Unmasking Pig-Butchering Scams and Protecting Your Financial Future
WHAT IS A PIG-BUTCHERING SCAM?
A pig-butchering scam is a type of investment fraud that lures individuals into investing their money in seemingly legitimate and profitable ventures. Typically, the scammers promise high investment returns within a short period. Pig-butchering scammers often use fake images and impressive-yet-fraudulent investment portfolios to convince victims of the legitimacy of their schemes. Once victims are hooked and have invested a significant amount of money, the scammers suddenly disappear, leaving victims with no way to recover their funds. The term "pig butchering" is derived from the idea that the scammers fatten up their victims with the promise of lucrative returns before "slaughtering" them for their money.
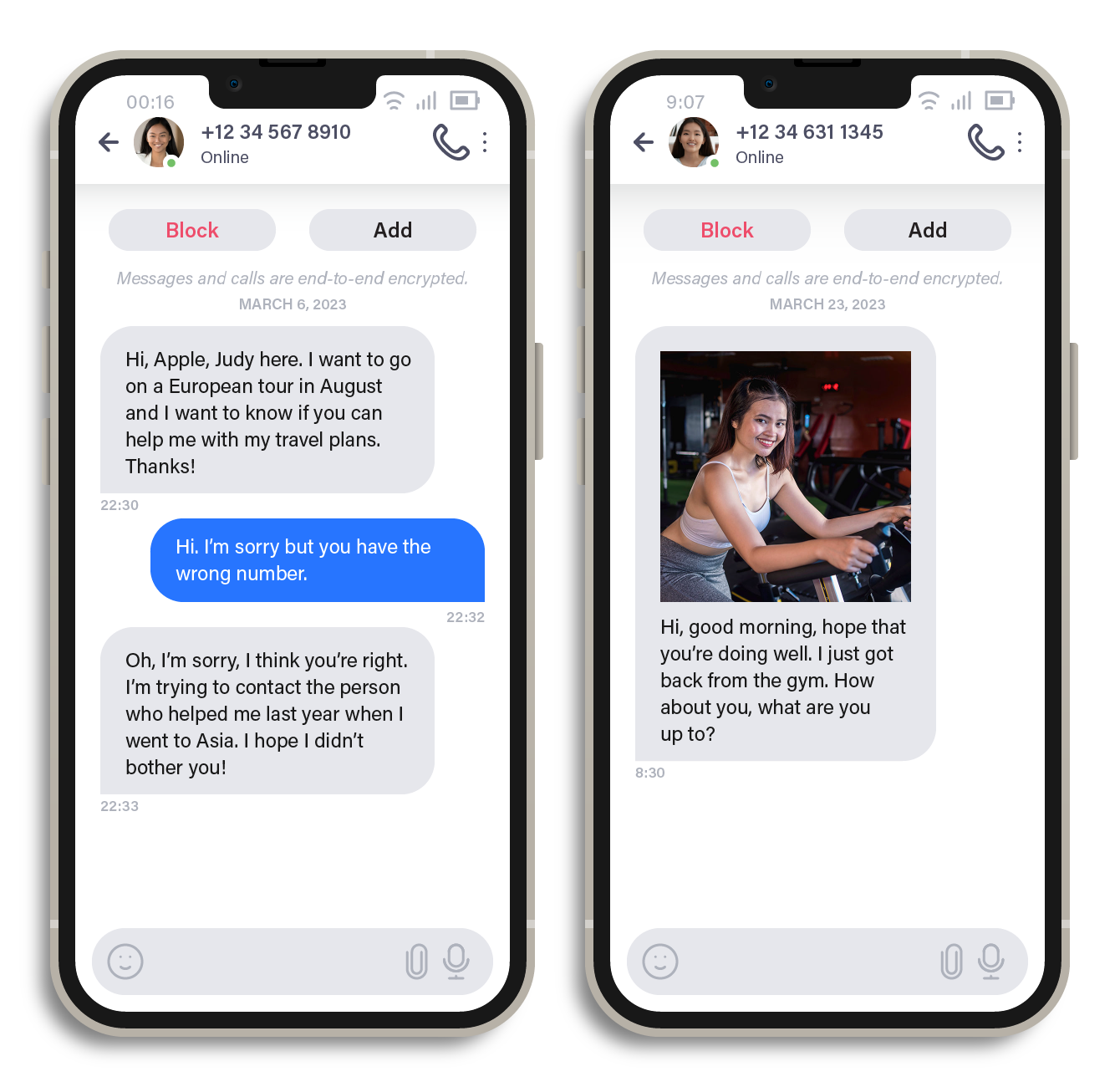
The scam often begins with a seemingly innocent chat initiated by a random person. The scammer might claim to have received the victim's number from a mutual friend, while also appearing unsure if they have the correct number. However, this is just an act to engage the victim in conversation. Scammers have also been known to use images of attractive women to lure victims, preying on their desire for companionship or romance to build trust and establish a connection.
Figure 1. Initial conversations wherein a scammer used a seemingly innocuous introduction for one victim and a stolen photo for another
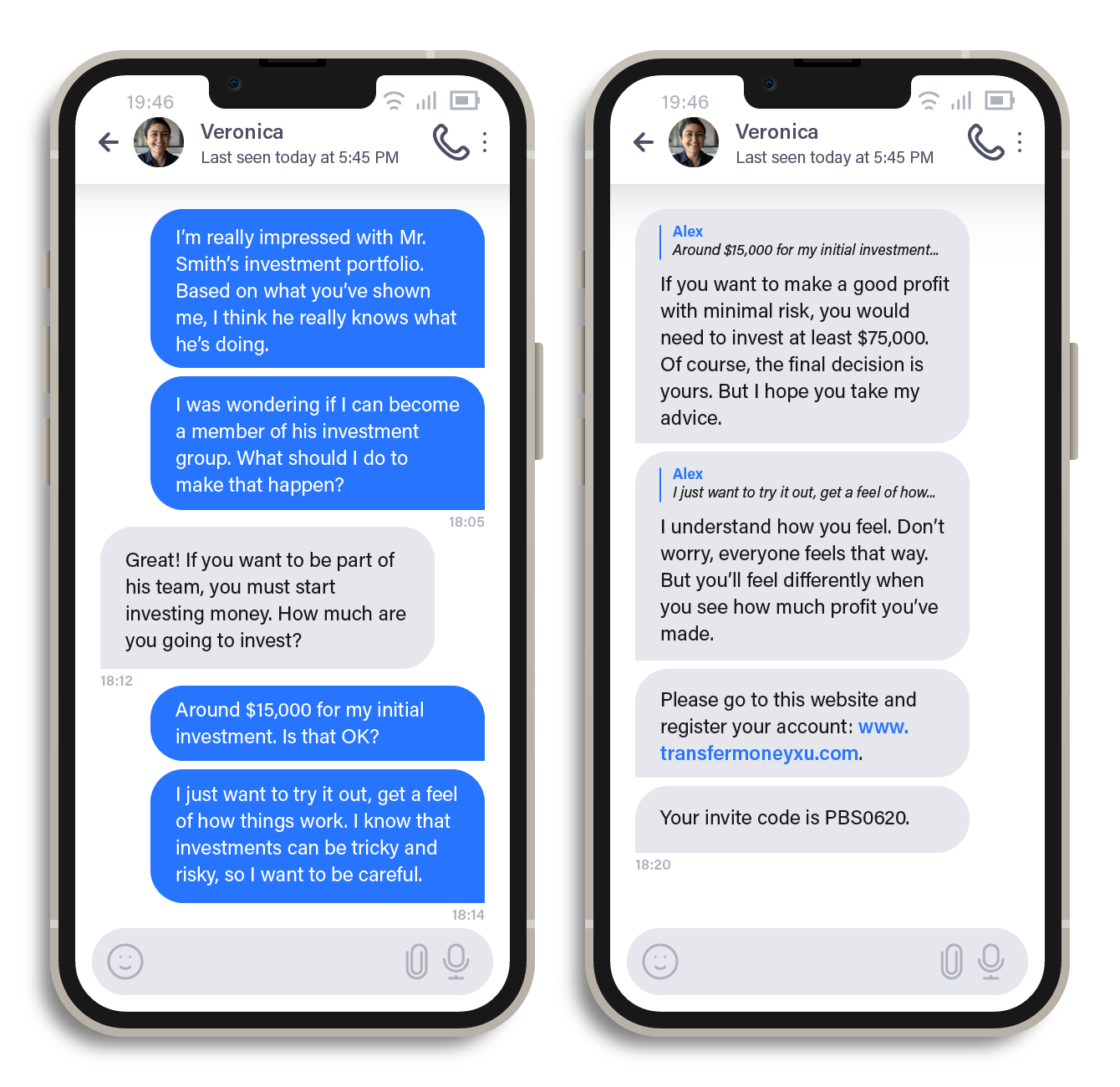
As the conversation progresses, the scammer gradually introduces the victim to the fake investment scheme and promises significant profits within a short period if the victim invests a certain amount. Unfortunately, many victims fall for this fraudulent scheme due to the scammers’ persuasive tactics and convincing appearance of legitimacy.
Figure 2. A scammer advising a victim to invest a large sum of money
HOW THE PIG-BUTCHERING SCAM WORKS
Pig-butchering scams, like many other types of investment fraud, follow a series of steps that are designed to manipulate and deceive victims. The scammers prey on the victims' desire for financial success and exploit their trust to carry out their nefarious schemes. The following sequence of phases outlines the common progression of how scammers carry out a pig-butchering scheme:
- Gaining a victim’s trust. The scammers initially develop the trust of their victims by presenting themselves as knowledgeable professionals or seasoned investors. They also use social media platforms or online forums to engage with potential victims and create an illusion of credibility and success. They also employ another unique tactic: adding a layer of romance or companionship to their scam. This means that they exploit not only their victims’ desire for financial success but also their innate need for connection and intimacy.
- Pitching the investment. Once trust is established, the scammers introduce a promising investment opportunity. This could involve stocks, cryptocurrencies, or other financial instruments. The scammers typically use persuasive language, manipulate numbers, and employ a sense of urgency to convince victims that the opportunity is too good to pass up.
- Collecting money. After persuading the victim to invest, the scammers collect the funds, often using digital payment platforms or cryptocurrencies to make tracking more difficult.
- Disappearing completely. Once they have received a substantial sum from their victims, or once the victims try to withdraw funds from the account, the scammers will suddenly become unreachable, or the brokerage platform will have trouble transferring funds. Scammers could also delete their online presence or create new identities, making it difficult for victims to recover their lost funds.
Each step is designed to draw victims further into the scammers’ web of lies. As the victims become more invested both emotionally and financially, it becomes increasingly difficult for them to recognize the scam for what it is and remove themselves from the situation.
EMERGING TACTICS: GROUP CHATS AND SOCIAL ENGINEERING
As pig-butchering scammers continue to adapt and refine their strategies, the emergence of new tactics — ones that enable them to more effectively target and manipulate their victims — also becomes more apparent. Previously, scammers focused on engaging individuals through one-on-one chat messaging. However, recent trends indicate a shift toward the use of group chats, allowing scammers to cast a wider net and identify potential victims with greater efficiency.
The scammers’ workflow typically begins with adding potential victims to a fake investment chat group that they moderate. If a victim shows interest in investing, the conversation evolves into a one-on-one chat. From there, the victim is introduced to a fake brokerage service and prompted to transfer funds to its website. As scammers continuously search for more victims, maximize their profits, and expand their reach, this workflow is repeated.
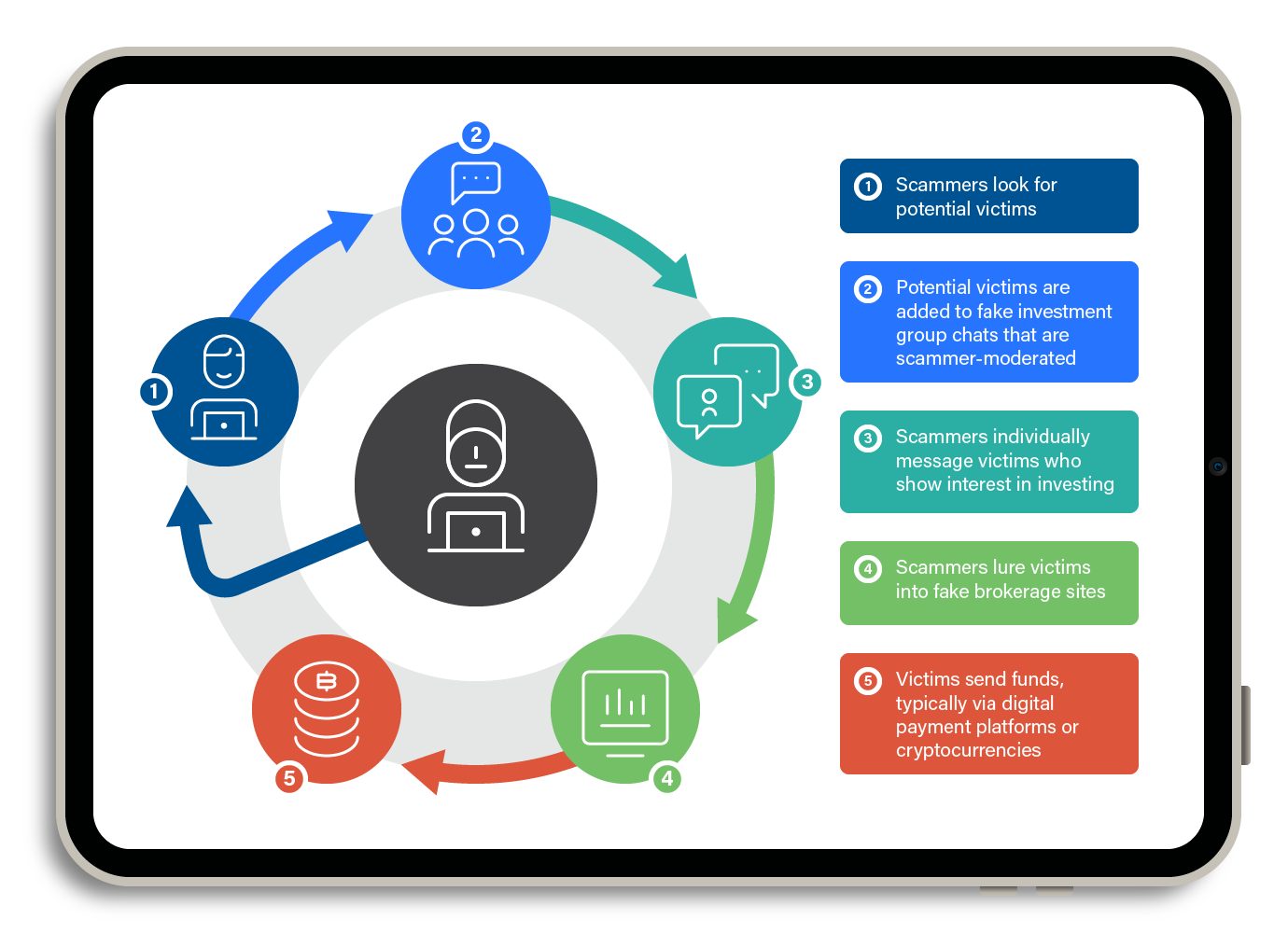
Figure 4. The workflow of a pig-butchering scammer
During our investigation, one question that came up was how scammers are able to obtain their potential victims’ phone numbers. Our research suggests that a significant portion of these phone numbers can be traced back to leaked databases containing personal information. We observed that more than half of the numbers added to the fake group chats have been found in such databases, indicating that scammers could be using leaked information to find their next victims.
Another possibility is that scammers acquire lists of phone numbers through underground markets, where cybercriminals trade and sell personal information. Based on our tests, we noticed that long-standing phone numbers tend to be targeted, while burner numbers or newly obtained phone numbers rarely receive these spam messages. The fact that scammers focus on established phone numbers implies that they have access to a source of personal information either through leaked databases or from underground markets.
The group chat strategy
By adding multiple people to chat groups that are centered around investment discussions, scammers can quickly gauge the interest of their targets. Those who remain in the group are more likely to be interested in investing, making them prime candidates for the scam. On the other hand, individuals who leave the group are either aware of the scam or are uninterested in investing. Hence, they are less likely to be persuaded by the scammer’s tactics.
The scammers consist of a group of individuals with different roles and objectives. Some of the chat group members are fake profiles created by the scammers themselves to make the group seem more authentic. This approach makes the process for scammers easier, enabling them to focus their effort on individuals who are more susceptible to their fraudulent schemes. It also creates an environment that promotes a sense of community and social validation, as potential victims would see that other people are engaging in discussions about investment and are not calling out the scam.
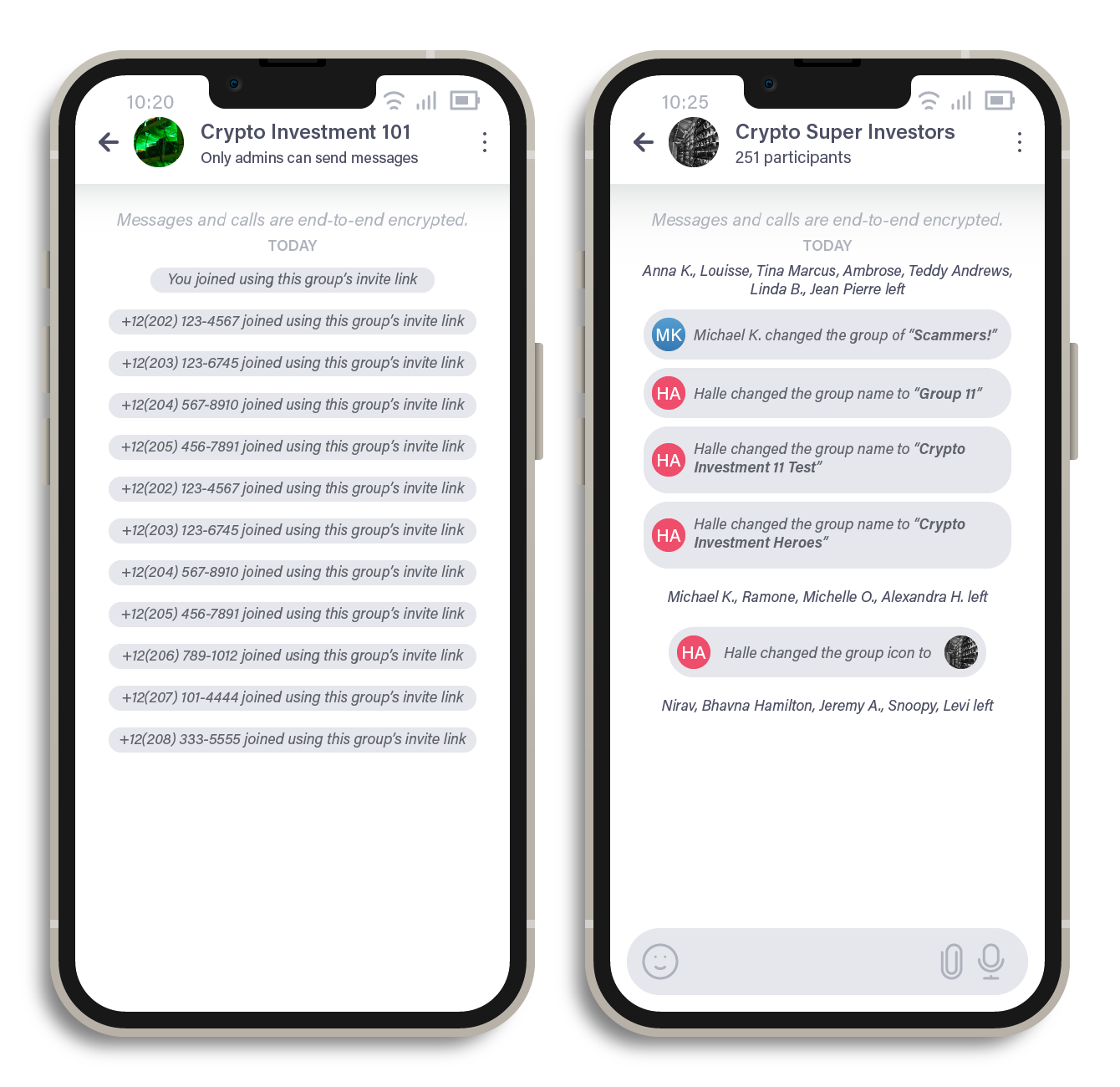
Figure 5. (Left) Unsuspecting victims who joined a fake investment group through an invitation link and (right) users who were added to a fake investment group chat and were possibly aware of the scam and left
Creating authenticity through group chat interactions
To further enhance their credibility, scammers often share images of their daily activities within the group chat. They also share images that subtly highlight their alleged earnings with other group chat members, which suggests that their success is a direct result of their investments. This creates an illusion that the members of the group are real people who are well-versed in investments, making it more difficult for potential victims to question the legitimacy of the investment opportunity. This tactic preys on the psychological phenomenon known as social proof, where individuals are more likely to trust and follow the actions of others, particularly when they appear to be successful.
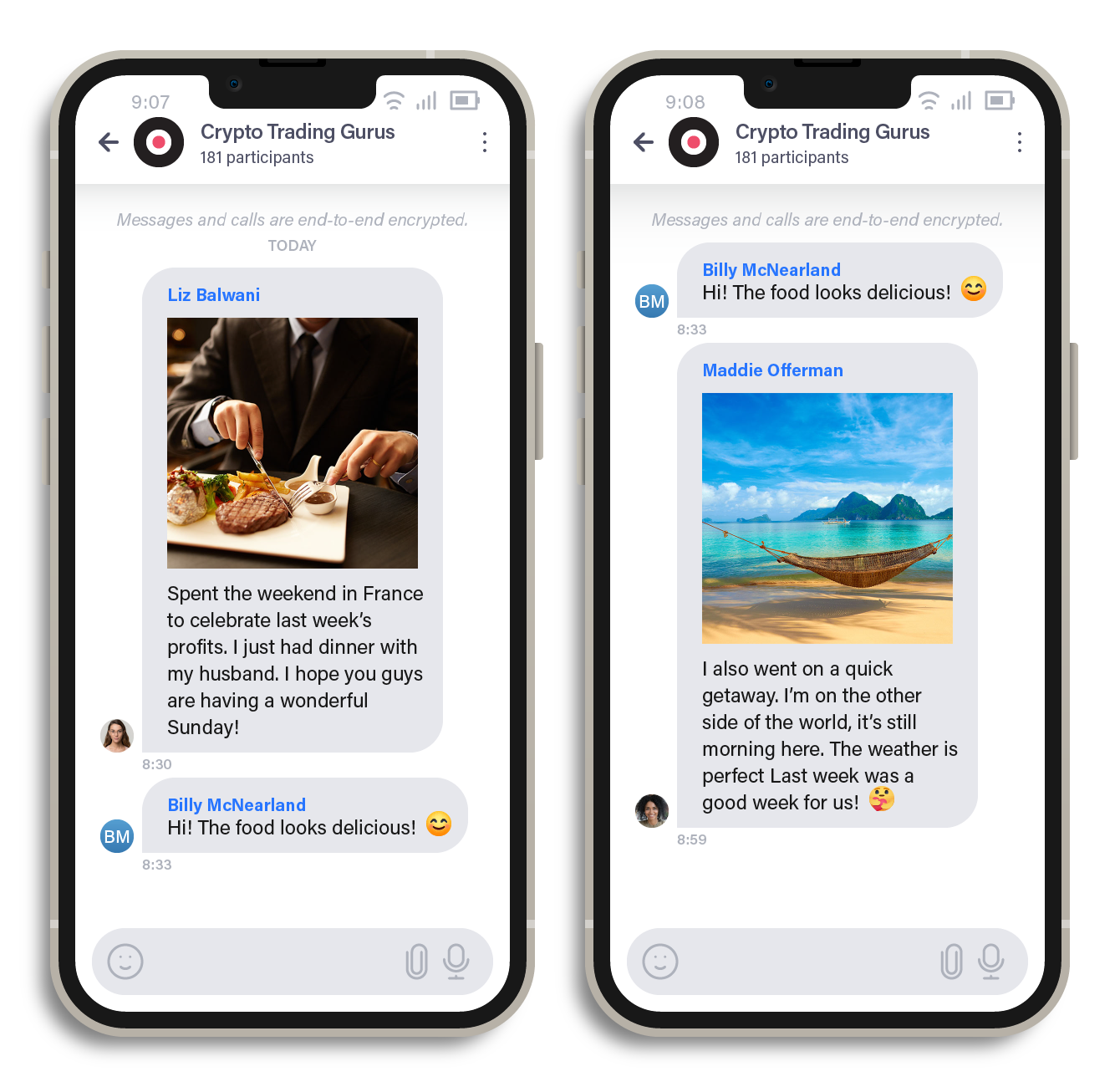
Figure 6. Chat interactions in the fake investment chat group
Transitioning to one-on-one chats: The deceptive secretary
Once the scammers have identified their targets from group members who have remained in their fake investment chat groups, they initiate a more personalized approach by transitioning to one-on-one chats. In these private conversations, the scammer poses as a secretary of the individual who provides trading signals and often uses a fake profile accompanied by a picture of an attractive woman. These one-on-one interactions can become personal and can set the stage for the pig-butchering scheme that will unfold.
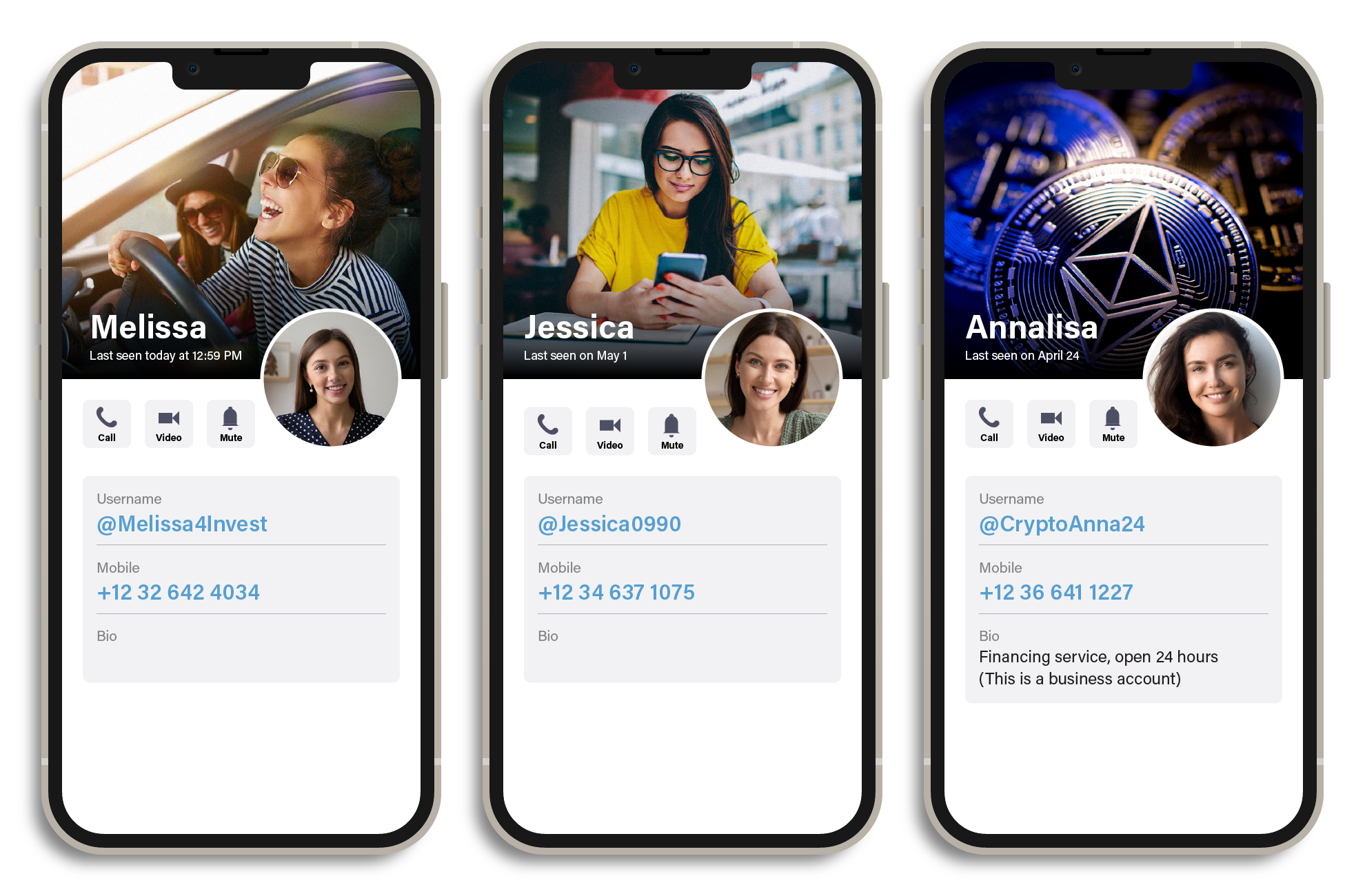
Figure 7. The fake secretary profiles of pig-butchering scammers
The scammers posing as secretaries walk the victims through the registration process on the fake brokerage sites. These fake secretaries also instruct victims to open accounts with legitimate cryptocurrency brokers to purchase cryptocurrencies. To fund their fake brokerage accounts, the scammers would then ask the victims to transfer their cryptocurrencies — ones that they obtained from the legitimate cryptocurrency brokers — to the crypto wallets controlled by the scammers. On the fake brokerage website, victims are presented with fabricated positive returns, enticing them to invest more.
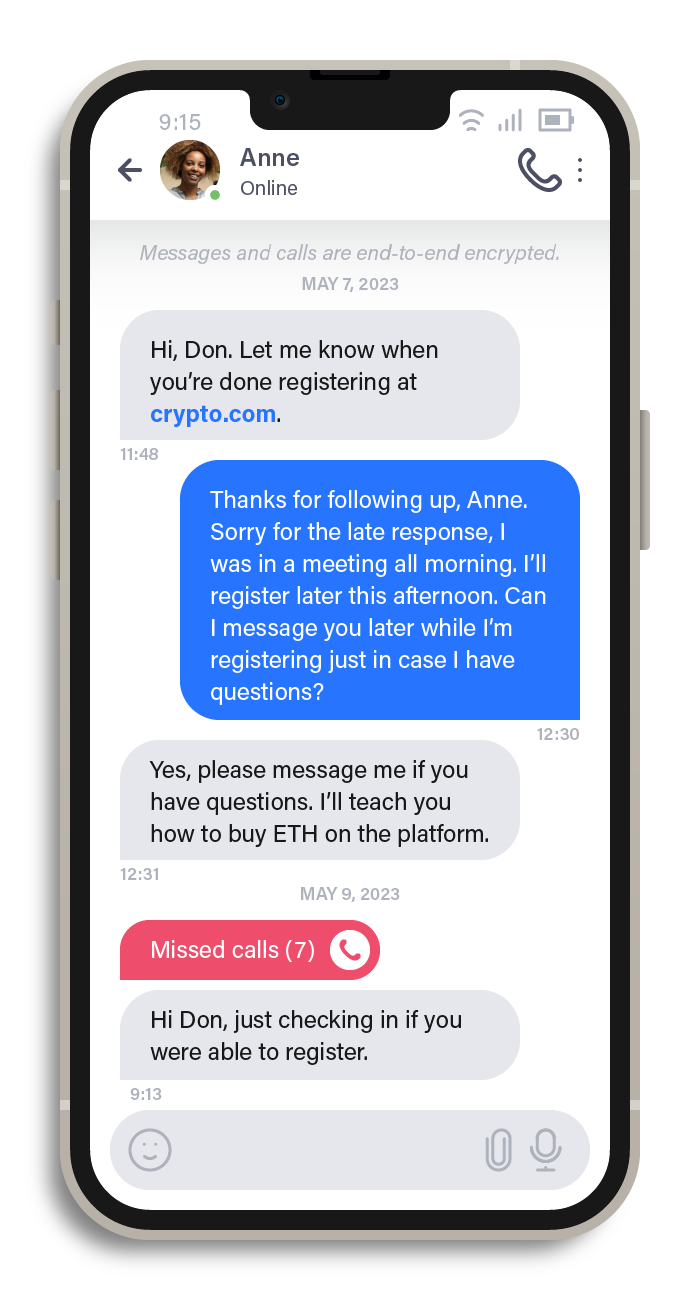
Figure 8. A conversation with a fake secretary guiding a victim on how to purchase cryptocurrencies
The so-called secretary is persistent in reminding the victim that new trading signals will be released soon, urging them to pour even more money into the fraudulent brokerage. This process of enticing the victim to invest more is incessant — the secretary provides constant reassurance of the investment's success and creates an illusion of trust between the scammer and the victim.
However, when the victim eventually attempts to withdraw their funds, they suddenly encounter difficulties getting in touch with the secretary. Excuses are given, stating that the account requires additional verification before funds can be withdrawn. This could lead the victim to send additional documents that reveal personally identifiable information (PII) in an attempt to verify their account, further exposing them to the risk of identity theft.
As the victim becomes more entangled in the scam, the fraudsters leverage the trust that they have built to continue extracting money and personal information. It is only when the victim can no longer provide additional funds or more pieces of PII that the scammers vanish, leaving the victim with significant financial losses and a heightened risk of identity theft.
Launching fake brokerage sites and apps
To further add legitimacy to their schemes, pig-butchering scammers also create fake brokerage websites and/or mobile applications for users to log in to. These fraudulent platforms are designed to mimic the appearance and functionality of genuine brokerage platforms, making it difficult for potential victims to determine authenticity via appearance alone.
Our research has determined that the domain addresses for these fake brokerage websites are often recently created, indicating that scammers are continually making new brokerage platforms to deceive their victims. Despite their brief online existence, these sites are carefully crafted to seem professional and trustworthy, appearing to look like legitimate cryptocurrency apps to lure unsuspecting individuals into believing that they are investing through a legitimate brokerage.
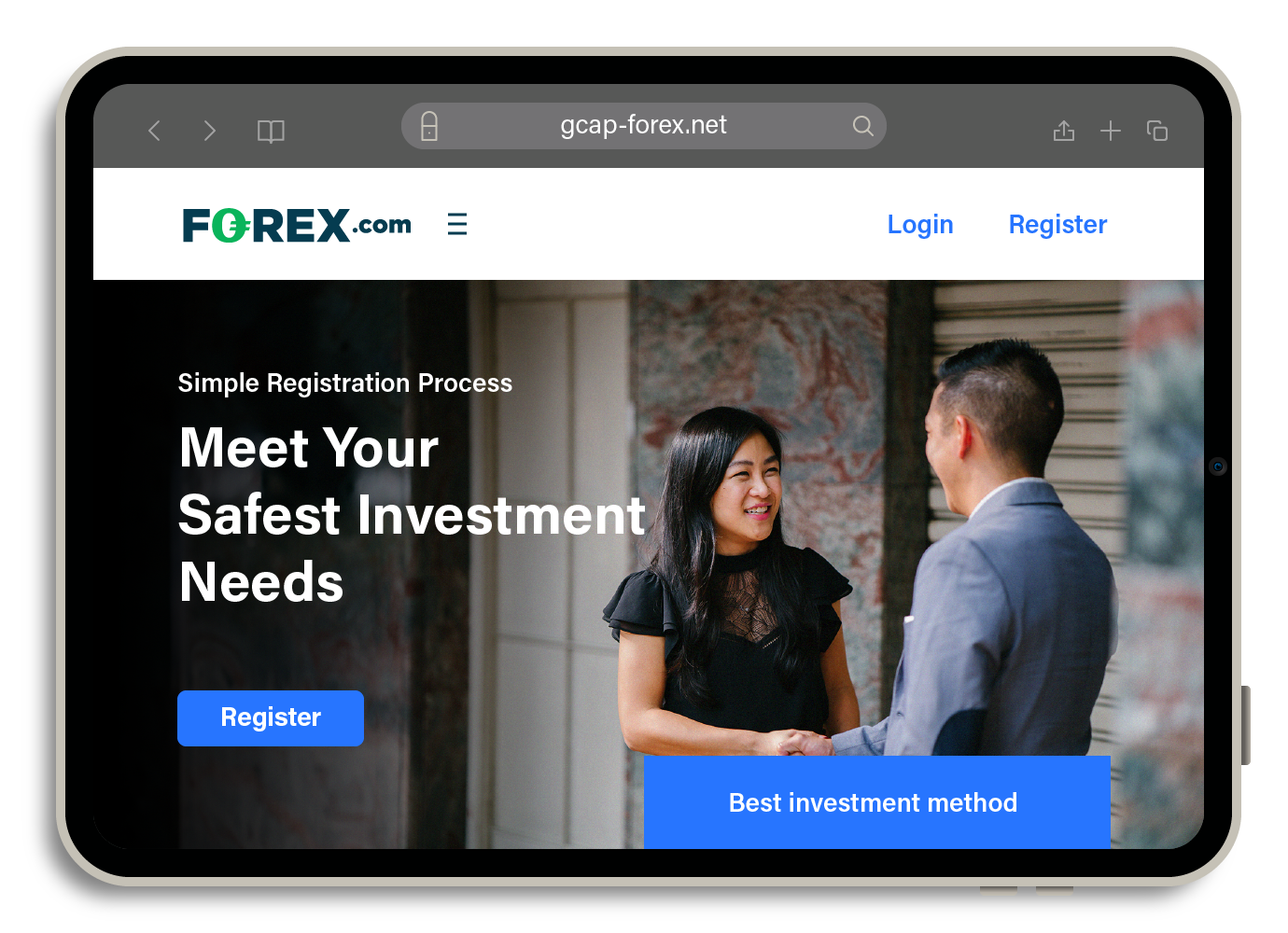
Figure 9. Example of fake brokerage websites using a legitimate broker’s logo
As previously mentioned, some fake brokerages have taken their deception a step further by developing Android applications that are available on the Google Play Store. This additional touch of credibility can be highly persuasive for potential victims who might be more inclined to trust a platform that has been vetted and approved by a reputable app store.
Another alarming aspect of these fake brokerages is their implementation of Know-Your-Customer (KYC) checks during the registration process. While this could seem to be a standard security measure, it poses a significant risk for victims who provide their personal information. Not only do they stand to lose their money in the scam, but they also risk becoming victims of identity theft, as scammers could exploit their sensitive data or sell it off to other cybercriminals.
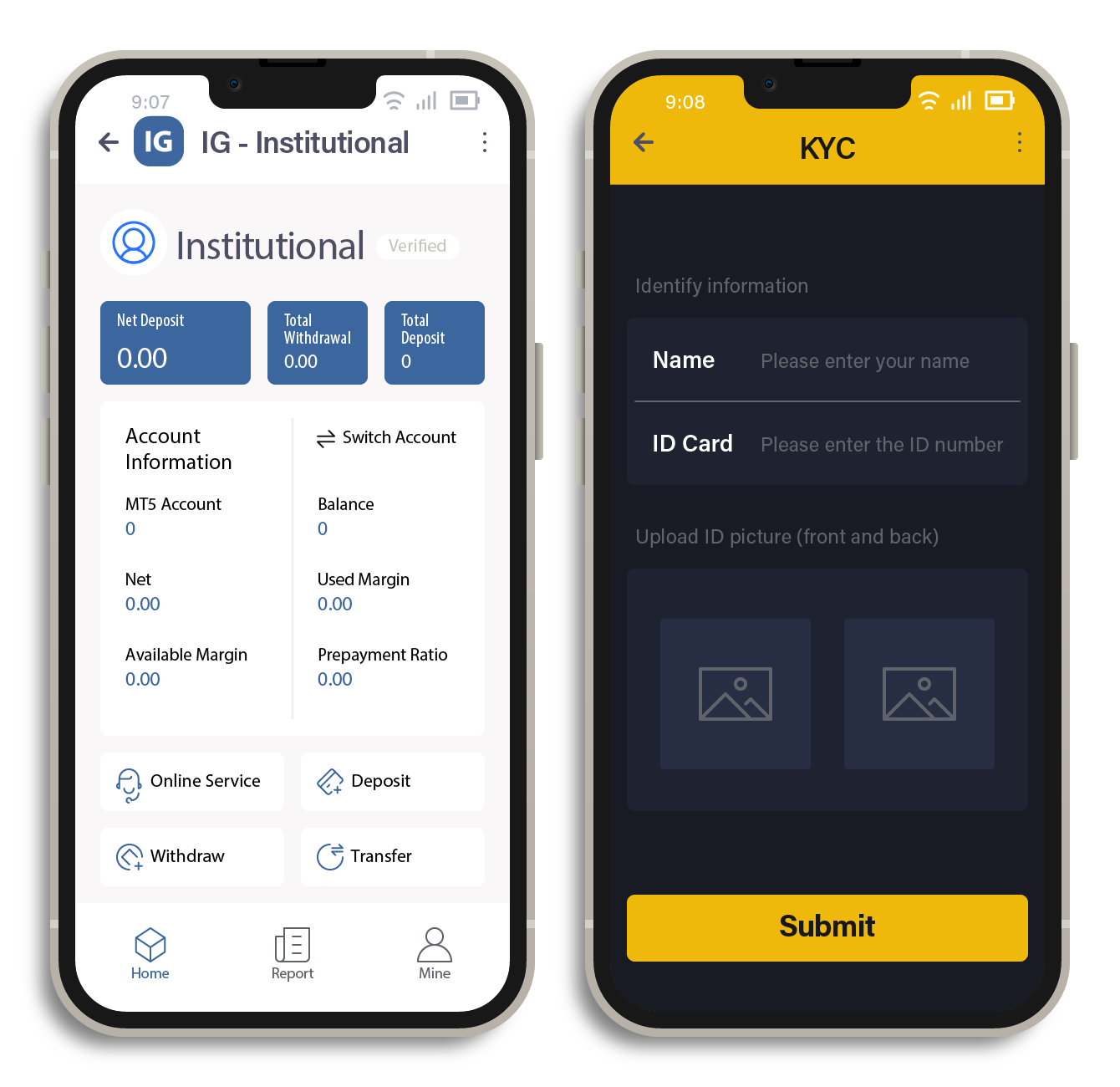
Figure 10. (Left) A fake brokerage mobile application that’s available on Google Play and (right) the KYC verification feature of a fake brokerage site that requires users to upload identification cards
The impact of pig-butchering scams
The FBI's recent reports on pig-butchering scams have revealed the devastating financial impact on victims. Thousands of individuals have fallen prey to these scams, resulting in millions of US dollars in losses. However, it is possible that the true extent of the problem is even more significant, as many victims are too embarrassed to report their experiences or are unaware that they have been scammed.
By closely monitoring the chat groups and identifying the fake brokerage sites, we were able to track down some of the cryptocurrency wallets controlled by these scammers. Based on one group of scammers alone, we estimate that this group has netted almost US$4 million based on transactions made from January to March 2023, indicating the severity of this scam. Table 1, which shows the total amount of funds transferred to each brokerage site and their corresponding cryptocurrency wallets, gives a clearer picture of the magnitude of this operation.
| Scam Broker | Token | Crypto Wallet | Token Value | Estimated US$ |
|---|---|---|---|---|
| okbipro[.]com | BTC | 3Cz32AGkdhJuDhUfstFZT32jouCpG2A7dn | 4.73202024 BTC | 107,469.59 |
| ETH | 0x68b1f66B0Ef9b0B2B7d45901616B222dca690bd4 | 42.926882 ETH | 63,072.13 | |
| RC20 | 0x68b1f66B0Ef9b0B2B7d45901616B222dca690bd4 | 593,772.44 USDT | 593,772.44 | |
| RC20 | TT4kk5DAwQ8XS6XVvzkWu2XDBtoJP2s9ok | |||
| cronosca[.]com | BTC | 3GSHjL87oowrzpcPWb33MSQorkgqPfKYxg | 1.8743 BTC | 31,840.16 |
| ETH | 0x5e0e496ac2b85162dD2e300D08c409BDE06ea9DE | 99.597488 ETH | 162,431.72 | |
| RC20 | 0x5e0e496ac2b85162dD2e300D08c409BDE06ea9DE | 861,372.99 USDT | 861,372.99 | |
| RC20 | 3GSHjL87oowrzpcPWb33MSQorkgqPfKYxg | |||
| trading-ic[.]com | BTC | 3Fr5kRfei6DqLsrPc4mnemq2Z7hBqMsbpg | 0.69306778 BTC | 17,345.34 |
| ETH | 0x1212C6a348b20CfCdcb8C7363a3bdb9E4aC50b39 | 14.432534 ETH | 23,518.22 | |
| RC20 | 0x1212C6a348b20CfCdcb8C7363a3bdb9E4aC50b39 | 322,681.80 USDT | 322,681.80 | |
| RC20 | TP7eP1Xygmb7iUBrQfcahNnHCWii8uixEX | |||
| amtopwd[.]com | BTC | 38NXsqmCN8znjFw1btezGcXVKbDWsVKYck | 0.55230811 BTC | 12,691.92 |
| ETH | 0x02FDB0Ce8D95394a51c52F4beEc804AAcd458F29 | 76.525566 ETH | 120,996.57 | |
| RC20 | 0x02FDB0Ce8D95394a51c52F4beEc804AAcd458F29 | 77,362.70 USDT | 77,362.70 | |
| RC20 | TNxE6Da5J7NaPiJe8QAMZt4pEaCR9xAra2 | |||
| vatusdt[.]com | BTC | bc1qsz23utgv436q6063sta65wvnqudu4xj3qq8d78 | 0 BTC | 0 |
| ETH | 0x93a737871f70FF2D8946Ebc6d4905f1c1B8250eD | 0.01 ETH | 16.66 | |
| RC20 | 0x93a737871f70FF2D8946Ebc6d4905f1c1B8250eD | 20,628.86 USDT | 20,628.86 | |
| RC20 | TT2K7V3SxnrTtWySDDC8tEhuyXrgc4ArHx | |||
| gcap-forex[.]net crmforexs[.]com | BTC | 3Bmu5Lt7NNR6h7mAQHrMJN4X9t7wsYn92b | 9.89690779 BTC | 179,839.95 |
| ETH | 0x573d623B9cd3fF486D1Bd146e36B39A805499497 | 0.144589 ETH | 220.22 | |
| RC20 | 0x573d623B9cd3fF486D1Bd146e36B39A805499497 | 706,495.03 USDT | 706,495.03 | |
| RC20 | TCX7Edsh2Bj1UGA6MWPbL5RFm7we7Ca3m2 | 89,289.52707 TRX | 5,878.28 | |
| filecoinprotocol[.]com | BTC | 3BzSRRrdQabzsipN4QewSYo4X3gTGjBQfH | 1.0866382 BTC | 27,574.10 |
| ETH | 0x68E760947Db2deeA251843F0096084Fa5C784D9E | 11.498334 ETH | 19,127.16 | |
| RC20 | 0x68E760947Db2deeA251843F0096084Fa5C784D9E | 671,675.16 USDT | 671,675.16 | |
| RC20 | TT2wjB7V6YnGQTiYtkz8S35bhMkhc3xTnc | |||
| RC20 | 0x68E760947Db2deeA251843F0096084Fa5C784D9E | |||
| C20 | 0x68E760947Db2deeA251843F0096084Fa5C784D9E |
Table 1. A summary of the total transactions transferred to the cryptocurrency wallets owned by a group of scammers
Victim demographics
One striking aspect of pig-butchering scams is the victims’ demographic profile. The large transaction amounts deposited into the scammers' accounts, ranging from US$10,000 to US$100,000, suggest that the targets are not victims with limited savings. Instead, these scams appear to be targeting a more financially established demographic, including professionals with high salaries and individuals nearing retirement. Figure 13 shows that some of the transactions made to a scammer's cryptocurrency wallet were in the five- to six-figure range.
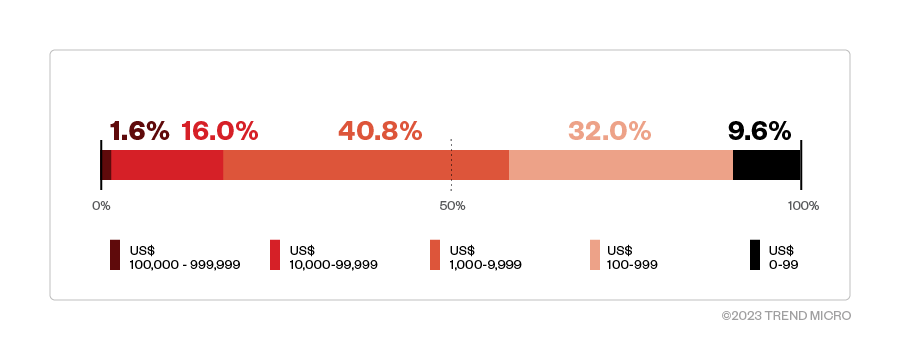
Figure 11. Breakdown of transactions made to a cryptocurrency wallet controlled by pig-butchering scammers, 40% of which are in the US$1,000 to US$9,999 range
It is plausible that scammers are focusing their efforts on victims they consider “big fish,” as these individuals are more likely to have access to large sums of money. These individuals are also potentially more susceptible to the scam because it’s possible that they would like to grow their wealth and maintain their lifestyle. In some cases, these individuals might overlook red flags in their eagerness to capitalize on seemingly lucrative opportunities. According to the 2022 IC3 report, the victims of these scams typically fall under the 30 to 49 age range. This further highlights the scammers' focus on individuals with greater financial resources.
Another possible target group for pig-butchering scams are individuals approaching retirement who might have substantial savings and are actively seeking investment opportunities to secure their financial future. It’s possible that scammers will exploit this sense of urgency and vulnerability to convince victims to invest in their fraudulent schemes.
According to the same IC3 report, victim losses pertaining to investment fraud have reached a whopping US$3.31 billion, which is considerably higher than other types of fraud. Included in this staggering amount are complaints pertaining to cryptocurrency investment fraud, which reached US$2.57 billion last year. These alarming numbers further emphasize the importance of raising awareness and taking proactive measures against these malicious actors to protect individuals' hard-earned savings and financial futures.
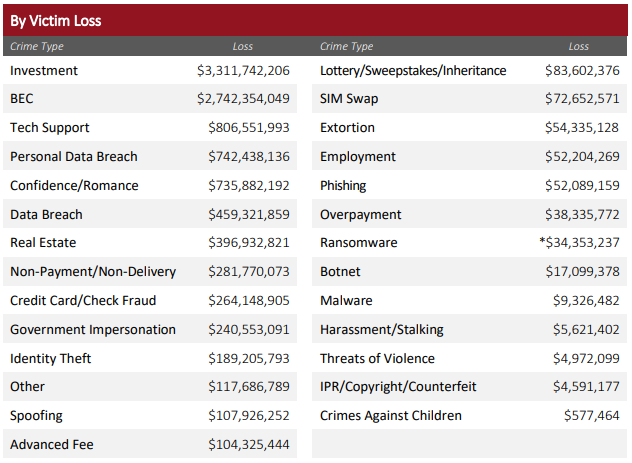
Figure 12. Top reported fraud by victim losses in 2022
Source: 2022 Federal Bureau of Investigation Internet Crime Report
Saving victims from falling prey to pig-butchering scams
Given the alarming trends and the growing sophistication of pig-butchering scams, it is crucial for individuals to take proactive steps in safeguarding their investments and personal information. The following recommendations, some of which are provided by the FBI, are designed to help individuals recognize the warning signs of these scams and take appropriate action:
- Be cautious of unsolicited messages and group chats. As previously discussed, scammers often initiate contact through seemingly innocent chat messages or by adding individuals to investment-themed group chats. Be wary of engaging with strangers and carefully consider the source of any unsolicited messages or group chat invitations.
- Verify the legitimacy of brokerages. Before investing your money, make sure that you conduct a thorough investigation of the brokerage you’re considering. Check for recently created domains via registration data or news articles. If something seems suspicious, trust your instincts and avoid engaging with the platform.
- Monitor identity theft resources for leaked personal information. Be vigilant about the security of your personal information. Regularly check or sign up for reputable identity theft monitoring services to track any leaks or breaches involving your data and take appropriate steps to secure your information if needed.
- Be skeptical of high investment returns with low risks. If an investment opportunity promises high returns with minimal risk, it is likely too good to be true. Always research and verify investment opportunities before committing your money.
- Educate yourself about emerging tactics. Stay informed about the latest strategies employed by scammers, such as the use of group chats and fake brokerages. By understanding how these scams work, you can better recognize the warning signs and avoid becoming a victim.
- Report suspicious activity. If you encounter a potential pig-butchering scam, report the incident to law enforcement. Your report could help prevent others from falling victim to the same scam. If you have already transferred funds to fake brokerage websites, it is best to report this as soon as possible to potentially recover them.
CONCLUSION
The alarming rise of pig-butchering scams and their devastating impact on victims emphasizes the imperative to stay informed about and vigilant of the tactics and strategies employed by scammers. As malicious actors continue to adapt and refine their methods, it is essential for individuals to remain proactive in protecting themselves and their investments, especially since those who are new to investing large sums are more susceptible to falling victim to such schemes. If you find yourself in a seemingly trustworthy relationship with an unknown person online that follows this scam’s patterns, it is crucial to take a step back and evaluate if you might be the target of such a scheme.
Moving forward, it is critical to be aware of the risks posed by pig-butchering scams and other types of investment fraud. Scammers involved in investment frauds are likely to evolve their tactics and methods when approaching victims, but their core intent would remain the same — to swindle individuals out of their hard-earned money.
In the face of these evolving threats, always exercise skepticism toward obscure private investment opportunities and prioritize well-established and mainstream ventures. By doing so, individuals minimize the risk of falling for scams and increase their chances of earning a profit instead of losing everything.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks