Conti and LockBit Make Waves with High-Profile Attacks: Ransomware in Q4 2021
Ransomware actors were intent on punctuating 2021 with a wave of high-profile attacks. We zero in on LockBit and Conti ransomware operators: two groups that worked overtime in the final quarter of 2021, as evidenced by the modern ransomware campaigns that they launched against different organizations in various countries.
The LockBit 2.0 ransomware group kicked things off for the quarter after it claimed to have stolen and threatened to leak sensitive company data of the E.M.I.T. Aviation Consulting Ltd., an aerospace and defense organization in Israel in October. Meanwhile, the Conti ransomware group was allegedly behind an attack on Graff, an A-list London-based jeweler, and stole the sensitive data of 11,000 of the company’s clients and leaked 69,000 files on the dark web in November. The group also victimized multiple organizations from various industries in Australia, allegedly including CS Energy, the country’s electricity provider. Toward the latter end of November, it hit the industrial automation and industrial internet of things (IIoT) chip maker Advantech with a $14 million ransom demand to decrypt company documents and cease the data leak.
Using Trend MicroTM Smart ProtectionTM Network data, we explored the ransomware threat landscape in the fourth quarter of 2021 and detected a total of 3,250,504 ransomware-related threats across our file, URL, and email layers in the quarter. Our telemetry also showed a 6.12% decrease in overall ransomware threats between Q3 and Q4.
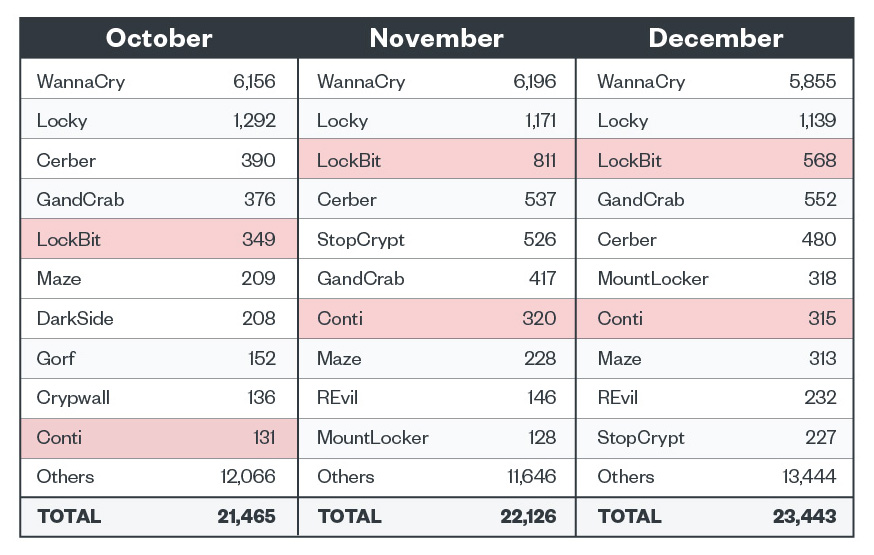
Top 10 ransomware families
Interestingly, LockBit was consistently seen in the top five ransomware families for the quarter, while Conti was more irregular in its placement on the list. This irregularity is due to the fact that modern ransomware actors choose to steer clear from spray-and-pray tactics in their attacks, instead opting for a more targeted approach to deploying their malicious payloads. Meanwhile, in terms of volume of detections, legacy ransomware families topped the list of the top 10 ransomware families during the last three months of the year.
Figure 1. The top 10 ransomware families operating in Q4 2021 (notably active ransomware families highlighted)
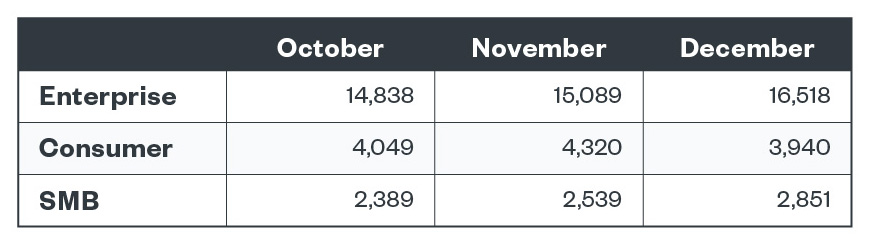
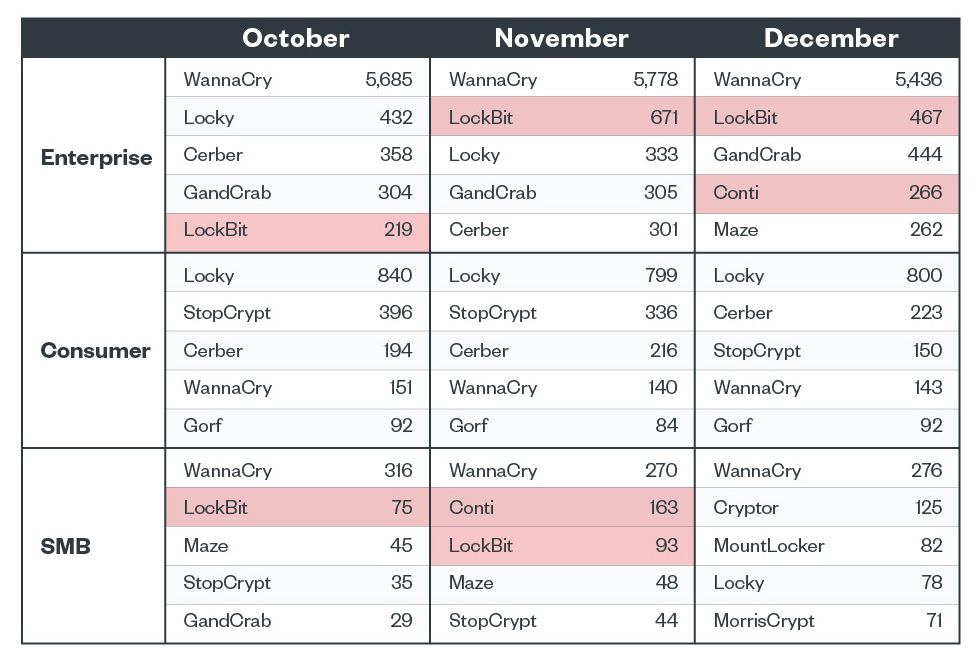
Top five ransomware detections by segment
LockBit was consistently detected from October to December 2021 in the enterprise segment, and in the small and medium-sized businesses (SMB) segment in October and November. Conti, on the other hand, was one of the top five ransomware families in December for the enterprise segment and in the SMB segment in November.
Trend Micro detections reflect just how busy LockBit and Conti actors were in the span of three months. LockBit operators claimed to have launched ransomware attacks on European cryptocurrency exchange BTC-Alpha, helicopter maker company Kopter, and Mexican IT firm Telepro. Meanwhile, the Conti gang compromised the hotel reservations, check-in, check-out, and room key creation systems of the Nordic Choice Hotels — one of the biggest hotel chains in the Scandinavian region in December. In the same month, the group hit yet another hotel chain, McMenamins in Portland, Oregon, and compromised the chain’s servers, machines, and point-of-sale systems. Before the month ended, it weaponized the Log4Shell vulnerability via a full attack chain that includes the Emotet botnet, Cobalt Strike, and Kerberoast.
Figure 2. Monthly ransomware file detections across business segments in the fourth quarter of 2021
Figure 3. The top five ransomware families detected per business segment in the fourth quarter of 2021 (LockBit and Conti highlighted to show activity in connection with news reports)
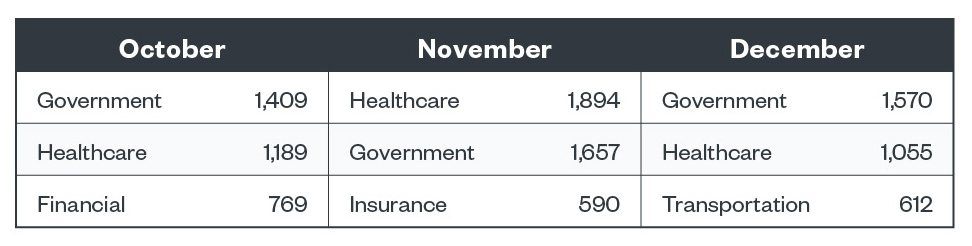
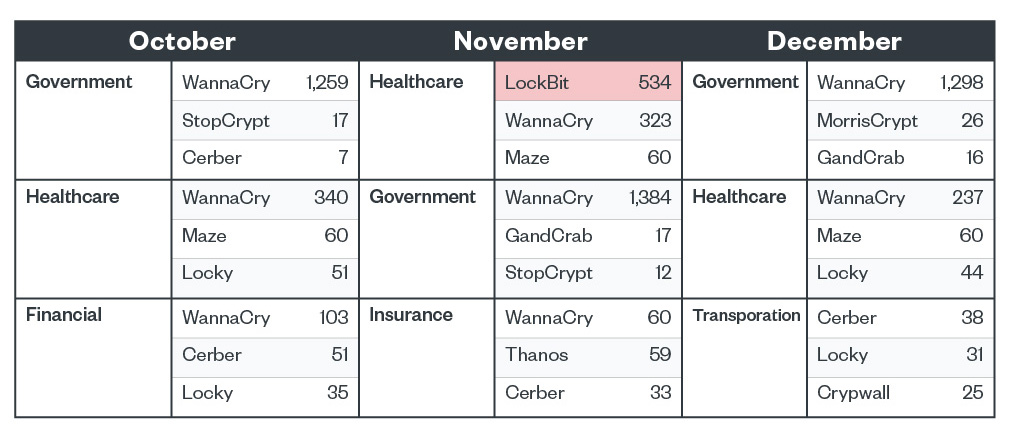
Top three industries with ransomware detections
Similar to the third quarter of 2021, the government and healthcare industries were the two industries with the most number of ransomware detections from October to December 2021. Taking the third spot for the final quarter were the financial, insurance, and transportation industries, respectively.
Legacy ransomware families mostly topped the list across the board, however, we saw a surge in LockBit detections in the healthcare industry in November. Previously, LockBit actors have claimed that they do not target healthcare, education, social services, and charitable organizations. However, in September 2021, the Health Sector Cybersecurity Coordination Center (HHS) shared a threat advisory warning healthcare organizations of the ransomware group and its preferred method of intrusion, which is unpatched systems.
Figure 4. The top three industries in terms of ransomware file detections in the fourth quarter of 2021
Figure 5. The top three ransomware families affecting the top-ranking industries in the fourth quarter of 2021 (notable family highlighted)
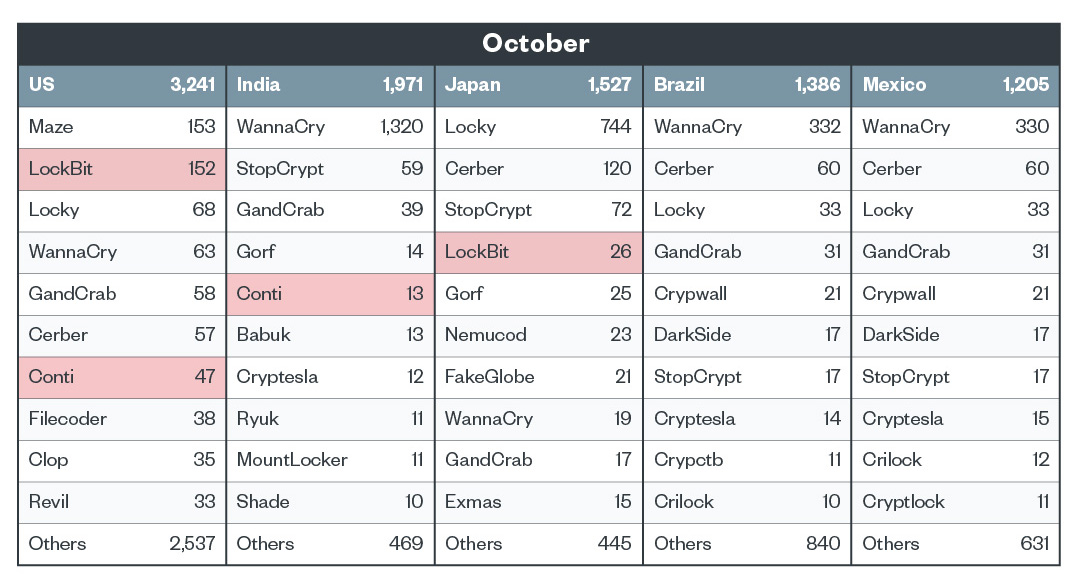
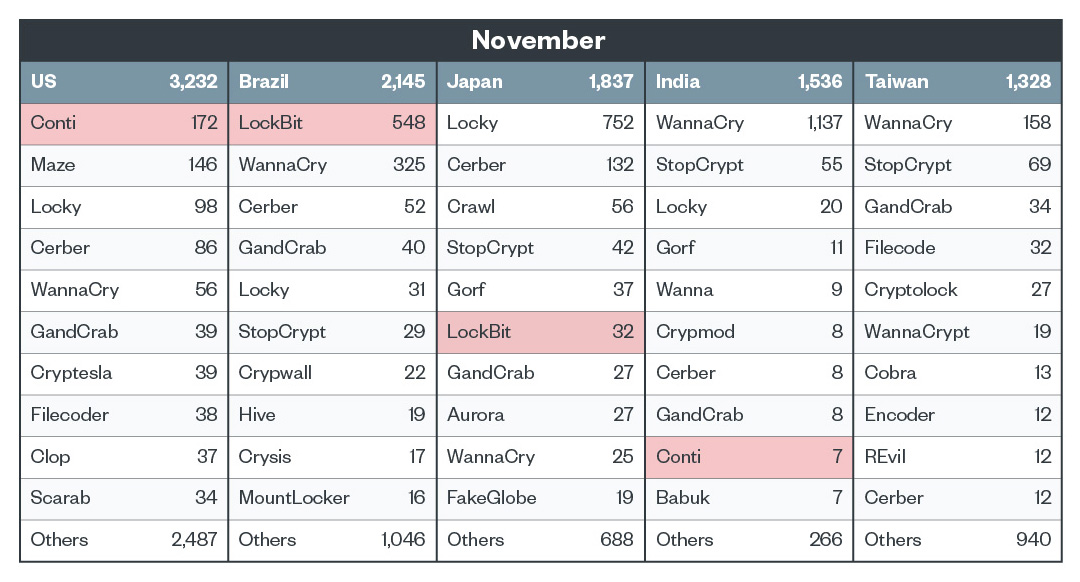
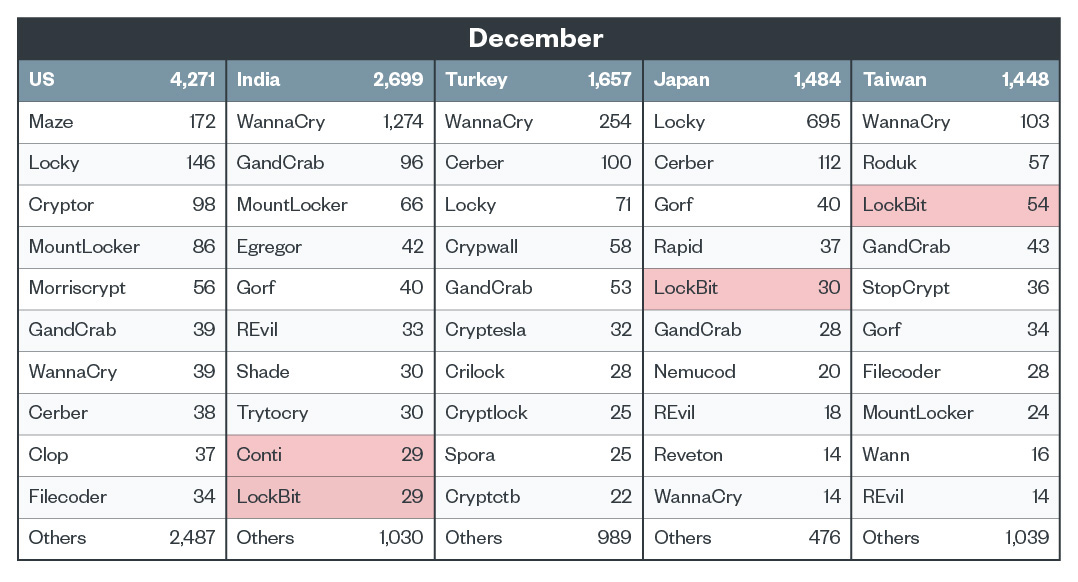
Top five countries with ransomware detections
We observed that Conti, LockBit, Clop, and Maze actors launched attacks in an irregular manner in the fourth quarter, continuing the trend of erratic activity from the third quarter of 2021. However, it should be noted that for the month of November, Conti was the most detected ransomware family in the United States and LockBit topped the list in Brazil.
In Brazil, it can be observed that LockBit wasn’t detected in October but surged in November. Because of the increased number of high-profile attacks waged by LockBit operators, the Brazilian Centre for Prevention, Treatment, and Response to Government Cyber Incidents (CITR) sent an alert pertaining to LockBit ransomware attacks in early December.
In Japan, LockBit actors were seen actively launching attacks throughout the quarter. One notable LockBit attack in the country happened on October 31 at the Handa Hospital in Tsurugi, Tokushima Prefecture. The hospital experienced a LockBit ransomware attack wherein 85,000 patient information and backup data were compromised.
Figure 6. Top 10 ransomware families affecting the top 5 countries in October 2021
Figure 7. Top 10 ransomware families affecting the top 5 countries in November 2021
Figure 8. Top 10 ransomware families affecting the top 5 countries in December 2021
Combating ransomware attacks
Ransomware is a favored payload that actors will continue to use and improve in the coming years. To prevent ransomware attacks from compromising and leaking critical data, enterprises should follow these security recommendations:
- Enable multifactor authentication.
- Be wary of opening unverified emails. Avoid clicking on embedded links, as these can start the ransomware installation process.
- Back up important files. As a rule, organizations should adhere to the 3-2-1 rule: Create three backup copies on two different file formats, with one of the backups in a separate location.
- Always patch and update your systems. It’s important to patch and update all operating systems and applications, and all pertinent software.
Organizations can also benefit from multilayered detection and response solutions such as Trend Micro Vision One™, a purpose-built threat defense platform that provides added value and new benefits beyond extended detection and response (XDR) solutions, allowing organizations to see more and respond faster. Trend Micro Vision One provides deep and broad XDR capabilities that collect and automatically correlate data across multiple security layers — email, endpoints, servers, cloud workloads, and networks — to prevent the majority of attacks with automated protection.
Trend Micro Network One delivers critical network telemetry to Trend Micro Vision One, enabling security operations teams to get a clearer picture of their environment, accelerating response, and preventing future attacks.
Download our ransomware detection data for the fourth quarter of 2021 here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Archive
- Phobos Emerges as a Formidable Threat in Q1 2024, LockBit Stays in the Top Spot: Ransomware in Q1 2024
- Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
- LockBit, BlackCat, and Clop Prevail as Top RAAS Groups: Ransomware in 1H 2023
- LockBit, BlackCat, and Royal Dominate the Ransomware Scene: Ransomware in Q4 2022
- LockBit and Black Basta Are the Most Active RaaS Groups as Victim Count Rises: Ransomware in Q2 and Q3 2022

 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks