PHP_WEBSHELL.YWD
Windows


Threat Type: Backdoor
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This backdoor may be hosted on a website and run when a user accesses the said website.
It executes commands from a remote malicious user, effectively compromising the affected system.
It retrieves specific information from the affected system.
This is the Trend Micro detection for files that contain a malicious script.
TECHNICAL DETAILS
Arrival Details
This backdoor may be hosted on a website and run when a user accesses the said website.
Backdoor Routine
This backdoor executes the following commands from a remote malicious user:
- Execute cmd commands
- Execute Files
- Delete File
- Upload File
- Download File
- Edit File
- View File
- Rename File
- Change File Permission
- Create File
- Create Directories
- Enable Safe mode
- Delete itself
- Terminate itself
Information Theft
This backdoor retrieves the following information from the affected system:
- Computer Name
- User Name
- Group Name
- PHP Version
- Computer Mode (Safe Mode on or off)
- IP address
- Server IP address
- Hard Drive Total Space
- Hard Drive Free Space
- Operating System
- Downloader being used
- Disabled Functions
- PHP Configuration
- Disk Drives present
- Servers present
- Display information located on symlink file (For Linux)
- If the following servers are turned on:
- cURL
- MySQL
- MSSQL
- PostgreSQL
- Oracle
- Directories of the following (For Linux):
- Open_basedir
- Safe_mode_exec_dir
- Safe_mode_include_dir
- Complete file directory for all disk drives including:
- File Name
- File size
- Last modified date
- Number of Owners/Group
- File Permissions
- The following System Information:
- Host Name
- OS Name
- OS Version
- OS Manufacturer
- OS Configuration
- OS Build Type
- Registered Owner
- Registered Organization
- Product ID
- Original Install Date
- System Boot Time
- System Manufacturer
- System Model
- System Type
- Processor(s)
- BIOS Version
- Windows Directory
- System Directory
- Boot Device
- System Locale
- Input Locale
- Time Zone
- Total Physical Memory
- Available Physical Memory
- Virtual Memory Max Size
- Virtual Memory Available
- Virtual Memory In Use
- Page File Location(s)
- Domain
- Logon Server
- Hotfix(s)
- Network Card(s)
- Running Windows Services in infected machine
- User accounts in infected machine
- ARP Table of the infected machine
- IP Configuration of the infected machine
Other Details
This is the Trend Micro detection for files that contain a malicious script.
NOTES:
This malware has other capabilities:
- Base64 encryption/decryption
- URL encryption/decryption
- Full URL encryption
- Generate md5 hash
- Generate sha1 hash
- Generate crypt hash
- Generate CRC32 hash
- Generate html formatted special characters
- Use 'eval' function
- Access SQL Database
- UDP Dossier for DDOS attacks
- Back connection for PERL and PHP threads(need ip and port)
- Provide3 a portal to report defaced websites to Zone-H
**Zone is an archive of defaced websites.
Upon execution, the backdoor will show the following:
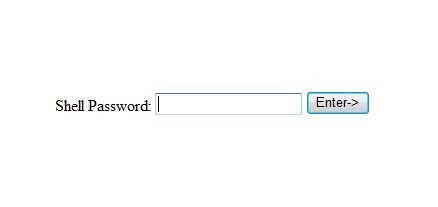
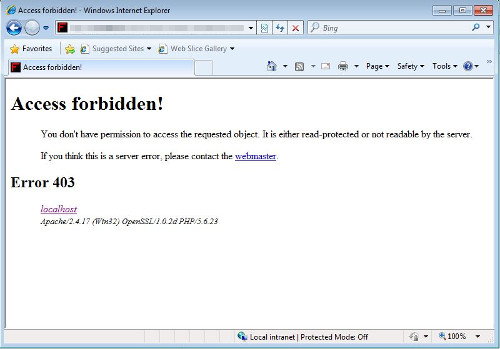
It shows the following if the incorrect password used:
Once the correct password is used, it will direct the user to the GUI below.
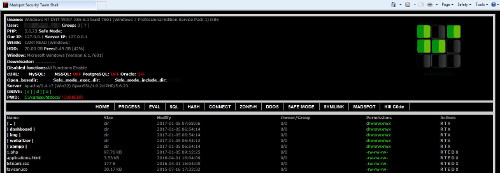
This gives the user access to the backdoor capabilities of the malware.
The backdoor is based from the Madspot Security Team Shell ver. 1.
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Close all opened browser windows
Step 3
Scan your computer with your Trend Micro product to delete files detected as PHP_WEBSHELL.YWD. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


