Soundsquatting 101: How Homophones Can Lead to Risks
 View infographic: Soundsquatting 101
View infographic: Soundsquatting 101
With all the time that we spend on the Internet, whether we’re browsing for answers or information, reading the latest news, or simply connecting with our friends on our social networking sites, it’s easy to get distracted by advertisements, offers, and even viral videos. As such, it isn’t uncommon for cybercriminals to use visual foolery techniques like intentionally misspelling domain names to lead users to fake websites. These sites may contain news hoaxes, fraudulent donations pleas, and spammed messages that ultimately phishes for user information and steals money.
But what happens when we’re tricked into dubious sites unwittingly despite being careful enough? If you've ever tried using voice command software for browsing before, there's a chance you might have been led to a malicious site that has been set up to take advantage of erroneous voice-to-text conversions.
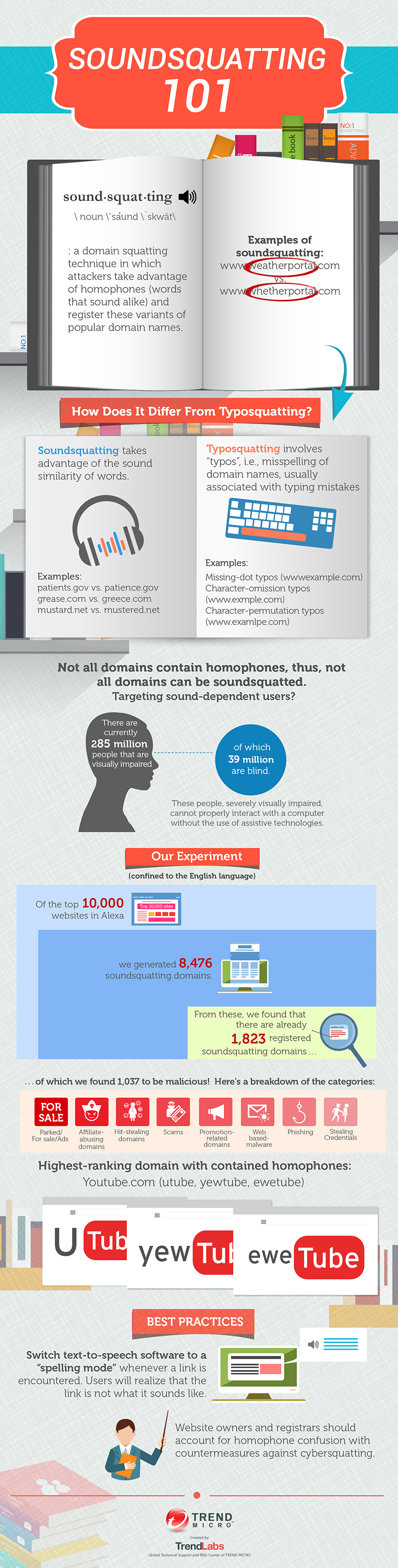
Soundsquatting is a domain squatting technique that takes advantage of homophones, or words that have similar sounds but have a different spelling. Though soundsquatting targets mostly sound-dependent users (most of which are visually impaired), ordinary users are still susceptible to such attacks. Non-native English users for example might search for words that sound similar to one another for example, “wait” when they mean “weight”, could lead them to a malicious site, due to the large proportion of domain variations.
[More: Soundsquatting: Uncovering the Use of Homophones in Domain Squatting]
To avoid these potentially risky mistakes, users who depend on assistive technologies must switch text-to-speech software to a “spelling mode” to allow them to analyze the intended command properly. It’s also better to double-check with another source before clicking on results. Learn more about soundsquatting and how you can avoid unintentionally landing on malicious domains by reading our infographic Soundsquatting 101.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks