
Our full midyear roundup report, “Unseen Threats, Imminent Losses,” gives deeper insight into the most notable threats of the first half of 2018.
Stealthy and subtle — two common characteristics of the major cybersecurity threats we found in the first half of 2018. The year started off rocky when, in January, serious design flaws were discovered in popular microprocessors previously assumed to be secure. Throughout the next few months, we also saw a noticeable shift away from highly visible ransomware to a more discreet detection: cryptocurrency mining. There was also a rise in “fileless” malware and other threats using nontraditional evasion techniques, as well as an increasing number of data breaches and social engineering email scams.
These damaging threats — from the miners that quietly leech power from victims’ devices to the serious vulnerabilities that leave machines open to covert attacks — split limited security resources and divide the focus of IT administrators.
In this report, we dive into the first six months of 2018 to find the top emerging threats that enterprises should stay ahead of.
Serious vulnerabilities discovered in hardware make patching even more challenging
The year opened with the disclosure of Meltdown and Spectre, two major design flaws in popular microprocessors. The impact of these vulnerabilities was exacerbated by the huge number of devices affected and the level of access they could allow attackers to have. These were only the beginning as more vulnerabilities were found and patched following the announcement.

Hardware vulnerabilities present a complicated problem for IT admins. Since microprocessors from multiple vendors are affected and vulnerability fixes are released over an extended period, applying firmware patches across all affected devices is more difficult. In addition, some of the patches affect the system performance of older devices, compounding the impact on business operations.
Along with these hardware problems, IT admins also had to deal with vulnerabilities disclosed by major software vendors. Major vendors release regular patches as disclosed vulnerabilities are found and fixed, but enterprises still have difficulty securing their networks. The volume of vulnerabilities and the pressure to keep networks operational make patching a perennial problem for administrators.
Trend Micro ZDI published
602
advisories in 1H 2018
23
published without patches or
mitigation at the time of advisory
SCADA vulnerability advisories increase
Total reported SCADA vulnerabilities:
30%
increase from 2H 2017
The number of reported vulnerabilities related to supervisory control and data acquisition (SCADA) systems increased since the second half of 2017, and many of these vulnerabilities were found in human-machine interface (HMI) software. The SCADA HMI is the main digital hub that manages critical infrastructure, and the data it shows has some reconnaissance value for attackers.
SCADA ZERO-DAYS WITH NO PATCH WHEN DISCLOSED
77%
decrease from 2H 2017
Our data also indicates that more vendors were able to create patches or mitigation methods in time for the corresponding vulnerability announcements. While this is a welcome improvement, the sheer number of discovered vulnerabilities highlights why enterprises in critical infrastructure sectors should stay on top of SCADA software systems and invest in multilayered security solutions. The European Union (EU), through the Network and Information Security (NIS) Directive, has already mandated its member states to enact laws that ensure a heightened level of security for critical sectors and essential digital services.
The NIS Directive
- EU legislation that affects organizations operating critical infrastructures. With the directive and corresponding national laws in force, operators in essential sectors must have appropriate, proportionate, and state-of-the-art measures to secure network and information systems, among other risk mitigation policies.
- What enterprises are affected?
- Power plants
- Water facilities
- Banks
- Hospitals
- Transportation
companies - Online
marketplaces - Cloud computing
services - Search
engines
Cryptocurrency mining detections more than doubles while ransomware remains an enterprise threat
We noted in our 2017 annual roundup report that cryptocurrency-mining activity was on the rise. That trend continued in the first half of 2018, with detections of cryptocurrency-mining activity more than doubling from 2H 2017. We also detected a significant number of new cryptocurrency miner malware families, showing that cybercriminals remained keenly interested in profiting from digital currencies.
141%
increase in cryptocurrency-mining activity detections by Trend Micro™ Smart Protection Network™ infrastructure
47
1H 2018
New cryptocurrency miner
malware families detected
Throughout the first few months of 2018, we noted how cybercriminals devised new methods and explored new techniques to maximize the profit from illicit cryptocurrency mining.
- JanMalvertising in Google's DoubleClick
- FebAds injected by Droidclub botnet into websites
- MarAdware downloader ICLoader
- AprWeb miner script in AOL ad platform
- MayCVE-2017-10271 via port 7001/TCP
- JunNecurs exploit kit
Unwanted cryptocurrency miners on a network can slow down performance, gradually wear down hardware, and consume power — problems that are amplified in enterprise environments. IT admins have to keep an eye out for unusual network activity considering the stealthy but significant impact cryptocurrency mining can have on a system.
Though its prevalence in the cybersecurity landscape has plateaued, ransomware is still something that enterprises should be vigilant against.
In the first half of 2018, ransomware detections saw only a slight increase while the number of new ransomware families declined, compared to the second half of 2017. But this change of pace is likely due to the increased attention on ransomware and the resulting improvements in prevention and mitigation methods.
3%
increase in detected
ransomware activity
26%
decrease in new
ransomware families
Mega breaches rise even as GDPR penalties loom
Using the relevant 2017 and 2018 data sets from Privacy Rights Clearinghouse, we saw a 16-percent increase in reported U.S.-based data breaches.
Reported breaches in the U.S.
224
2H 2017
259
1H 2018
It was interesting to see that the number of incidents due to unintended disclosures was higher, albeit only slightly, than that due to hacking.
- Unintended disclosure
- Hacking or malware
- Physical loss
- Others (insider, unknown, etc.)
Fifteen of the 1H 2018 data breaches were mega breaches, that is, each exposed at least one million records. In terms of number of incidents, the healthcare industry suffered the most breaches, but most of the mega breaches were from retailers and online merchants. We also found at least nine breaches outside the U.S. that could be considered mega breaches.
increase in the number
of mega breaches in the U.S.
71%
of breaches were from
the healthcare industry
There are substantial consequences for enterprises that are hit by data breaches. Recovery and notification costs, revenue losses, patching and downtime issues, and potential legal fees can add up: A mega breach can cost companies up to US$350 million. Also, many countries are establishing new data privacy regulations that impose hefty fines for improper data management.
The EU in particular has taken a strong stance on privacy by implementing one of the toughest and most extensive data protection laws in the world: the General Data Protection Regulation (GDPR). This regulation, enforced in May this year, sets a high bar for data security and privacy protection. It imposes considerable fines for noncompliant organizations: Penalties could reach up to €20 million or 4 percent of the noncompliant company’s global annual turnover, whichever is higher. Moreover, it has quite a long reach since any organization holding EU citizens’ data is affected.
GDPR – Are you compliant?
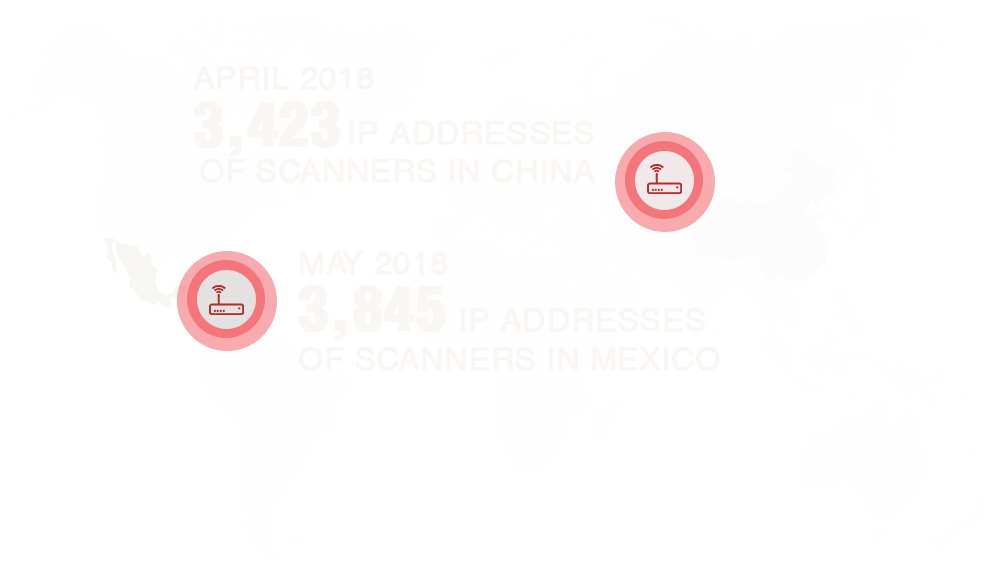
Router security still weak despite Mirai alert
In the first half of 2018, we observed that routers were being explicitly targeted, an indication that homes and businesses remained open to network-based attacks. This is particularly dangerous because if a router is compromised, then anything and everything connected to it can be attacked as well — laptops, smartphones, smart assistants, and other internet-of-things (IoT) devices.
We detected Mirai-like scanning activity looking for vulnerable routers and IoT devices. In 2016, Mirai was responsible for record-breaking distributed denial-of-service (DDoS) attacks. Since the release of its source code in October that year, cybercriminals have been using it for other malicious activities.
Fileless, macro and small-sized malware challenges purely file-based security technologies
To persist against continually improving detection techniques, malware developers are constantly fine-tuning their evasion methods. In the first half of 2018, a few approaches stood out: using fileless threats, using macros, and manipulating file sizes.
Typical threats involve malicious files that are installed and executed in the compromised device. Fileless threats don’t operate that way. Instead, they hijack trusted tools that are built into the operating system to carry out the attacks.
Fileless events detected
24430
Jan
38189
Jun
1H 2018
We detected a rising trend in the number of fileless threats throughout the first half of the year. Enterprises can stay ahead of these threats by deploying integrated layers of protection across the network.
We also saw an uptick in the use of malicious macros. Powload was the most pervasive culprit and, like most malicious macros, it was being sent through spam. The spam email is crafted in such a way that manipulates users into enabling the macro and downloading the malware payload.
Macro
6%
increase from Jan to Jun
POWLOAD
68%
increase from Jan to Jun
We also detected a steep increase in detections of a point-of-sale (POS) malware family called TinyPOS. This could be partly due to the source code release of TreasureHunter, another POS malware family, as we often see a spike in similar or related malware when there is a source code leak. The extremely small file size of TinyPOS is most likely a characteristic cybercriminals used to try and evade detection.
TinyPOS DETECTIONS
BEC losses exceed projection as BEC attempts exhibit steady growth
Business email compromise (BEC) scams are quite straightforward, relying more on open-source intelligence and social engineering than high-level technical expertise. In a typical BEC scheme, a scammer impersonates a high-ranking executive and tricks an employee (usually one connected to the finance department) into transferring funds to the scammer’s account. Because BEC scams require relatively fewer resources and yet could yield high payouts, we predicted that losses would exceed US$9 billion this year.
MORE THAN
US$9BPREDICTION
ACTUAL
2018 TREND MICRO PREDICTION VS ACTUAL CUMULATIVE
GLOBAL BEC LOSSES
A report by the Federal Bureau of Investigation (FBI) on BEC and email account compromise (EAC) shows just how severe the problem has become for businesses: Accumulated global losses (from October 2013 to May 2018) have reached US$12.5 billion.
We have been actively tracking BEC attempts, and our data shows an increase in the last 12 months.
5%
INCREASE IN RECORDED BEC ATTEMPTS FROM 2H 2017 TO 1H 2018
To prevent email-based threats, enterprises need to look beyond file-based detection and consider email reputation technologies. For BEC scams in particular, solutions using machine learning add a new layer of protection by, for example, analyzing a user’s writing style to identify if an email is genuine or not.
THREAT LANDSCAPE
20,488,399,209
Overall threats blocked in 1H 2018
CHANGES IN VULNERABILITIES FOUND PER VENDOR (2H 2017 vs. 1H 2018)
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks