Trickbot, Emotet Use Text About Trump to Evade Detection
February 07, 2020
 Threat actors use text from news articles about U.S. President Donald Trump to make malware undetectable. Trickbot samples employing this technique were recently found, while Trend Micro researchers detected Emotet samples using the same method.
Threat actors use text from news articles about U.S. President Donald Trump to make malware undetectable. Trickbot samples employing this technique were recently found, while Trend Micro researchers detected Emotet samples using the same method.
Trickbot’s use of Trump-related text
Trickbot, discovered in 2016, is a banking malware used to steal personally identifiable information (PII). A recent variant of Trickbot can be dropped by Emotet as part of secondary infection.
Vitali Kremez of SentinelLab and security researcher MalwareHunterTeam reported that texts from articles about Trump were used to mask the Trickbot malware. Snippets from an impeachment story by The Independent were lifted and placed under InternalName, FileDescription, and OriginalFileName of one sample. Another took text from a CNN article about Trump’s impeachment, and added them as custom exif data tags.
Kremez said the technique added and appended “goodware” strings to binaries in order to bypass static machine learning engines.
Emotet’s use of the technique
Emotet was discovered by Trend Micro researchers in 2014 as a banking malware family also used to steal PII. At present, the malware has evolved to add more damage inducers in its arsenal; recent versions of Emotet have since been found delivering other malicious payloads and improving their evasion technique.
Trend Micro researchers detected Emotet samples using text from another article about Trump, based on an interview conducted a few hours before this year’s Super Bowl.
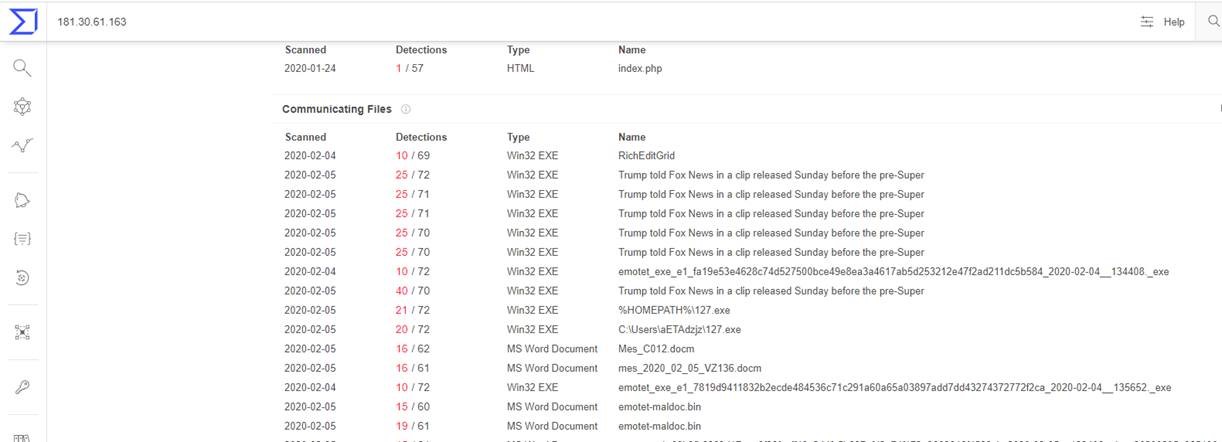
Figure 1. Emotet samples observed by Trend Micro researchers (using Virus Total)
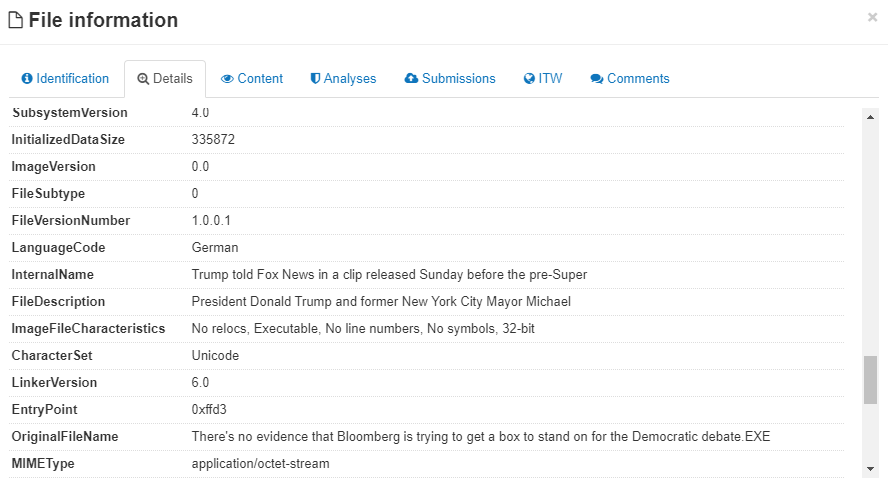
Figure 2. Metadata of a file carrying Emotet malware
Trumping security threats
As cybersecurity experts come up with new ways to strengthen the protection of systems, cybercriminals at the same time learn more ways to circumvent security solutions. To defend themselves and their companies against threats, users should practice good cybersecurity hygiene and do the following:
- Don’t forgo or delay the installation of patches and updates to ensure that even newly discovered vulnerabilities can’t be exploited.
- Observe lags and glitches, especially when they happen frequently. These may be caused by a malware infection.
- Don’t settle for default passwords and security settings. Change and update passwords regularly, and configure security settings depending on specific needs.
- Conduct cybersecurity awareness trainings in your organization or even at home.
- Control access based on the principle of least privilege.
In these particular Emotet and Trickbot campaigns, it is highly likely that the points of entry used are socially engineered emails carrying a malicious attachment, since this is the typical method to propagate both Trickbot and Emotet. Also, the use of recent news to propagate malware has been used as a bait in other attacks before. As a defense from such attacks, users are also advised to closely inspect emails, and to be careful of clicking links and downloading attachments especially from unknown sources.
Further build up the security of systems by employing a multilayered security approach that will protect gateways, endpoints, networks, and servers while allowing centralized visibility and control. Such methods are recommended since threat actors can use any of these layers as entry points, and a threat that affects a single layer usually spreads to other layers soon after as well.
Additional research by Angelo Deveraturda and Raymart Paraiso
Additional research by Angelo Deveraturda and Raymart Paraiso
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks