account
- Examples: Creating an EC2 instance, deleting an S3 bucket
- Data Events. These provide detailed information about the resource operations performed on or within a resource
- Examples: S3 object-level API activity (GetObject, DeleteObject), Lambda function execution activity
- Insights Events. These help identify unusual operational activity in an AWS account
- Examples: Detecting spikes in resource provisioning, unusual changes to IAM permissions
Here is an example of a CloudTrail log:
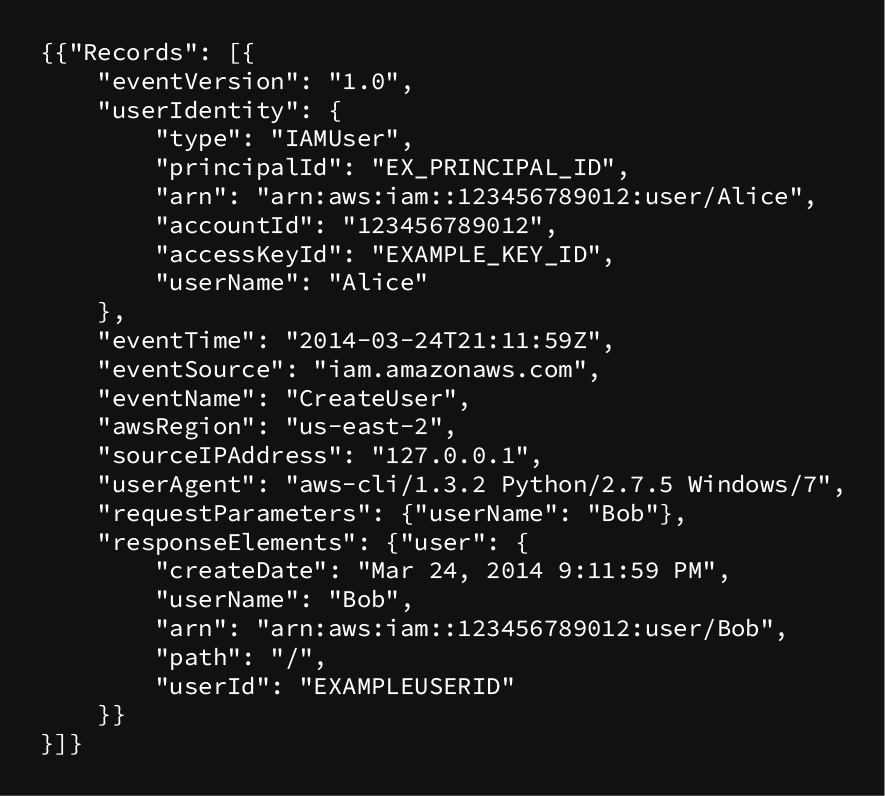
The following are the different fields found in a CloudTrail log in detail, while ensuring originality:
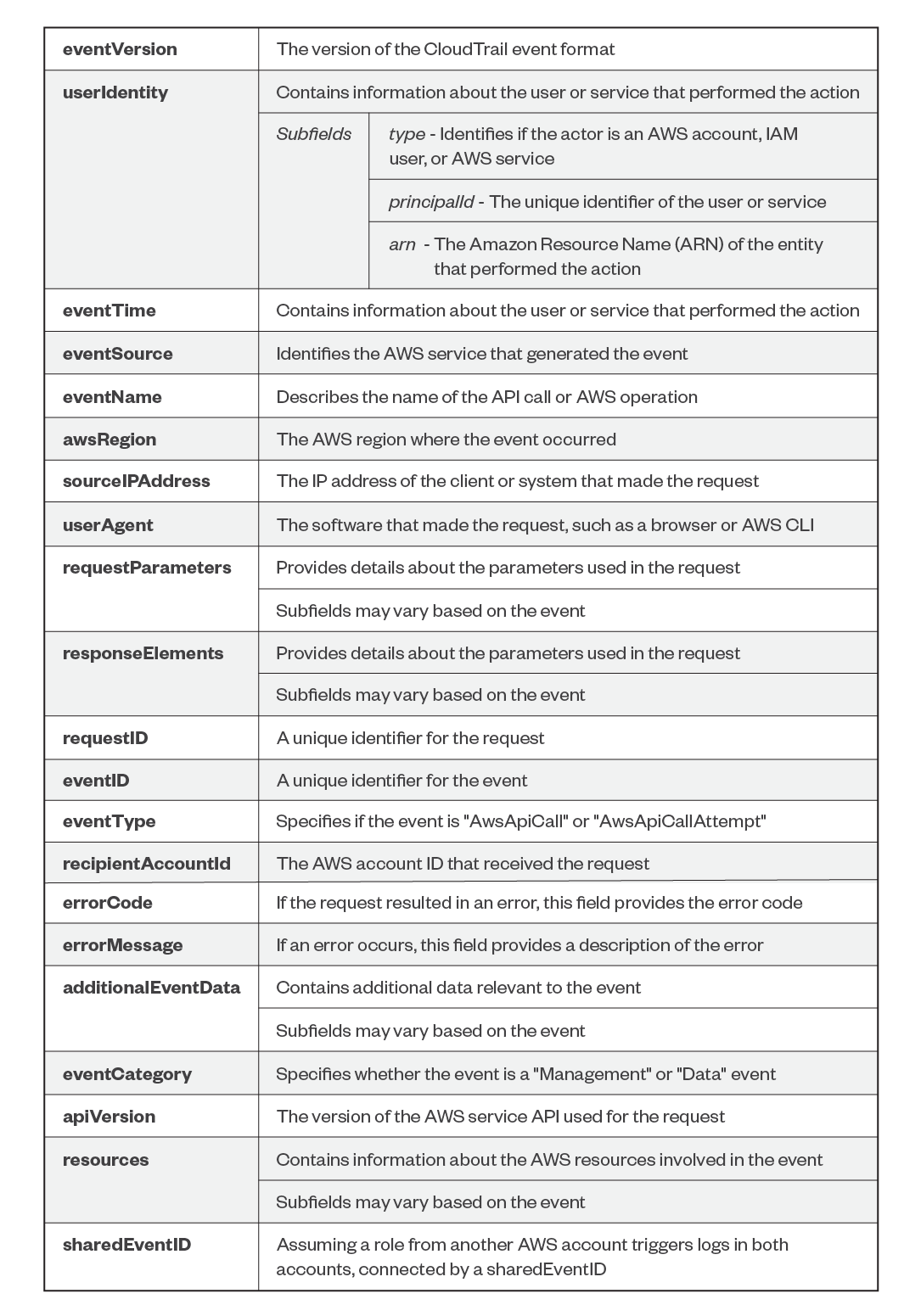
AWS CloudTrail and Trend Micro Vision One integration
Having visibility over tons of CloudTrail logs can be challenging. To address this challenge, Trend’s Vision One now ingests CloudTrail logs from AWS account (Figure 4). This allows Vision One to examine AWS CloudTrail logs from a user’s AWS accounts, detect threats and attacks, notify users of issues, provide response actions, and generate a visual representation of the logs.
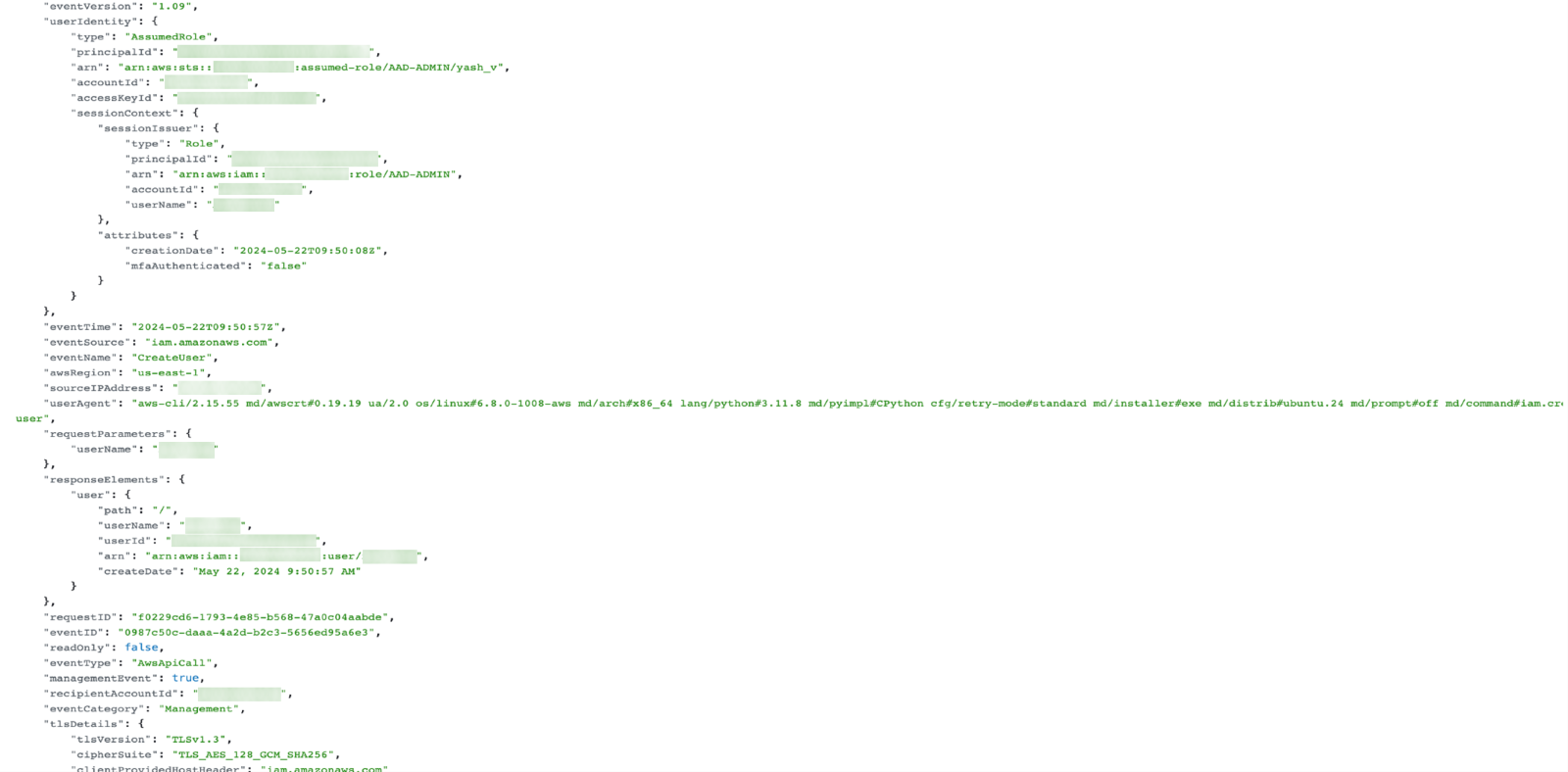
Figure 4. Raw CloudTrail logs
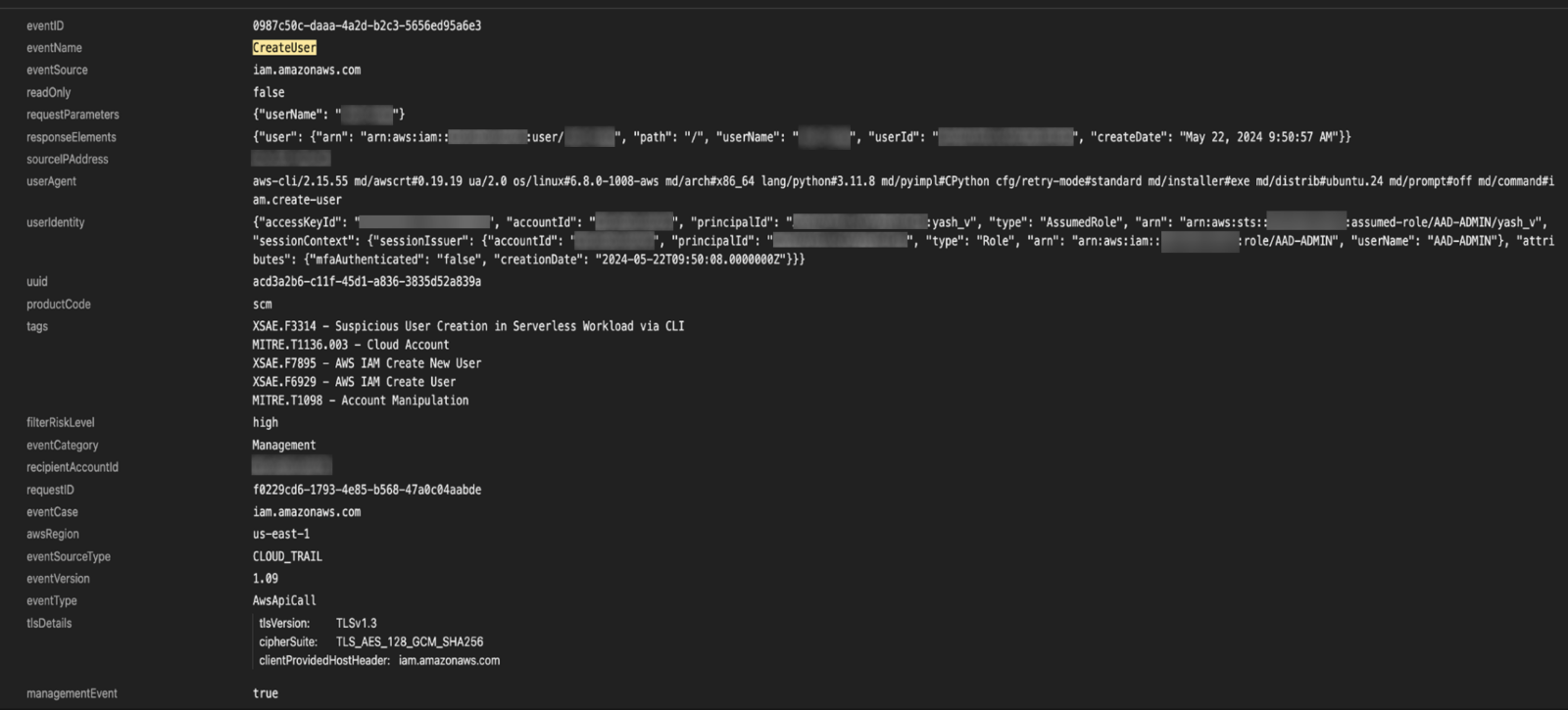
Figure 5. CloudTrail logs on Vision One
As shown in Figure 5, Vision One produces a better visual representation of the logs: It enriches the logs with various detection and MITRE tags to help customers hunt for various suspicious activities within their AWS account. Customers can use the Vision One Search app to hunt for any specific log that they want to view, like the one shown in Figure 6. Customers can deploy this solution by referring to documentation about their AWS accounts and CloudTrail settings, which are quite straightforward.
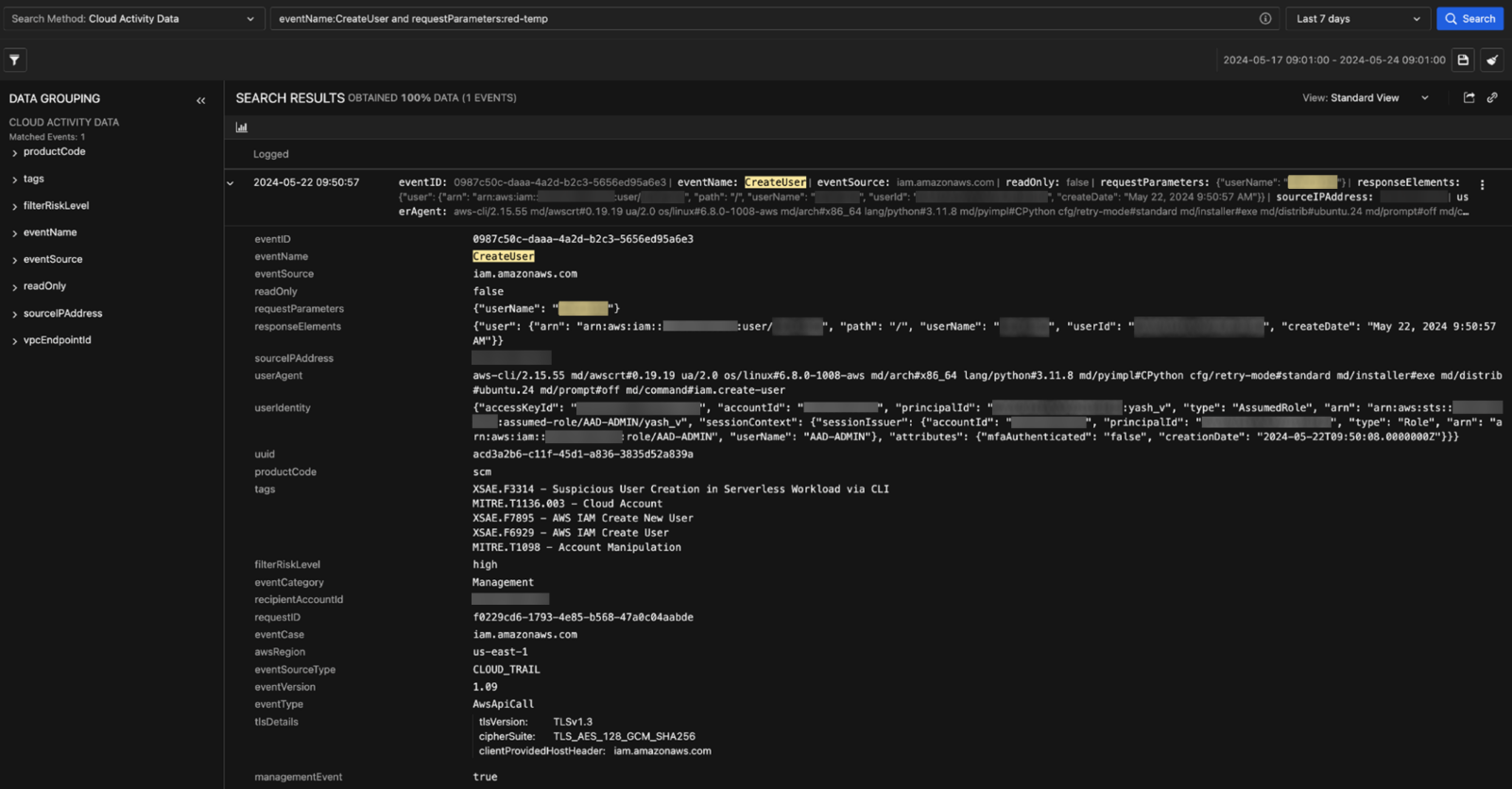
Figure 6. The Vision One Search app used to find a specific AWS log
Vision One detections for CloudTrail: WorkBenches
Trend also provides various detections around CloudTrail that customers can directly leverage to monitor different suspicious activities or even ongoing attacks in their AWS account. This article explores a few examples of real-world AWS attack scenarios under different MITRE cloud tactics and how the workbench would look like.
Initial access
The MITRE ATT&CK framework for cloud environments identifies initial access as a critical tactic where attackers gain their first foothold within a target AWS environment. In AWS, there are three primary methods by which attackers achieve this initial access (Figure 7):
- Accessing exposed keys
- Attackers often seek to find and exploit exposed AWS keys.
- These exposures can occur when credentials are inadvertently placed in publicly accessible code repositories, websites, or other insecure locations.
- Once these keys are discovered, attackers can use them to gain unauthorized access to AWS resources.
- Exploiting public apps hosted on AWS computes with permissions
- Attackers target vulnerabilities in publicly accessible applications hosted on AWS compute resources.
- These applications may have permissions to access other AWS resources, providing attackers a path to escalate their access.
- By exploiting these vulnerabilities, attackers can gain unauthorized access and move laterally within the cloud environment.
- Vulnerabilities in the AWS service
- Although less common, vulnerabilities within AWS services represent a significant threat.
- Exploiting these inherent weaknesses in the cloud provider’s infrastructure can allow attackers to bypass traditional security measures.
- This method provides attackers with direct access to the cloud resources.
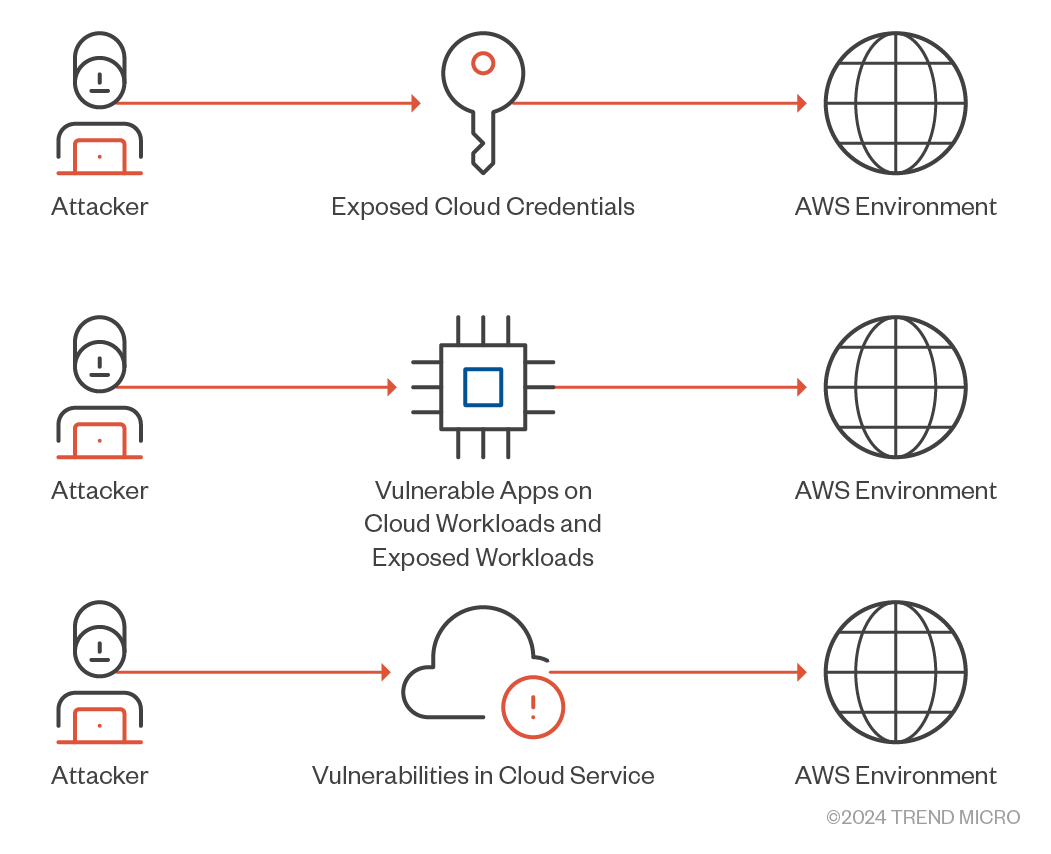
Figure 7. Methods attackers can use to gain initial access to an AWS environment
Consider a scenario wherein an attacker gains an initial foothold in an AWS account by exploiting a remote code execution (RCE) vulnerability in an over-privileged AWS Lambda function hosting a public website. To maintain persistence, the attacker then changes the Lambda function's timeout settings and tries to perform other activities like enumeration of the IAM service and creation of new users.
In this case, the Vision One Workbench detects this initial Lambda compromise, as shown in Figure 8:
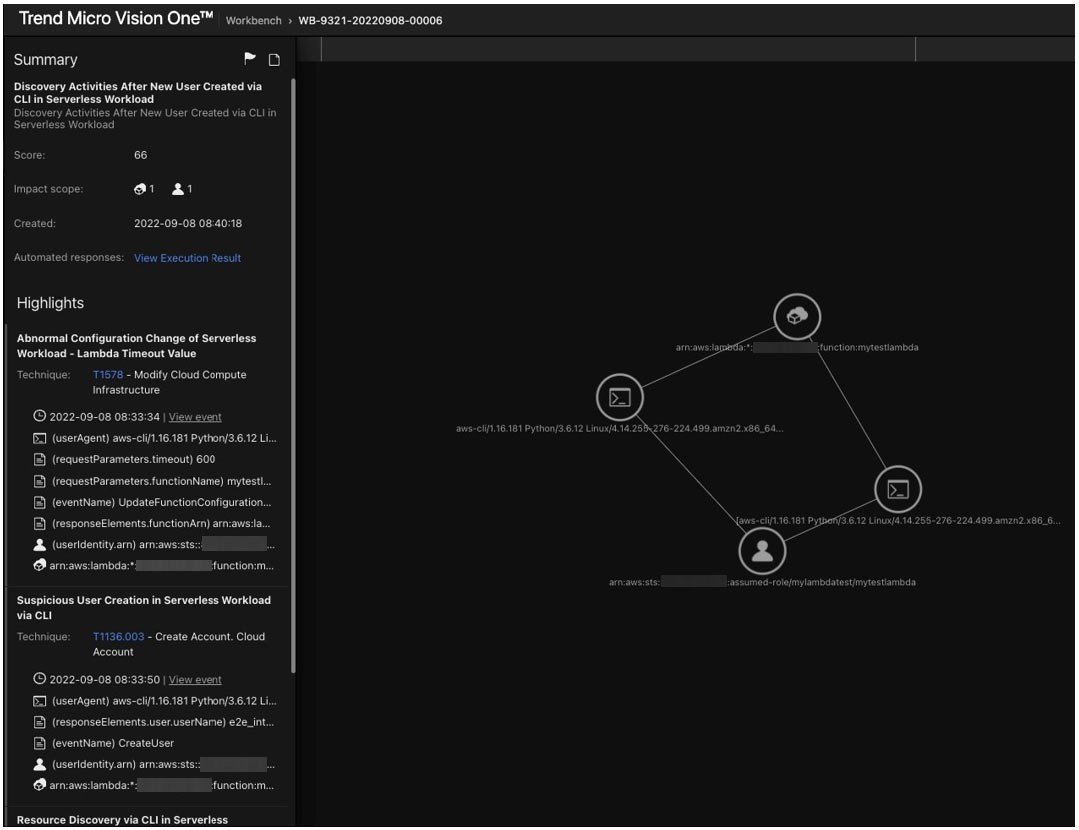
Figure 8. Vision One Workbench detects a compromised Lambda function
Execution
Execution involves carrying out adversary-controlled code or commands within the cloud environment (Figure 9). This could include running scripts on EC2 instances, invoking Lambda functions, or using AWS APIs to perform unauthorized code executions, potentially leading to data breaches or system compromise.
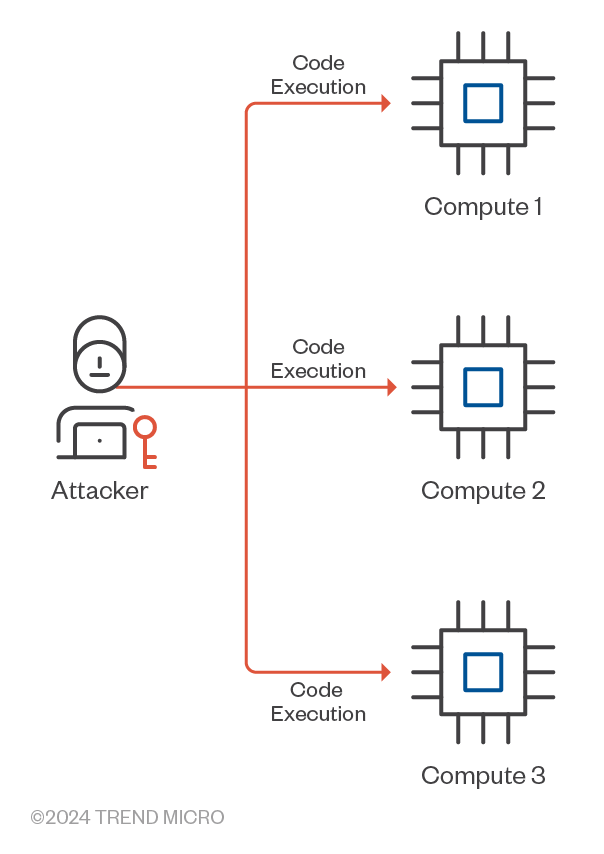
Figure 9. An attacker sends code or commands within a cloud environment
The SendCommand API in AWS EC2 instances enables users to remotely execute commands via AWS Systems Manager. However, it can lead to severe security breaches if accessed maliciously. In a potential attack scenario with respect to execution, an adversary gains initial access to the AWS environment, identifies EC2 instances with the Systems Manager agent, and exploits misconfigured IAM policies or stolen credentials to execute unauthorized commands through the SendCommand API. This could result in the installation of malware, data exfiltration, or other harmful activities, emphasizing the importance of securing access to this API and closely monitoring its usage for suspicious behavior.
Figure 10 shows how the detection would look like in Vision One:
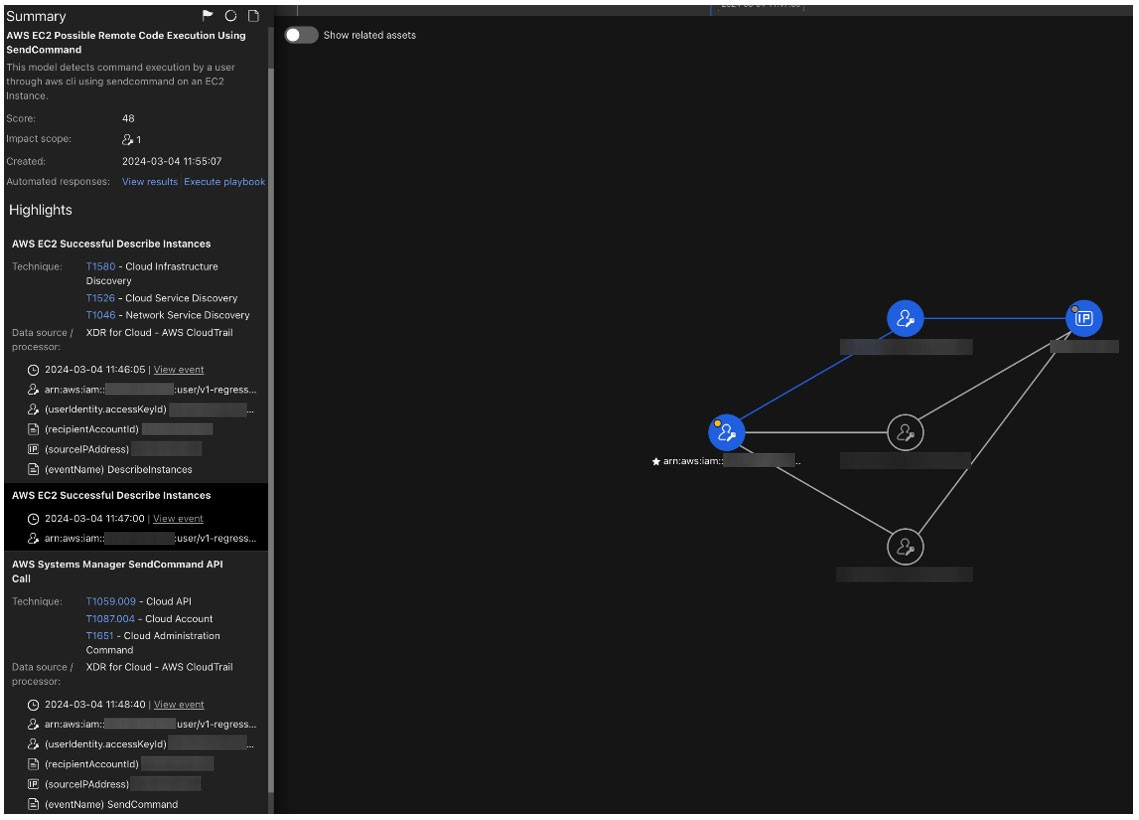
Figure 10. Vision One detects possible remote code execution
Discovery
Discovery involves attackers gathering information about the target cloud environment by directly using compromised keys or enumerating them after getting a foothold in computers with permissions (Figure 11). This intelligence aids attackers in planning further attacks. Attackers collect this information through various means, which include:
- Reviewing CloudTrail logs for API activity, examining IAM policies for excessive permissions
- Scanning for publicly accessible resources like EC2 instances and S3 buckets
- Querying metadata endpoints for instance details
- Enumerating DNS records for infrastructure information
- Enumerating cost explorers and AWS organisations to know more about the size and structure of the target
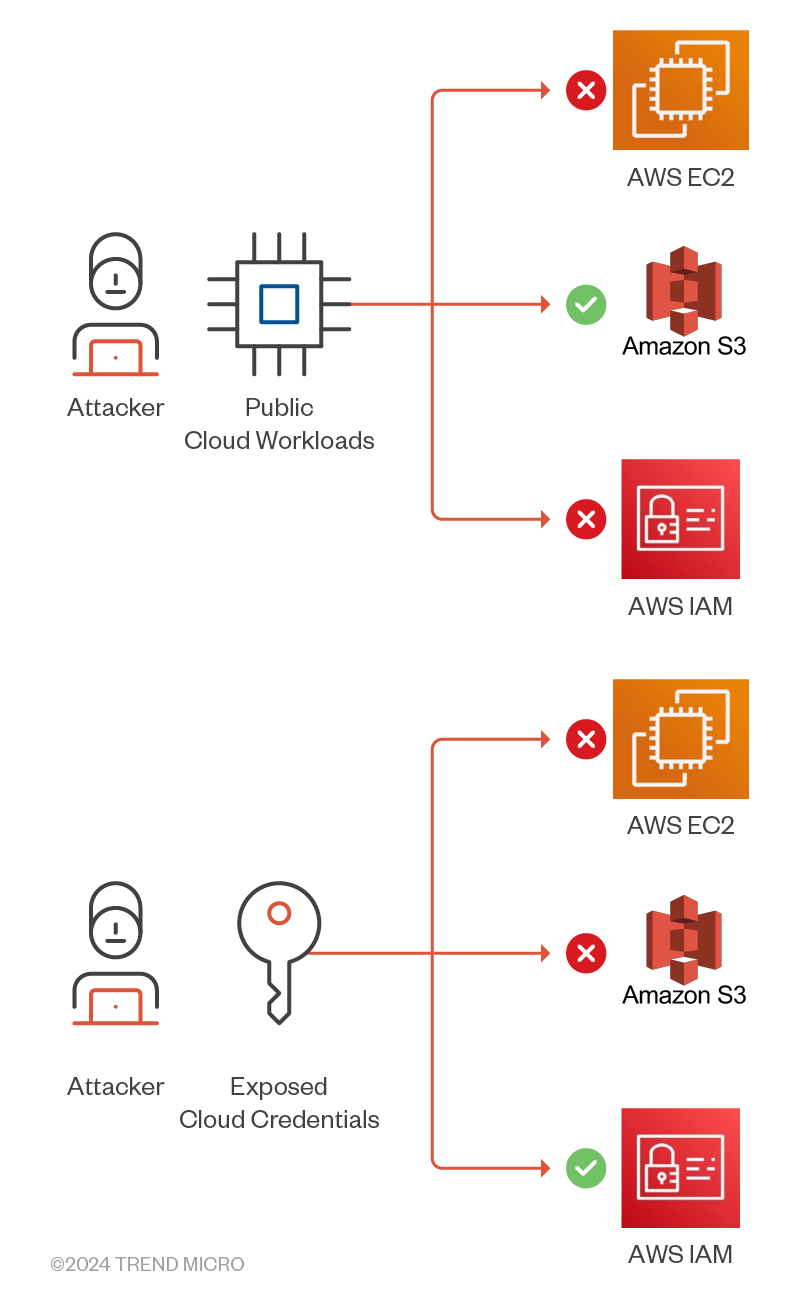
Figure 11. How attackers gather information about their targeted cloud environment
Consider an attack scenario in which an attacker gains initial access to an AWS environment and proceeds to enumerate IAM permissions through various methods such as analyzing IAM policies, investigating role trust relationships, and searching for additional credentials. With this information, the attacker targets overly permissive roles, allowing for lateral movement within the environment and data exfiltration from AWS resources. Vision One detects such enumeration techniques, as shown in Figure 12.
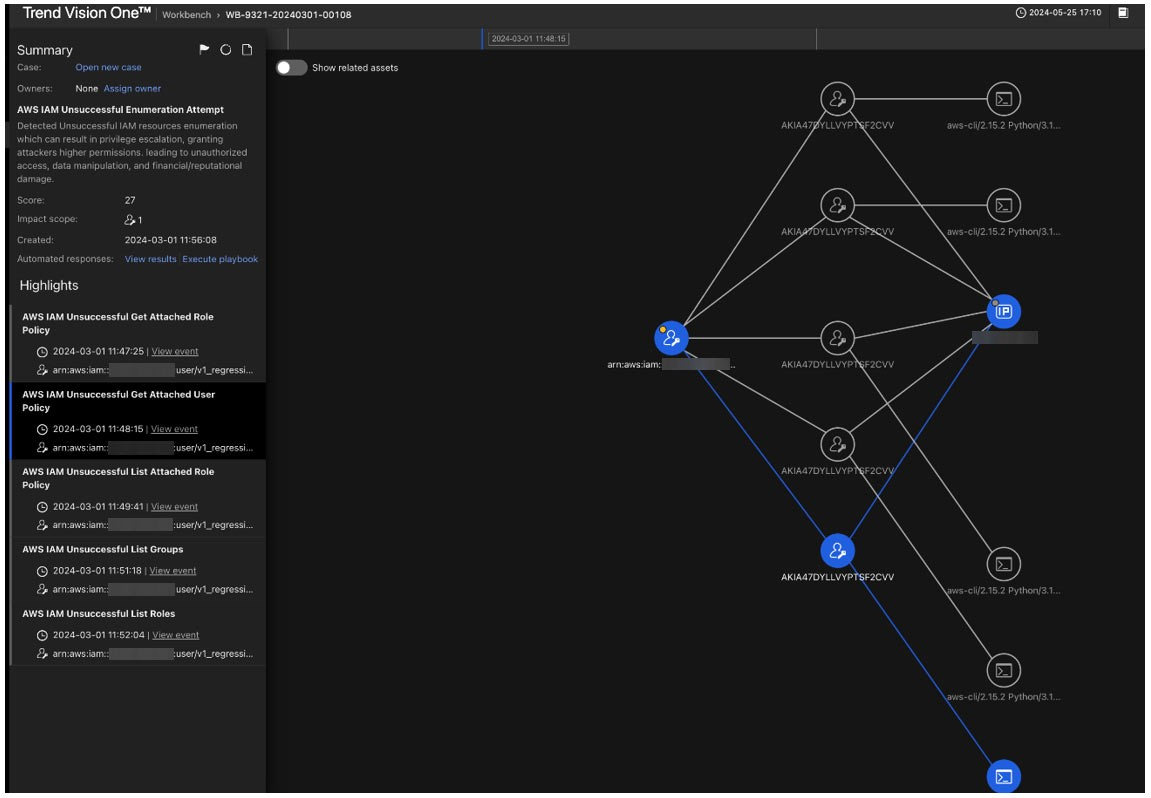
Figure 12. Vision One detects enumeration techniques in AWS environments
Exfiltration
The exfiltration tactic involves attackers extracting and transferring data from the cloud environment to an external location under their control. Attackers typically enumerate resources such as S3 buckets, databases (like RDS and DynamoDB), EC2 instances, and managed services to identify valuable data (Figure 13). Once identified, attackers exploit vulnerabilities or weak access controls to access and download this sensitive information. Subsequently, they transfer the stolen data to external servers or repositories or external AWS accounts. This tactic poses significant risks to organizations, as it can lead to the loss of confidential information, intellectual property, or customer data, potentially resulting in financial and reputational damage.
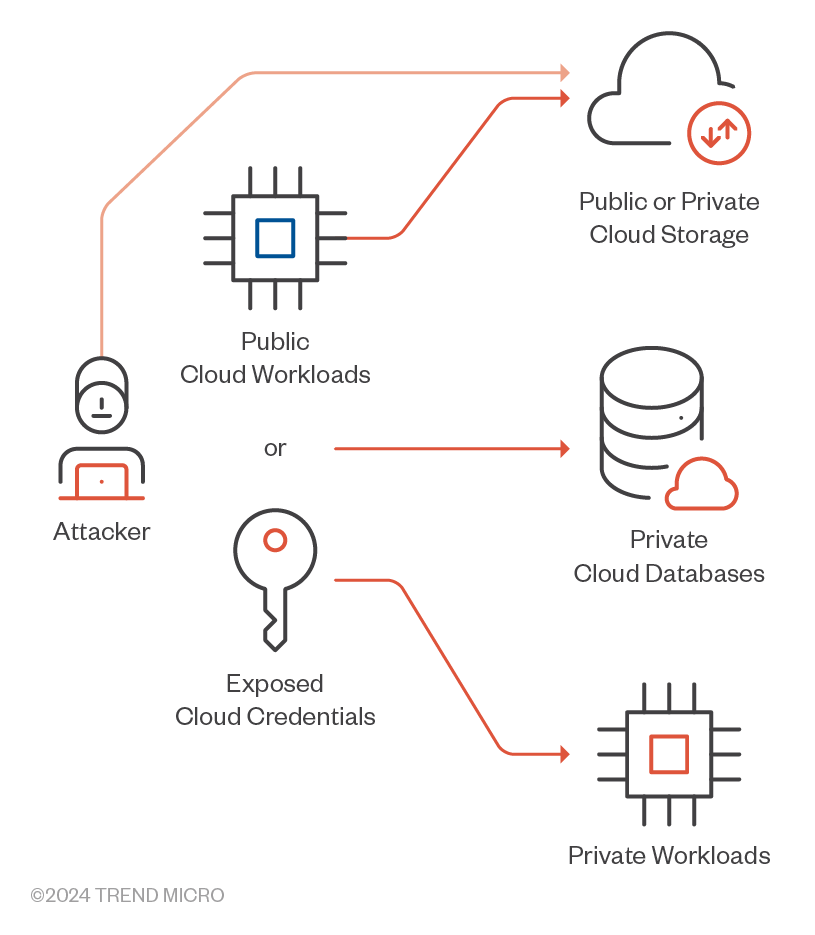
Figure 13. Methods with which attackers can extract and transfer valuable data from a cloud environment
Consider an attack scenario in which an attacker gains access to an AWS database (like Amazon RDS) within an organization's environment. They create a snapshot of the database containing sensitive data and share it publicly or with an external AWS account under their control. This allows them to exfiltrate the data externally which poses significant risks to the organization. Vision One helps detect these kinds of attacks, as shown in Figure 14.
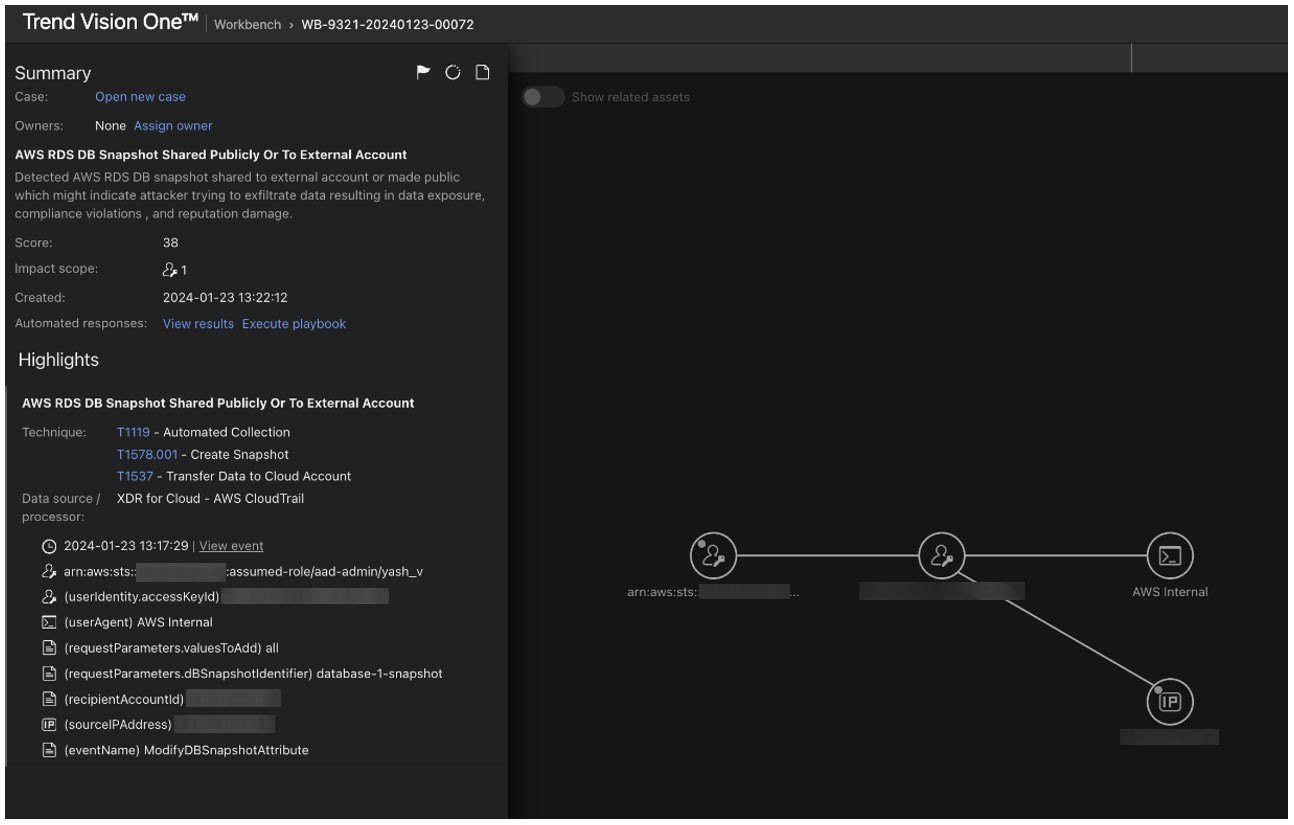
Figure 14. Vision One detecting when a snapshot of an AWS database is shared
Privilege escalation
Privilege escalation involves adversaries gaining higher-level permissions through various sophisticated methods (Figure 15). Common techniques include exploiting overly permissive IAM roles or misconfigured trust relationships, abusing AWS services such as Lambda functions and EC2 instance metadata, and manipulating IAM policies. Attackers may also compromise access keys, hijack user sessions, or use the sts:AssumeRole API to incrementally assume higher privileges. Resource-based policy abuse is another critical method, where misconfigurations can be exploited for unauthorized access. These techniques highlight the importance of stringent access management and vigilant monitoring to safeguard AWS environments against potential privilege escalation attacks.
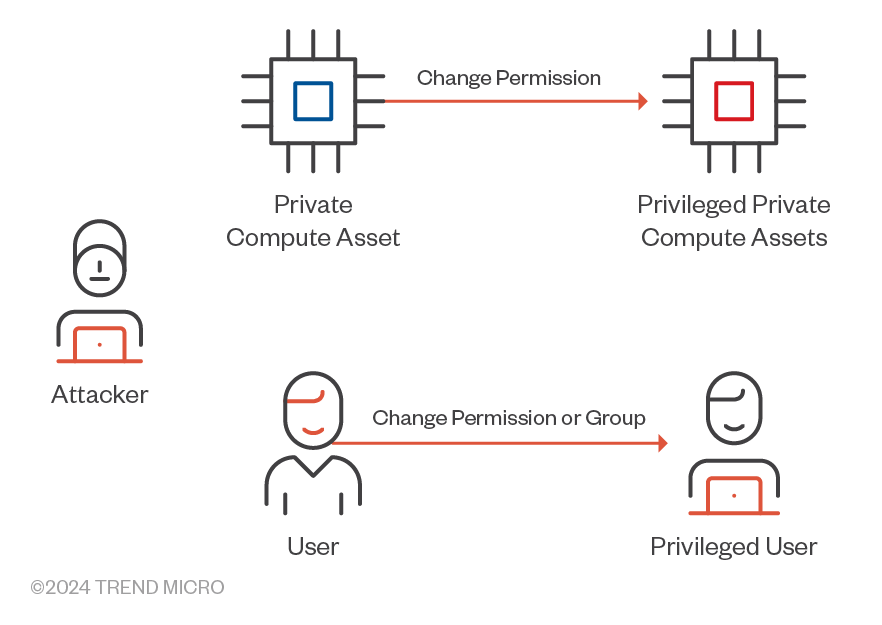
Figure 15. Methods with which attackers can gain higher-level permissions
To illustrate privilege escalation in AWS, consider an attacker who gains access via compromised credentials of a user with limited permissions. The attacker identifies that this user can modify IAM policies, then creates and attaches an admin policy to their account, thereby gaining full administrative control. This enables them to perform any actions within the AWS account, such as accessing sensitive data and creating or deleting resources. Monitoring and alerting on such activities is crucial. Vision One assists by providing alerts for these kinds of activity, enhancing security visibility into the AWS account (Figure 16).
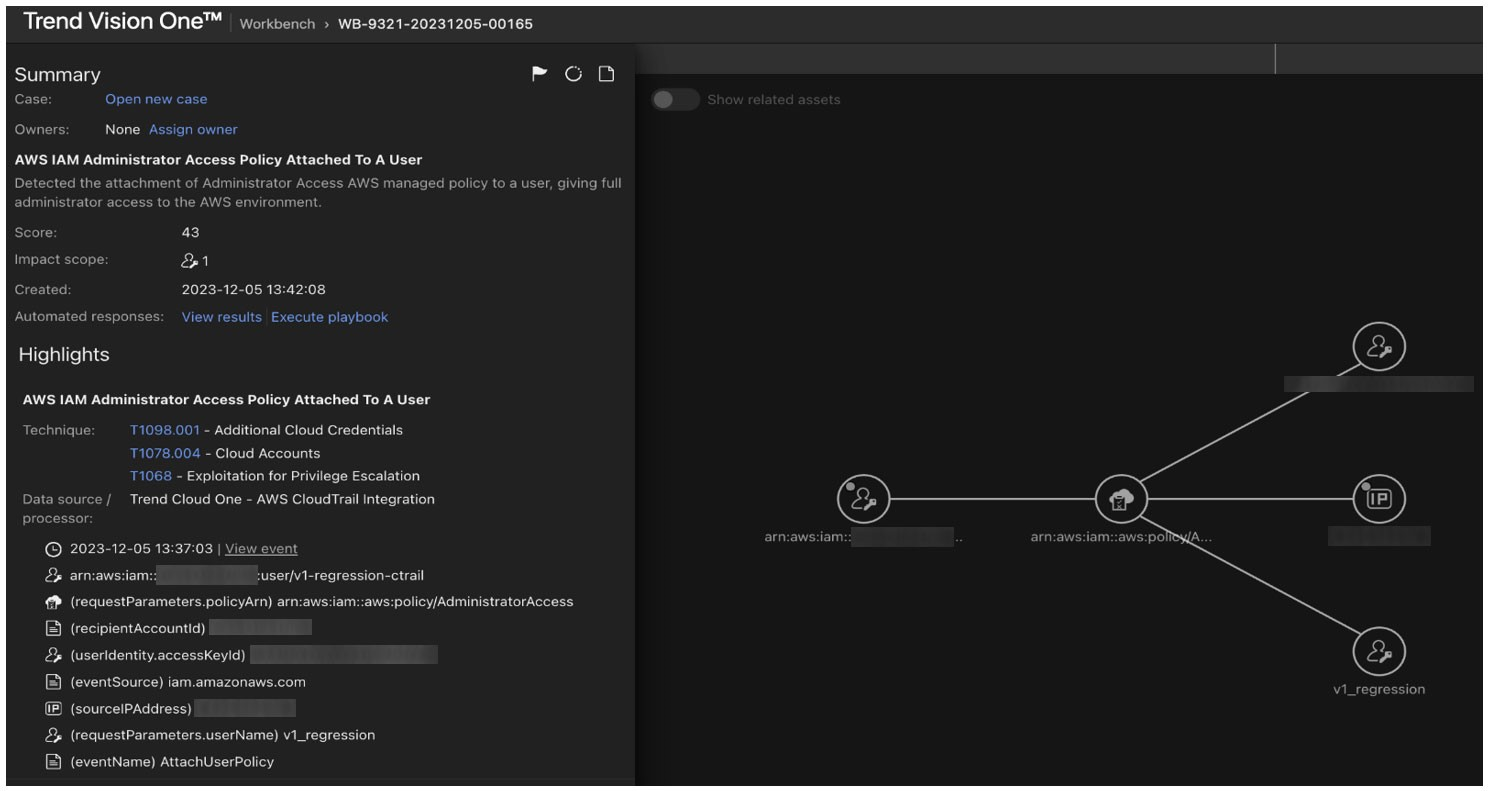
Figure 16. Vision One can provide alerts for suspicious activity that points to possible privilege escalation
Lateral movement
In AWS, lateral movement refers to how attackers move within the cloud environment after initial access, targeting further resources. This can occur across different services, accounts, and compute resources (Figure 17). The kinds of lateral movement in AWS environments include:
- Cross-Service. Attackers use compromised credentials to access various AWS services, often leveraging IAM roles and API calls.
- Cross-Account. Attackers exploit trust relationships or shared resources to move between AWS accounts, using methods like the AssumeRole API.
- Cross-Compute. Attackers exploit EC2 instance metadata, Lambda vulnerabilities, or container exploits to move between compute resources
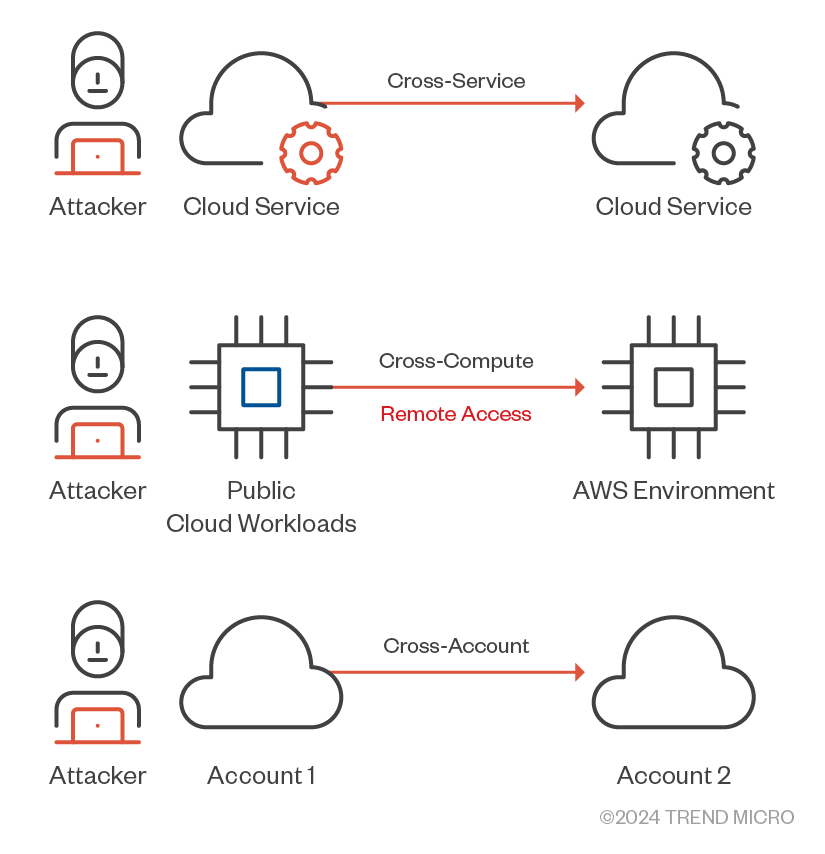
Figure 17. Methods with which attackers can perform lateral movement
Consider an attack scenario in which a malicious actor escalates their privileges to obtain full access to AWS Systems Manager (SSM). The attacker then uses this access to move laterally to EC2 instances, where they can conduct further malicious activities such as cryptocurrency mining and ransomware activities. Vision One can monitor these types of suspicious activities (Figure 18).
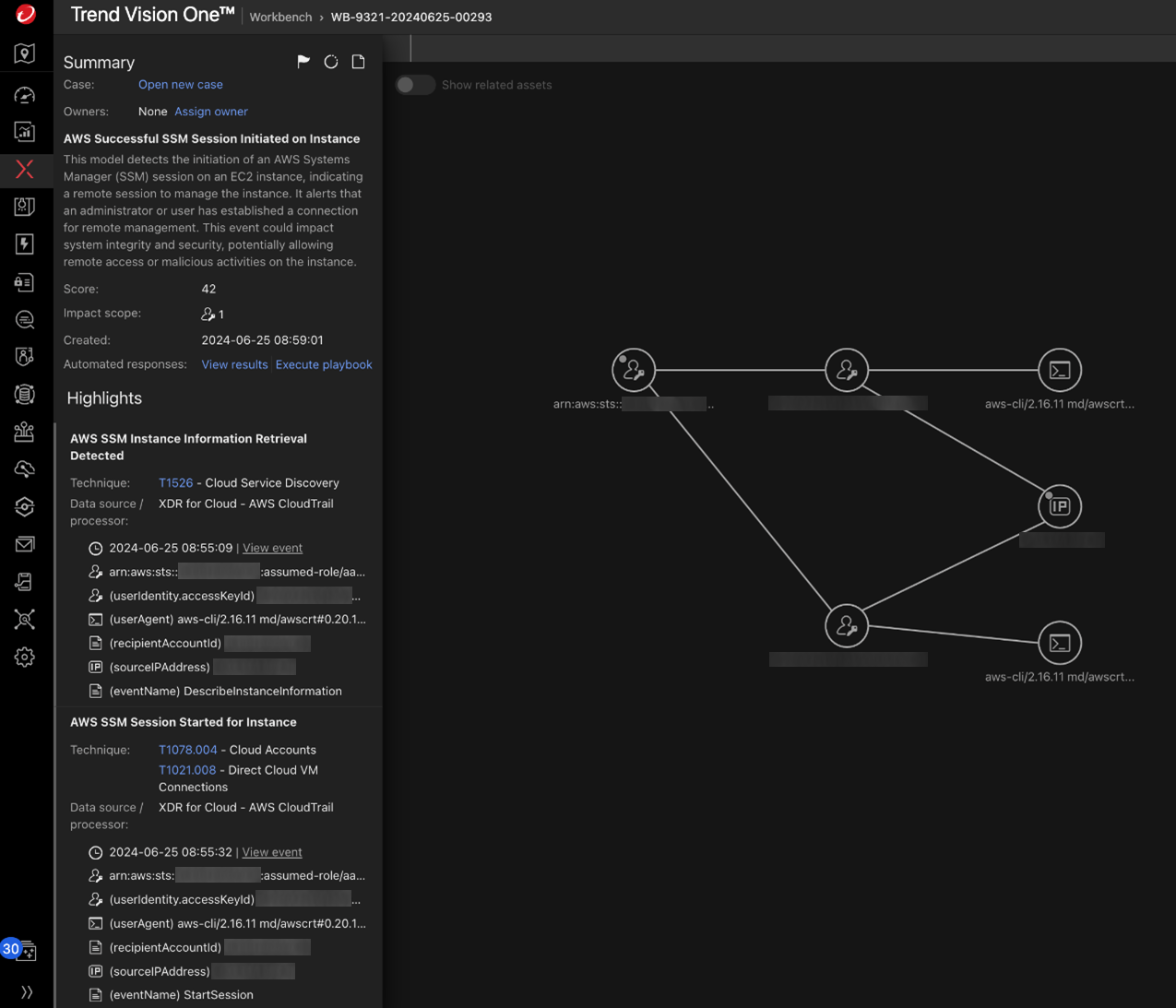
Figure 18. Vision One can monitor SSM access to spot a potential attacker’s lateral movement
Defense evasion
In AWS, the defense evasion tactic involves the use of various methods to circumvent security measures and evade detection. Attackers either directly disable or delete cloud logs — including CloudTrail logs, Cloudwatch logs, S3 access logs, and GuardDuty logs — or compromise an AWS compute with required permission to do so (Figure 19).
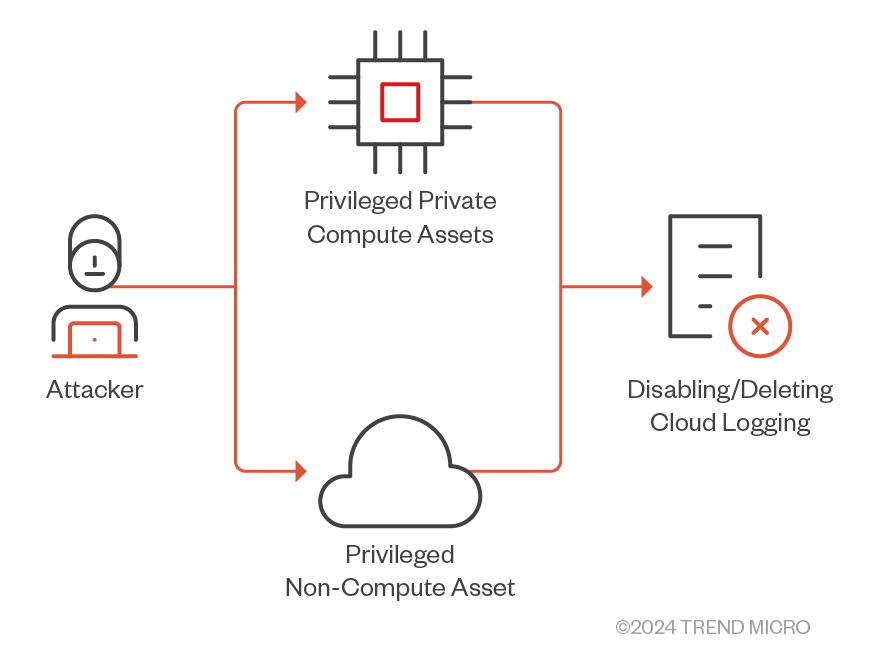
Figure 19. Methods with which attackers can disable or delete cloud logs
Consider a scenario where an attacker disables logging services like CloudTrail by either compromising a leaked AWS key or user or some compute asset having CloudTrail full access. By evading detection mechanisms, attackers aim to maintain their presence undetected within AWS environments. It‘s crucial to monitor such activities, which security practitioners can do through Vision One (Figure 20).
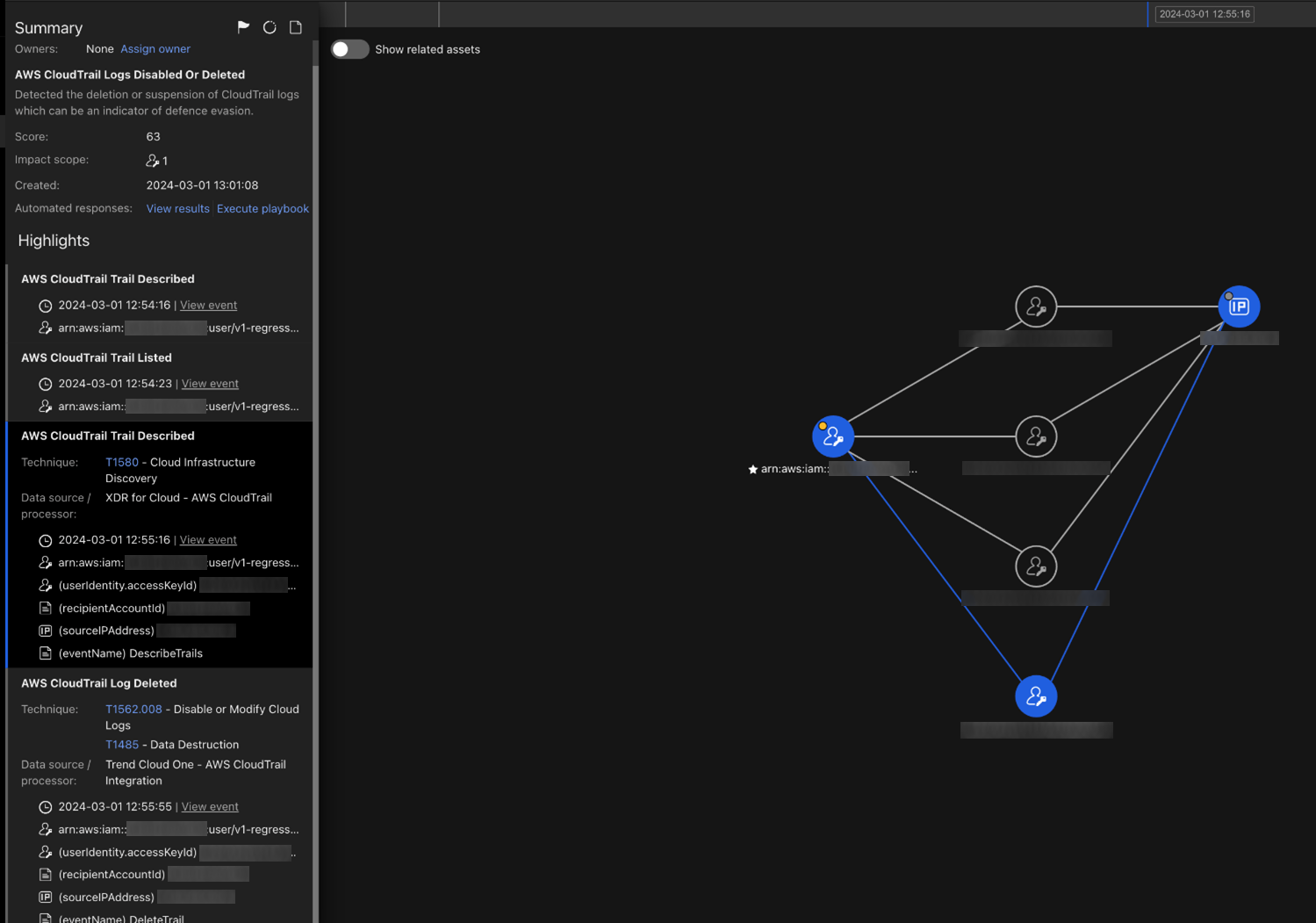
Figure 20. Vision One can detect whether logging services like CloudTrail have been disabled
Persistence
In the context of AWS, the MITRE ATT&CK framework's persistence tactic involves attackers establishing long-term access and control over compromised systems. They achieve this by deploying backdoors, such as ones that modify IAM policies or inject malicious code into AWS Lambda functions, and setting up data exfiltration channels, often through unauthorized S3 bucket access or covert data transfers. Additionally, attackers may use scheduled tasks or cron jobs within AWS services like CloudWatch Events or EC2 instances to maintain persistence. These tactics allow attackers to maintain a foothold in AWS environments, facilitating continued unauthorized access and data exfiltration (Figure 21).
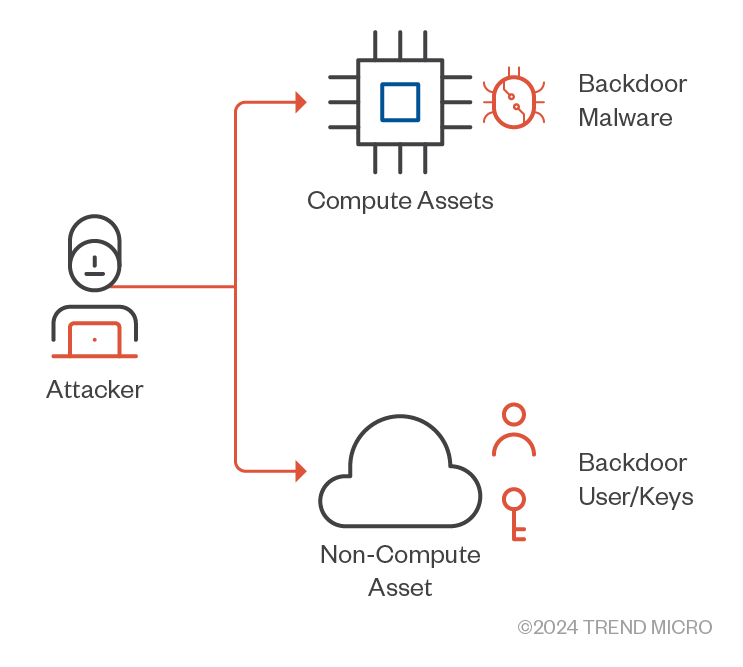
Figure 21. Methods with which attackers can maintain a foothold in AWS environments
In AWS, attackers establish persistence by creating access keys post initial compromise. These keys grant programmatic access to AWS resources, enabling ongoing malicious activities even if initial entry points are closed. Access keys serve as a persistent mechanism, allowing attackers to maintain control and evade detection within the compromised environment. By rotating keys and obfuscating activities, attackers can prolong their presence, posing an ongoing threat to AWS security. So, it becomes very important to monitor creation of access keys, Vision One can help creating alerts for these activities, as shown in Figure 22.
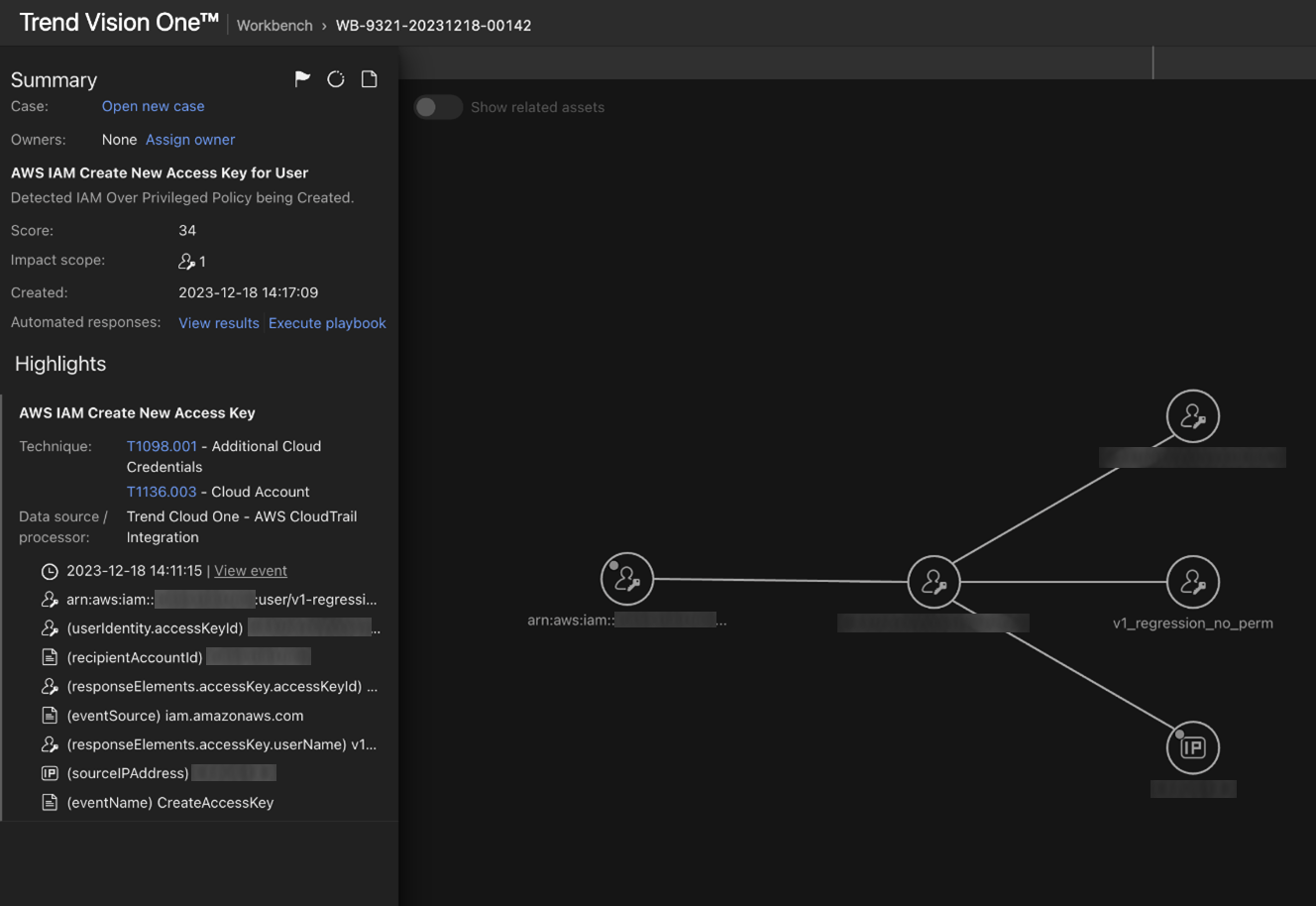
Figure 22. Vision One alerts that monitor the creation of new access keys
Conclusion
Exploring various AWS attack scenarios and how they align with MITRE tactics helps defenders better understand cloud-based threats. Vision One effectively detects each of these threats, providing crucial insights for quick response to protect your AWS environments from further attacks. Securing these environments requires security practitioners to stay proactive and vigilant against potential threats. Apart from utilizing platforms like Vision One, defenders can be in a better position to protect cloud assets through best practices that include:
- Enabling multi-factor authentication (MFA)
- Require MFA for all users, particularly those with administrative access, to add an extra layer of security.
- Implementing the principle of Least privilege
- Grant users and applications the minimum permissions necessary.
- Regularly review and update permissions to match current needs.
- Using IAM roles and rotating credentials
- Use IAM roles for services instead of long-term access keys.
- Regularly rotate IAM access keys, passwords, and other credentials to maintain security.
- Enabling logging and monitoring
- Activate AWS CloudTrail for comprehensive logging of account activity.
- Use Amazon GuardDuty and AWS Config for continuous threat detection and resource monitoring.
- Encrypting data at rest and in transit
- Use AWS Key Management Service (KMS) to encrypt data stored in AWS services.
- Ensure data in transit is protected using SSL/TLS encryption.
- Implementing strong network security
- Use VPCs to isolate different environments and control network access with security groups and network ACLs.
- Enable AWS WAF for application-level protection and VPC Flow Logs for monitoring network traffic.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks