Who Is Really Attacking Your ICS Devices?
Industrial Control System (ICS)/SCADA systems have been the talk of the security community for the last three or more years due to Stuxnet, Duqu, and other similar noteworthy attacks. While the importance and lack of security around ICS systems are well documented and widely known, I’ve been researching Internet-facing ICS/SCADA systems, who’s really attacking them, and why. Recently, I spoke at BlackHat Europe about the same research and wrote a research paper to share my findings.
Without knowing if Internet-facing SCADA systems were attacked, I developed a honeypot architecture that would emulate several types of SCADA and ICS devices mimicking those commonly found on these systems. The honeypots included traditional vulnerabilities found across the same or similar systems, showcasing a very realistic honeypot environment.
The findings include real-world attacks from several countries with varying attack attempts.
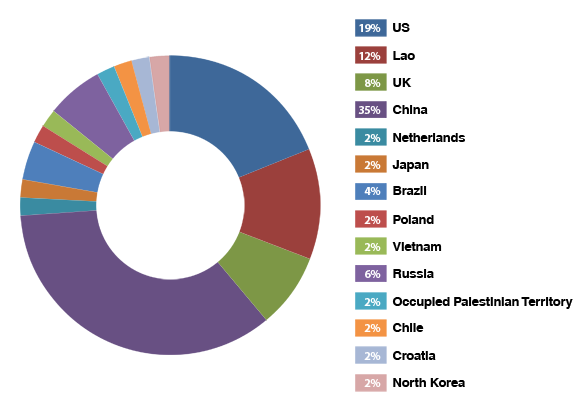
Figure 1. Percentage of attacks per country
In addition to the statistics gathered about the source of attacking country, my research includes some specific vulnerabilities that threat actors attempted to exploit. Included in some of the attacks I found were an attempt to spearphish a site administrator and a bid to exploit fundamental ICS protocols.
Our expectation is that attack trends will continue to increase in the ICS arena, with possible far reaching consequences. With continued diligence and utilizing secure computing techniques, your ability to deflect and defend these attacks will help secure your organization. For more information about these findings, you may read my report “Who’s Really Attacking Your ICS Equipment?” and find out details of some of these attacks and who are some primary offenders.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks