ENTSCRYPT aka GermanWiper, SYRK, and STOP Ransomware Variants Usher in August

Three notable ransomware incidents kicked off the first few days of August. Reports of SYRK and STOP ransomware variants encrypting files on infected machines started off the month. Meanwhile, ENTSCRYPT aka GermanWiper, the third and more insidious of the lot, is a fileless ransomware and wiper that makes file retrieval from an infected machine impossible.
Two days before August, our telemetry reported a high number of LNK files that use a PowerShell code to download ENTSCRYPT (detected by Trend Micro as Ransom.Win32.ENTSCRYPT.THHOAAIA) on the machine.![]()
Figure 1. Screen capture of malicious code inside an LNK file
According to ZDNet, GermanWiper is distributed via malicious spam emails containing fake job applications. A ZIP file attached to the spam email contains a malicious LNK file. Once downloaded onto a device, the malware will proceed to overwrite the content of local files with zeroes, making these files unrecoverable. It also changes file extensions to five random alphanumeric characters.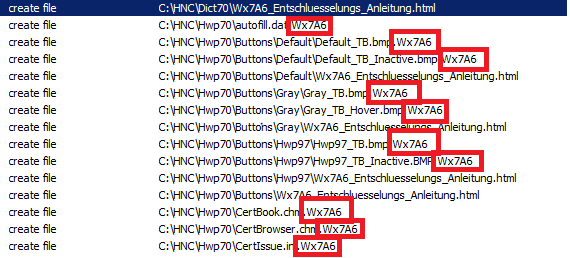
Figure 2. Screen capture of files infected by ENTSCRYPT aka GermanWiper showing the same five-character file extension
Once the files’ contents are rewritten, a ransom note written in German will open on the infected device’s browser, requesting for US$1,500 in bitcoins in exchange for a decryption key.
Victims should be warned, however, that this is a ruse; even if the ransom amount is paid, the rewritten files will no longer be recovered as they have already been permanently overwritten.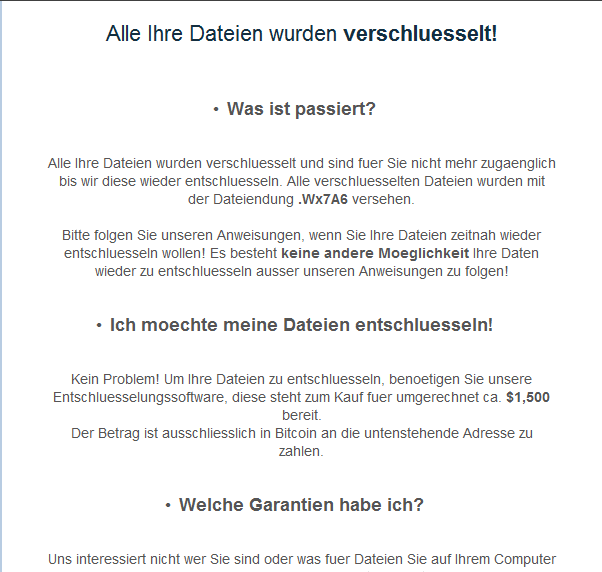
Figure 3. Screen capture of files infected by ENTSCRYPT aka GermanWiper ransom note
Meanwhile, on August 1, The PC Security Channel creator and malware analyst shared on Twitter that the SYRK ransomware (detected by Trend Micro as Ransom.MSIL.SYRK.A) is a variant that may have been inspired by a hacking tool for popular online game Fortnite and is able to terminate Windows’ task manager and the open-sourced tool Process Hacker on an infected device. This ransomware uses the AES algorithm to encrypt data and changes encrypted files’ extensions to .syrk.
The tweet also shared a screenshot of a SYRK-infected device, which showed that SYRK also comes with a timer and a warning that informs users that their files will be deleted in three separate batches if ransom is not paid within the specified time frame. The first batch will delete files in the Pictures folder, the second will delete files saved on the Desktop, and the third will delete files in the Documents folder.
Just a day after, ransomware hunter and creator of ID-Ransomware Michael Gillespie discovered a STOP ransomware variant that encrypts files and changes the files’ extensions to .cosakos (detected by Trend Micro as Ransom.Win32.STOP.AN).
After further analysis, we saw that this STOP ransomware variant has a two-stage unpacking process before it decrypts its resources in a host machine using the “0x80” XOR encryption. Interestingly, this variant will terminate and delete itself on devices that have IP addresses from the following countries:
- Armenia
- Azerbaijan
- Belarus
- Kazakhstan
- Kyrgyzstan
- Russia
- Syria
- Tajikistan
- Ukraine
- Uzbekistan
Defending against ransomware
There has been a recent uptick in ransomware attacks, with the threat wreaking havoc in public sectors, local governments, and private companies, to name a few. When facing a ransomware attack, law enforcement and security experts discourage paying ransom, as it is a temporary solution against the threat. Additionally, paying ransom does not always ensure that cybercriminals will deliver on their promise, as in the case of GermanWiper.
Instead, enterprises are advised to employ adequate security measures to defend against ransomware attacks or, at the very least, mitigate their effects should one slip past defenses. Users and organizations can also follow these best practices to defend against ransomware infections or mitigate impact:
- End users should be wary of suspicious emails, URLs, or attachments that cybercriminals still use to deliver different malware variants.
- Regularly back up important files to make sure that data and information would remain available in the case of a ransomware attack.
- Restrict access to critical tools like administration tools and files to authorized personnel.
- Regularly update and patch software, programs, and applications to protect against cyberattacks that exploit vulnerabilities.
Trend Micro’s security solutions powered by machine learning
Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques. It uses machine learning technology to proactively and efficiently detect the maliciousness of previously unknown file types, ensuring that data centers, cloud environments, networks, and endpoints are protected against a full range of threats.
| Ransomware | SHA-256 Hashes | Trend Micro Predictive Machine Learning Detection | Trend Micro Pattern Detection |
| STOP | 26d5eaad09fc158b8bd16dab763af9f6faf17860936309451b5165da263242de | Troj.Win32.TRX.XXPE50FFF031 | Ransom.Win32.STOP.AN |
| SYRK | 077eee74b8f1227707b389a953234756d3bf8b78108a24f132bd5feb209dd8f6 | Ransom.MSIL.SYRK.A | |
| ENTSCRYPT/ GermanWiper | 0d115ba578ab98415697a815d93c6dddc4483fa13d65992660722fc8af8cd792 | Ransom.Win32.ENTSCRYPT.THHOAAIA | |
| ENTSCRYPT/ GermanWiper (LNK) | c816626c0ac50667a076783336530eeb6104f7ba866141491de66b1abaad083b | Trojan.LNK.POWLOAD.THHOAAI | |
| ENTSCRYPT/ GermanWiper (VBS) | e77447114c2261f0b0e19f8430cba22c1e27da1f0ac44ffbe9ba94cc6706846a | Trojan.VBS.DLOADER.THHOAAI |
Additional analysis from Sylvia Lascano, Jeanne Jocson, Raphael Centeno, and Earle Earnshaw.
Updated as of August 6, 2019 at 9:37 a.m. PDT to reflect a change in the Trend Micro pattern detection for the ENTSCRYPT ransomware/wiper
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks