Spammers Leverage Different Google Services for Phishing Attack
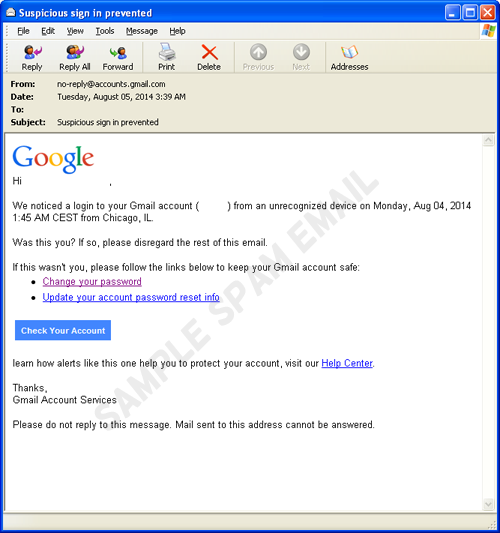
Gmail users are the target of a spam attack that took advantage of several Google services. While the attack tries to pass off as a legitimate Google notification, a closer look reveals that this fake Gmail notice can lead to malware.
The spammed message looks normal at first glance. The From field indicates the address no-reply@accounts.gmail.com but double checking the header will lead you to a “webmailer” account that has nothing to do with Gmail.
The message notifies the user about the associated Google account being accessed from an unrecognized device. It then asks the user to change his password or update his password reset information. However, the links redirects to a page hosted in yet another free Google service—this time, on Google Drive. It should be noted that even the Check Your Account button and the Help Center links also redirect to a page hosted in Google Drive.
Aside from Gmail and Google Drive, the landing page of these malicious links actually copied the Google Chrome Update Plug-in page. Clicking on “Accept and Install” will download the executable file Chrome_Plug-in_EN-US_WOL_WIN.exe. This file is detected by Trend Micro as BKDR_PERCS.A.
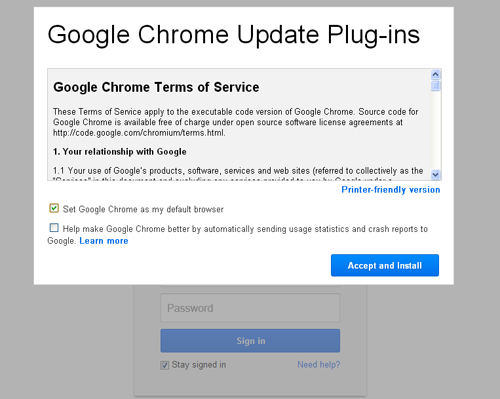
Based on the services used in this attack, it appears that the spammers are targeting Gmail users. Given that Google implements a unified account across all its services, it would be easier for the spammers to phish single information and use it to log in other Google products and services.
We advise users to be cautious, especially with emails concerning account settings and account information. For notifications like this one, it is best to visit the actual site—and not rely on the provided links—to double-check the security settings.
Trend Micro blocks all related threats in this attack.
- ENGINE:7.5
- PATTERN:0868
