STUXNET Malware Targets SCADA Systems
October 01, 2010
What is STUXNET?
STUXNET is a worm that initially made news in July due to its use of certain vulnerabilities to propagate and execute its routines. The media, as well as the security industry, have taken interest in this threat since its emergence. This is primarily due to new findings suggesting that STUXNET is not just another run-of-the-mill malware, but is instead one designed to target critical infrastructures.
What does STUXNET do?
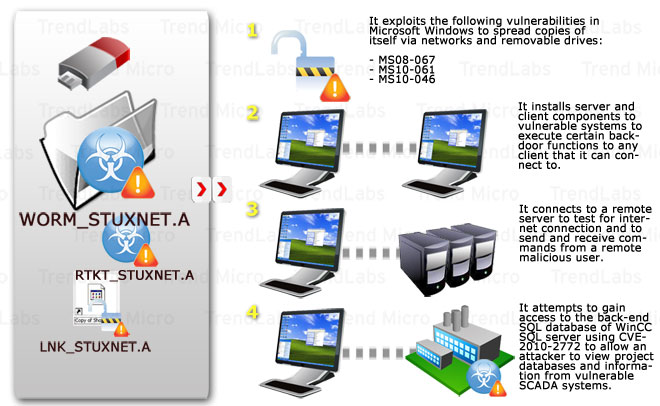
STUXNET has three components that work in concert—a worm, an .LNK file, and a rootkit.
WORM_STUXNET—The worm executes all routines related to the main payload of the attack. It uses certain vulnerabilities for its propagation and execution of certain routines. It implements a Microsoft Remote Procedure Call to execute certain functions, enabling affected systems to communicate with one another. It also tests for an active Internet connection on the affected system to communicate with a remote server. It is also the component responsible for attempting to access a database consistent with one used in Siemens WinCC systems.
LNK_STUXNET—This specially crafted .LNK file automatically executes the propagated copies of WORM_STUXNET. It exploits a vulnerability in the way Windows displays the icons of shortcut files and is basically employed by STUXNET for automatic execution.
RTKT_STUXNET—This rootkit component is mainly responsible for hiding all malicious files and processes. This is done in order to keep the infection from being traced by the user.
How does STUXNET propagate? What vulnerabilities were used?
One reason why STUXNET has become such a problem is the fact that it uses multiple means to propagate:
Note: All of these vulnerabilities have been patched, which means that patched systems cannot be easily infected. MS10-061 can only be exploited if anonymous users are allowed to use shared printers. By default, this was the case in Windows XP but not later versions of Windows. The shortcut vulnerability was the most exploitable, as trying to access the removable drive in any way would have been sufficient to trigger the vulnerability.
In addition, STUXNET uses two currently unpatched vulnerabilities in Windows to gain administrator rights on a system. The Windows shortcut vulnerability only runs code with the same privileges as the current user; using these two vulnerabilities ensures that this malware has the same rights as an administrator of the system.
How does STUXNET use P2P?
STUXNET installs both server and client components for a Microsoft Remote Procedure Call in all infected system by exploiting the MS08-067 vulnerability. This enables the affected system to execute the following functions into any client that it can connect to:
STUXNET is a worm that initially made news in July due to its use of certain vulnerabilities to propagate and execute its routines. The media, as well as the security industry, have taken interest in this threat since its emergence. This is primarily due to new findings suggesting that STUXNET is not just another run-of-the-mill malware, but is instead one designed to target critical infrastructures.
What does STUXNET do?
STUXNET has three components that work in concert—a worm, an .LNK file, and a rootkit.
WORM_STUXNET—The worm executes all routines related to the main payload of the attack. It uses certain vulnerabilities for its propagation and execution of certain routines. It implements a Microsoft Remote Procedure Call to execute certain functions, enabling affected systems to communicate with one another. It also tests for an active Internet connection on the affected system to communicate with a remote server. It is also the component responsible for attempting to access a database consistent with one used in Siemens WinCC systems.
LNK_STUXNET—This specially crafted .LNK file automatically executes the propagated copies of WORM_STUXNET. It exploits a vulnerability in the way Windows displays the icons of shortcut files and is basically employed by STUXNET for automatic execution.
RTKT_STUXNET—This rootkit component is mainly responsible for hiding all malicious files and processes. This is done in order to keep the infection from being traced by the user.
How does STUXNET propagate? What vulnerabilities were used?
One reason why STUXNET has become such a problem is the fact that it uses multiple means to propagate:
- First, it uses the MS10-046 Windows shortcut vulnerability (CVE-2010-2568), which allowed it to spread via removable drives even if Autorun is disabled.
- Second, it used the MS08-067 vulnerability (CVE-2008-4250) to spread via the network the same way DOWNAD/Conficker did.
- Third, it used the MS10-061 Printer Spooler vulnerability (CVE-2010-2729) to spread via networks, if a system shared a printer over the network.
Note: All of these vulnerabilities have been patched, which means that patched systems cannot be easily infected. MS10-061 can only be exploited if anonymous users are allowed to use shared printers. By default, this was the case in Windows XP but not later versions of Windows. The shortcut vulnerability was the most exploitable, as trying to access the removable drive in any way would have been sufficient to trigger the vulnerability.
In addition, STUXNET uses two currently unpatched vulnerabilities in Windows to gain administrator rights on a system. The Windows shortcut vulnerability only runs code with the same privileges as the current user; using these two vulnerabilities ensures that this malware has the same rights as an administrator of the system.
How does STUXNET use P2P?
STUXNET installs both server and client components for a Microsoft Remote Procedure Call in all infected system by exploiting the MS08-067 vulnerability. This enables the affected system to execute the following functions into any client that it can connect to:
- Get malware version
- Receive module and inject it
- Send the malware file
- Create a process that could be command shell or a file
- Create a file
- Delete a file
- Read a file
Universally Unique Identifier
(
UUID
) 000204e1-0000-0000-c000-000000000046. Using the said identifier enables systems affected by STUXNET to identify, communicate with, and update one another.
Does STUXNET try to contact a remote server?
Yes. In attempting to connect with a remote server, STUXNET first tests for an active Internet connection by connecting to the following non-malicious URLs:
- www.windowsupdate.com
- www.msn.com
After a connection is established, it then connects to the following URL(s) to send and receive commands from a remote malicious user:
- www.{BLOCKED}erfutbol.com
- www.{BLOCKED}futbol.com
- http://www.{BLOCKED}erfutbol.com/index.php?data={data}
Where {data} is an encrypted hex value that contains the IP address of the machine, computer name, and domain.
How does STUXNET relate to SCADA systems?
The nature of STUXNET confirms the idea that this malware was not initially designed just to target common users' systems.
Analysis revealed that WORM_STUXNET.A looks for the legitimate .DLL file S7OTBXDX.DLL used by Siemens WinCC systems in the Windows system folder. Once found, it renames the said file to S7OTBXSX.DLL and then drops a modified .DLL file to replace the original .DLL file. The new .DLL will have the same exports as the original but with code modifications on the following functions:
- s7db_open
- s7blk_write
- s7blk_findfirst
- s7blk_findnext
- s7blk_read
- s7_event
- s7ag_test
- s7ag_read_szl
- s7blk_delete
- s7ag_link_in
- s7db_close
- s7ag_bub_cycl_read_create
- s7ag_bub_read_var
- s7ag_bub_write_var
- s7ag_bub_read_var_seg
- s7ag_bub_write_var_seg
These functions are generally used to access, read, write, and delete code blocks on the PLC. In an infected system, when these functions are called, STUXNET will execute additional codes before calling the true function in S7OTBXSX.DLL . By intercepting these functions, we can say that it can modify the data sent to or received from the PLC.
It also scans the system for certain processes related to security software. It then attempts to inject itself into the said routines.
Once fully installed into the system, STUXNET exploits the Siemens SIMATIC WinCC Default Password Security Bypass Vulnerability to gain access to the back-end SQL database of the WinCC SQL server. More information can be found below:
- CVE-2010-2772 Siemens SIMATIC WinCC Default Password Security Bypass Vulnerability
This enables the attacker to view the projects database and information from the WinCC server. It can alter configuration settings and can access or delete the file %ALL USERS PROFILE%\sqlx.dbi. Since .DBI files are database explorer information files, this deletion is most likely done to remove any trace of modification done by the malware in the database.
Was this a targeted attack against someone or something?
That appears to be the case. The PLC commands that form one of the primary payloads of STUXNET are designed to execute only on systems with very specific hardware configurations. Therefore, we can surmise that the authors of STUXNET knew that their target possessed this specific configuration.
Who was the target?
We don't know. No one has come forward and admitted that they were the targets of STUXNET, and short of finding out the exact hardware configuration of every SCADA system in the world we cannot be sure. Speculation pointing to Iran as the likely target is just that—speculation. The large number of STUXNET infections in that country may merely be a consequence of other factors. Trend Micro has noted that countries with high reports of STUXNET infection also had high rates of DOWNAD/Conficker infection.
Who was behind the attack?
No one knows. We know even less about who could have written STUXNET than the target. Portions of STUXNET’s code that suggest authorship are vague at best. There is nothing in the code that could be taken to be a definitive link to anyone.
What we do know is that whoever was behind it had good knowledge of SCADA systems, particularly those they targeted. In addition, using so many unpatched vulnerabilities in just one malware family is unheard of outside STUXNET, again suggesting that whoever wrote STUXNET was more sophisticated than the typical cybercriminal.
What was the motive of these attacks?
Without better knowledge of the persons behind these attacks, it's near impossible to say with any certainty who was responsible. The combination of sophisticated attacker and target means that any guess as to who was behind this is nothing more than speculation.
However, the implications of STUXNET being able to modify commands sent to SCADA systems are significant. Industrial systems under SCADA control that were targeted by STUXNET could be damaged or outright destroyed, depending on the modified commands sent by the cybercriminals.
How should users react?
Home and enterprise users without SCADA systems are at relatively little risk. The largest risk for them lies in attacks that are unrelated to the original STUXNET attack, but instead use it as springboard for something else. For example, soon after the Windows shortcut vulnerability was found in STUXNET, more conventional malware families like ZBOT and SALITY soon made use of it. Recent news coverage has also encouraged cybercriminals to use STUXNET as a social engineering bait. Blackhat search engine optimization (SEO) efforts are now using multiple FAKEAV "file scanner" campaigns that use STUXNET-related search terms on Google and other search engines.
For enterprise users that do have SCADA systems, this would be a good time to re-consider existing security policies regarding these systems. At the very least, these systems should be updated to guard against vulnerabilities, as well as antivirus clients to guard against similar threats that will come in the future.
We have discussed the issues of SCADA security in detail long before STUXNET became an issue:
What are Trend Micro's solutions?
The Trend Micro
Smart Protection Network™ protects against all components of the STUXNET threat. The new Web-based attacks are blocked using the Web reputation technology. All of the file components are detected using the file reputation technology. The cloud-client architecture ensures that all of our customers are protected immediately, regardless of where they connect—from home, on the road, or within their network.
Below are the current files detected by Trend Micro:
- LNK_STUXNET.A
- LNK_DLOADER.SMR
- LNK_STUXNET.C
- EXPL_CPLNK.SM
- WORM_STUXNET.A
- WORM_STUXNET.SM
The rootkit component is similarly detected as RTKT_STUXNET.A.
In addition, Trend Micro offers virtual patching for the vulnerabilities used in this attack with Deep Security and OfficeScan with the Intrusion Defense Firewall (IDF) plug-in, which are able to prevent network propagation of STUXNET files.
Find out if you are infected
- HouseCall Free Malware Scan
- Trend Micro Internet Security Free Trial (for consumers)
- Worry Free Business Security Free Trial (for small businesses)
- OfficeScan Free Trial (for enterprises)
- Register for Free Onsite Security Threat Assessment (for enterprises)