Going into the holiday shopping season, many people will opt to do their shopping online. The online shopping experience has evolved during the past two years of Covid-19, a time that drove awareness for new and convenient ways of shopping people may not have otherwise explored. At the same time, a variety of events highlighted supply chain and delivery issues. Many will remember the spontaneous panic-buying of toilet paper and the widespread adoption of online purchases including home delivery of groceries. Worldwide, many will also remember the global shipping delays caused by the Evergiven container ship becoming jammed in the Suez Canal.
At the time of writing, the effects of the pandemic in several countries seem to be slowing down. In fact, the rise in consumption is now driving increased consumer purchasing. This bubble of demand was not predicted by traditional supply chain logistics algorithms. The demand for shipping containers at a macro level has exceeded the global supply while highlighting the fact that many truck drivers found other employment at a time when there was reduced demand.
These issues can be remedied with technology. For example, predicting demand is a core attribute of artificial intelligence (AI) and machine learning (ML), while delivery plays to the core attribute of autonomous vehicles. Trigger events, such as those that prompt restocking, are a core attribute of internet of things (IoT) devices such as smart shelves and smart carts. Meanwhile, enabling technologies like 5G reduce reliance on co-located human involvement for all tasks, from drivers to cashiers, allowing people in other countries to perform low-end tasks that are increasingly difficult to hire for.
In 2030, the online shopping experience would be composed of many technologies working together to increase global social resilience and “flatten the curve” of supply chain risks. In this report, we describe the 2030 era as being the next generation of retail. While many of the technologies we have mentioned exist today as small deployments or as successful proof of concepts, our vision of retail in 2030 is one of unified enablers; predictive inventory, supply chain logisitics, and management of goods; and resiliency-enhancing changes to delivery models. One example of these changes to delivery models include dynamic warehousing in which goods move closer and closer to the consumer as the time of expected order delivery occurs. This has the effect of making supply chains shorter and delivery logistics more capable of reacting to bubbles of demand.
These enablers are categorized as delivery models, smart shelves, roboticization, artificial intelligence and machine learning, cashless payments, supply chain, and in-store experience.
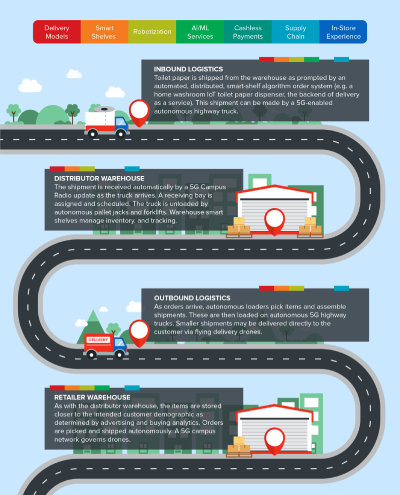
We use the delivery of toilet paper as a use case scenario, illustrating the role of each enabler and how they would work together as seen in Figure 1.
The seven technology pillars of next generation retail
The journey of the roll of toilet paper into consumers’ homes gives an overview of these seven-technology pillars or enablers’ roles in the future of retail. This section explores the technologies in each of these pillars. What will these pillars look like in 10 years and what does it mean for cybersecurity?
Robotization
Robots will be extensively used for tasks like deliveries, returns, in-store assistance, and in-store fresh meal preparations. They will support, and in some ways, even replace store employees.
SECURITY AND PRIVACY IMPLICATIONS
- Hacking or theft of autonomous delivery vehicles. Attackers could hack or intercept autonomous delivery vehicles and steal shipments.
- Hackers gaining control of a fleet. Hijacked vehicles, drones, or trucks can be used for criminal activities such as a mule network to transport stolen goods or as a mobile goods stash.
- Using radio frequency (RF) interference to hijack delivery units. RF interference can be used to hijack autonomous delivery units or conduct a distributed denial of service (DDoS) attack against a delivery service provider.
- Targeting robots for surveillance attacks. Robots are very interesting targets for surveillance attacks as they have multiple cameras and sensors for spatial recognition that can be misused.
- Terrorist attacks using autonomous vehicles. Autonomous vehicles can be controlled to commit terrorist attacks.
- Critical outages. This can be brought on by the excessive dependence on robotization, similar to the recent Facebook/WhatsApp outage case that caused businesses that operate via the social media platforms to lose hours of revenue generation.
- Using exploits on trusted technologies. Robots permitted to enter certain buildings can be used as trojan horses to conduct one or several stages of hi-tech attacks. They can, for example, bring a rogue base station or Wi-Fi access point into the building and allow an attacker to intercept two-factor authentication (2FA) or wiretap network traffic. They can also be used to perform war shipping, a form of espionage in which a hacking device is sent to a fictitious person at a location. The hacking device uses radio from inside the delivery drone to make an attack on local WiFi or campus cellular network; because the person is fictitious the drone will return the device to the hacker.
Supply chain
The supply chain (SC) will evolve to become both automated and Just In Time (JIT) with real-time order tracking for customers. Stores will also roll out in-store vertical farms for fresh produce, to improve profits, and have customer customizable production.
Just In Time (JIT) and customizable supply chain. The Just In Time supply chain will lend itself to a customer customizable production chain. If implemented correctly, together with predictive analysis, this is expected to cut down costs for smaller retailers. Large retailers benefit from economies of scale, but a deeply profiled customer base together with predictive analysis should reduce stock wastage and improve efficiency for all retailers.
Farm-to-table supply chain. A farm-to-table supply chain eliminates the middleman involved and supports local producers and farmers. Retailers have greater control over the SC, while consumers can view the farm-to-table delivery chain and consult a freshness tracker. This can also be used to assert supply chain security for food, as well as to track and detect counterfeit food, including stolen food sold in collusion with local retailer staff.

In-Store
Vertical Farms
In-store vertical farms. In-store vertical farms will provide customers with the freshest possible produce grown in-store. These can be picked and taken home or used for in-store food preparations like salads, sandwiches, stir-fry dishes, etc.

Online Bidding Mechanism for Specialty Items
Online selling and bidding of specialty items. Customers will be allowed to participate in curated retailer auctions for specialty or premium items (e.g. truffles) that stores don’t typically stock. This will make these items available and maintain a healthy profit margin. More importantly, it provides a one-stop shop for consumers by eliminating the need to visit specialty stores.
SECURITY AND PRIVACY IMPLICATIONS
- Interception of pickups and deliveries. Delivery or pickup spots could be intercepted to steal shipments.
- Hacking or theft of autonomous delivery vehicles. Attackers could hack or intercept autonomous delivery vehicles and steal shipments.
- Hijacking gaining control of a fleet of drones or trucks. This can lead to many different types of crimes such as next-generation ransom attacks.
- The addition of minute defects in 3D printed designs. For stores selling 3D printed designs, adding minute malicious defects or imperfections can result in a wide range of consequences.
- Attacks that affect the delivery of high-demand products. Attacks can affect the reliability, quality, or timing of the delivery of high-demand products.
- Extremely granular hijacking. Examples of this include interception of a specific delivery vehicle transporting specific street-resellable prescription drugs to specific homes.
Delivery Models
Delivery models will evolve in a way that leads to the rapid growth in home delivery e-commerce that already started because of the global pandemic. New click-and-collect models, shopping-as-a-service, in-home deliveries, drone deliveries, and other models will expand to become the norm.
Click-and-collect. Click-and -collect will allow the customers to pick up purchases from the store or for stores to deliver purchases using drones to the customer's vehicle in the store parking lot.
Automated store models. The Amazon Go store model or similar models will be offered as a service with retailers and manufacturers directly stocking products in these types of stores.
In-store automated storage and retrieval systems. In-store automated storage and retrieval systems (smart shelves) will coordinate customer orders with delivery drones to provide a more efficient and faster delivery experience for the customers.
Delivery drones used for returns. Delivery drones will also be used for package returns from the customer, thereby simplifying the entire return process and cutting the cost for the retailers who won’t need to pay for return deliveries.
Growth of shopping-as-a-service. Shopping-as-a-service will continue to grow. Dedicated apps like Instacart and Yandex.Eda already provide this service. Food delivery services like UberEats are also branching into this service.
Home security products interfacing with delivery drones. Home security products, like the Ring doorbell, will be able to interface with trusted drone delivery companies. They will open the front door and allow drones to deliver goods inside the home, reducing the possibility of theft by porch pirates.
Localized mothership concept. Delivery trucks drive up to neighborhoods then multiple drones unload packages from the trucks and deliver to homes in the neighborhood.
An extensive catalogue of 3D printed designs and materials. At home or in-store 3D printers can print purchased designs from an extensive catalog. In-store 3D printers can print models using a wider range of materials including metal. They can also print faster than home printers and have access to an exclusive catalog of products such as car engine replacement parts.
SECURITY AND PRIVACY IMPLICATIONS
- Intercepting delivery and pickup spots. Attackers can intercept delivery and pickup spots to steal shipments.
- Hacking or intercepting autonomous delivery vehicles. This will be done to steal shipments.
- Delivery systems as a prime target. Target delivery systems as it tracks a lot of personal data.
- New scams. New attack schemes could involve phishing pages for smaller grocery stores and chains.
- The abuse of anything-as-a-service infrastructure. Anything as a Service is abused to sell black market or contraband items and services.
- The Amazon Go model being compromised. Attackers can walk away from a store with goods paid by someone else’s credit card.
- Web bots being used to order high demand items and reselling them elsewhere. This is already happening with gaming consoles, but could potentially happen to toilet paper, hand sanitizers, and other grocery items.
- Attacks against the business model and processes. Since all shipments have a cost, large orders of low-cost goods will temporarily consume all the capacity of delivery drones. This can have a negative impact on profits. Such an attack could be strategically carried out by a malicious competitor.
In-Store Experience
In-store experience is an important component of next-generation retail stores as many customers still prefer to shop in physical stores.
1
Smart shopping carts. Smart shopping carts will be able to perform automatic checkouts of items placed inside it when the customer exits the store.
2
More smart shelves. Smart shelves are becoming popular in retail stores. They are capable of inventory tracking and reordering, displaying customized ads and dynamic pricing, mood tracking, track purchasing pattern, etc.
3
Mobile smart shelves. Smart shelves are expected to evolve into mobile shelves. Mobile shelves in self-organizing stores use Kohonen networks, historic seasonal data, and demand to reorganize themselves. Mobile shelves will also be able to use the in-store ASRS for restocking when shelf stocks are depleted.
4
Food preparation done by robots. In-store robots will prepare fresh meals in front of the customers.
5
Smart shelves tracking customers. Smart shelves that are capable of tracking moods and purchase patterns can display targeted ads or temporary sales to entice the customer to make a complementary or impulsive purchase.
6
Robotic assistance. In-store robotic assistance will provide personalized shopping experience by helping collect the items from a customer's grocery list.
7
Mobile grocery trucks. Fully stocked mobile grocery trucks drive to neighborhoods. If the grocery trucks are carrying mobile smart shelves, they can quickly configure and create a store outside the truck.
8
In-store ASRS. In-store ASRS will help stock a large inventory of items in a smaller retail space. Customers will be able to interact with the shelves to retrieve items.
9
Enhanced CCTV tracking shopper purchasing patterns. This will help the store generate valuable predictive data that can be used in inventory management to reduce costs.
SECURITY AND PRIVACY IMPLICATIONS
- Cameras being used to track customers. Facial and pattern recognition combined with AI/ML can be used to derive data.
- A new way of shoplifting. This is done by replacing an item on the shelf with something of similar weight.
- Facial recognition as a double-edged sword. Privacy laws could prevent facial recognition that nullifies many of the enhanced mechanisms for detecting and preventing theft.
- Receipt fraud. This is done by falsifying the purchase of an item, returning that item, and getting a refund. This would depend on the retailer and their fraud loss tolerance.
- Brick and mortar stores stealing information. These stores can try to subtly connect to your phone using Bluetooth, Wi-Fi, cellular and other similar methods to gather data on your location, movement, or any data they can derive.
- Attacks on telemetry. These are performed on sensors or electronic labels. Since ordering systems are triggered by telemetry, shipments are also triggered by telemetry. An attacker who can manipulate telemetry can control the supply chain and even the timing of logistics and shipping. The old and mature data manipulation class, called garbage in, garbage out (GIGO), has great effect on telemetry, and can produce effects like late ordering (leading to empty shelves), organic overstock (leading to spoiled food), storage overcapacity (leading to insecure storage, possibly on the ground near the loading dock), and other consequences.
Digitization
The rapid growth of e-commerce after the pandemic shutdowns, combined with the growth of cloud computing platforms, anything-as-a- service infrastructure, maturing mobile technology, improved global internet connectivity, etc. is driving digitization across all economic sectors.
Continuing rise of e-commerce. E-commerce was already a major player before year 2020 , but after the Covid-19 pandemic shutdown, e-commerce platforms and delivery services exploded and became the main method for purchasing goods and services. Because of the pandemic, most businesses now have a web presence that they continue to maintain as it provides an alternate revenue stream. Even after countries reopened, these established e-commerce businesses are expected to continue and thrive.
Cloud-based databases. Cloud-based databases hosted by major players, like Amazon AWS, Microsoft Azure, Oracle, and Google Cloud, form the backbone of the e-commerce boom. They provide easily accessible, scalable, fault-tolerant, feature-rich platforms with high availability on which the digitization wave is being built.
Centralized identity tracking database. With the world moving towards mobile computing technology, countries are slowly moving towards digital identities. We already use biometrics to pay for store items. This is expected to expand to daily services like government and banking services. The goal is for our digital identities to follow us and enable all types of transactions. This will be achieved using centralized identity tracking databases shared across multiple industries.
Centralized fleet management. Centralized fleet management for drones (both aerial and ground-based) enables the retailers to optimize the delivery chain and reduce both delivery time and costs.
SECURITY AND PRIVACY IMPLICATIONS
- The digital identity tracking database becomes a prime target. The database will take identity theft to the next level. Criminals will be able to create “brand new” digital people.
- Hijacking control of a fleet. This can lead to many different types of crimes such as a mule network to transport stolen goods or contraband items. The physical fleet can also represent a physical obstacle with mass malicious orders compelling an inconvenient number of delivery drones to a particular area. This can limit the movement of emergency or other services.
- Cloud-based services being susceptible to attacks. These attacks can be denial of service (DoS), man in the middle (MitM), hijacking of services, latency issues, authentication and management issues, data privacy, misconfiguration, and cloud supply chain issues (vulnerable API ecosystem).
- New ways to commit fraud. As e-commerce becomes mainstream, we will have to deal with increased fraud cases like card testing, phishing, refund fraud, account takeover fraud, larceny (e.g. porch pirates), fake e-commerce sites, and price manipulation.
- Privacy implications of the next-generation retail ecosystem’s enhanced ability to track customers as identifiable persons. The tracking described here goes beyond regular CCTV profiling (e.g., age, gender, and height), and involves data on the precise individual habits and needs of people who live in a particular location. This collected data is even more powerful if it is combined with social media profiling data — in the future this data could become a part of the metaverse. This can lead to a very targeted advertisement, opinion manipulation, or even highly accurate predictive behavior analysis.
AI/ML Services
AI/ML services in both the home and in smart stores track consumption and supply levels, run predictive analysis based on observed behavior patterns, and can automatically coordinate with each other to order more supplies.
Smart refrigerators and pantries track groceries. IoT-enabled refrigerators and pantries can track groceries and other supplies, automatically placing an order to restock when supplies fall below the user-set threshold.
Predictive analysis from smart assistants and smart homes. Smart assistants, like Alexa, Google Assistant, and Siri, will coordinate with smart homes to do predictive analysis of occupant behavior and automatically order supplies.
Smart shelves track and predict customers. Smart shelves in grocery and retail stores track and predict customer purchasing behavior. The stores will be able to accurately predict when customers are running short of supplies and can automatically order and deliver products to the customers' homes. Alternatively, the smart assistant in the home directly coordinates with the smart stores.
SECURITY AND PRIVACY IMPLICATIONS
- Cameras being used to track customers. Facial and pattern recognition using AI/ML can be used to derive data e.g. age, sex, race, etc.
- The possibility of collected data being sold. Stores like Amazon use AI/ML to predict buying needs and patterns — we can never be sure that companies are not selling this data, or leaking this data to advertisers.
- A wider range of data points. Third-party ad firms will use improved AI/ML algorithms together with years of extensive data to derive a wider range of datapoints about customers and shoppers, which is a big privacy concern.
Cashless Payments
Near field communication (NFC)-based payments, mobile payments, biometrics, e-gift cards, digital coupons, and even corporate-branded cryptocurrencies will all transform how customers do transactions. People will rarely use physical currency, which will be replaced by strongly authenticated and partially deregulated digital currencies.
NFC-based payments. This has become very common in many countries around the world, with contactless payment platforms gaining traction because of the pandemic. Apple Pay, Google Wallet, Samsung Pay, Alipay, are all popular NFC mobile payment apps. Credit and debit cards also use built-in chips for NFC transactions. Cellphone SIM cards tied to debit and credit accounts can also be used for payment.
Biometrics used for payment. Biometrics, both face and fingerprint, are already used for payment. This will soon roll out to stores that support Amazon Go and similar smart store models. Voice biometrics will also be added as an ID authentication mechanism.
Use of e-gift cards, e-vouchers, and digital food stamps and coupons. These are commonly used options for digital transactions. Some of the big tech companies will start issuing their own branded cryptocurrencies for use in their own stores and affiliated retailers and service providers.
Drive through as a service. This is where the vehicles’ plate and registration are used to charge back to either the driver or the owner of the vehicle. This method is already used to pay toll fees but will be extended for click-and-collect services, fast food drive-throughs, and retail services directly consumed by autonomous vehicles such as parts (purchase and installation of replacement tires), and simple repairs.
SECURITY AND PRIVACY IMPLICATIONS
- Attacks targeting gift cards or e-vouchers. These attacks could involve the following scenarios:
- Brute-forcing gifts cards or e-vouchers using a botnet
- Abuse of gifts card or e-voucher campaigns with bots
- Alternative markets that resell gifts cards or e-vouchers that were bought using stolen credit cards or credentials
- SIM-jacking attacks. This can be done if the payment account is tied to a user’s cellphone.
- Shift in targeted data. As biometrics become more prevalent, it will change what the criminals need to steal – they won’t need to steal the biometrics, just the data or hash representing it.
- New phishing tactics. Innovative methods and new types of phishing attacks will be devised to capture biometrics, including hacking store cameras to steal people’s faces.
Conclusion
The scenarios we have depicted are rooted in technologies seen and used today. We are already witnessing the beginnings of drone deliveries and 3D-printed food, for example. In this report, we looked ahead to see how these technologies or pillars will transform the retail industry in the next decade. With the demands highlighted by Covid-19, these innovations can seem necessary, even a natural progression for the IoT, cloud, and ML/AI in the field of retail. However, this progress comes with the introduction of new threats that could greatly implicate security and privacy.
Organizations are challenged to prepare for these issues as early as possible, and not to overlook the demands of security over that of the market. 2030 is not far off, and the next few years are crucial to creating a safer environment for consumers and in defining the next-generation retail supply chain to be both innovative and secure.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.










 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks