Malicious Actors Target Comm Apps such as Zoom, Slack, Discord
In our 2020 midyear report, we discussed how the Covid-19 pandemic had forced many organizations to shift from physical offices to virtual ones — a change that also led to the rise of messaging and video conferencing apps as indispensable tools for communication. While these apps have provided businesses a way of maintaining communication between employees, they have also caught the eye of malicious actors who are always looking to integrate new techniques in their malicious activities.
Zoom-based attacks have remained consistent
No other software has defined 2020 as much as the video conferencing app Zoom, which has exploded in popularity since the start of the pandemic. Given its high usage rate among schools, businesses, and individuals, it’s no surprise that cybercriminals have been focusing their efforts on Zoom-based attacks.
The most well-known malicious activity involving Zoom is probably “Zoombombing,” which involves pranksters crashing a meeting and then performing disruptive actions, such as spamming pornographic content or even just generally being a nuisance.
While annoying, Zoombombing is typically harmless in terms of security. On the other hand, we’ve encountered Zoom-related attacks that involve actual malware, which can potentially be more damaging to organizations and individuals. The most common Zoom-related attack technique is the use of Zoom installers bundled with malware.
In some cases, the attackers use fake Zoom installers to trick users into installing them on their machines. We encountered an example of this in May, after we found samples of malware files that were disguised as fake Zoom installers. While it could be difficult for the average user to distinguish the legitimate Zoom app from the fake ones, closer inspection shows that the malicious versions have significantly larger file sizes.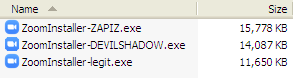
Figure 1. The file size of malicious Zoom copies compared with that of the legitimate installer
One of the malware samples (Trojan.Win32.ZAPIZ.A) is a backdoor with remote access features, allowing the attacker to gain access to the infected machine to perform malicious actions, such as stealing information. The other sample (Backdoor.Win32.DEVILSHADOW.THEAABO) has an installer that consists of a file containing malicious commands. Interestingly, both compromised installers installed a legitimate version of Zoom, likely to hide evidence of malicious activity from the user.
Aside from using compromised installers, we also found instances where malicious actors bundled legitimate installers with malware files. In April, we discovered an attack that used real Zoom installers that came with the RevCode WebMonitor RAT (Backdoor.Win32.REVCODE.THDBABO). This malware variant allows its operator to execute commands remotely, such as adding or deleting files, recording keystrokes, and gathering information.
Another example of this is the ZAPIZ malware (Trojan.Win32. ZAPIZ.A), a trojan that also comes bundled with a legitimate Zoom installer. Once downloaded, it will kill all running remote utilities, after which it will use PORT =5650/TCP for remote inbounding.
Based on our analysis, ZAPIZ will perform information theft, gathering the target machine’s usernames and its machine name — perhaps as a prelude to further attacks.
We also found an email sample where a malicious actor tried to extort money from the victim by threatening them with the release of compromised video footage — allegedly acquired via a hacked camera. 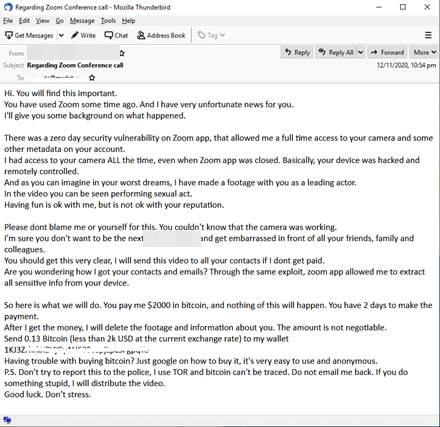
Abuse of other communication apps such as Discord and Slack
While Zoom remains perhaps the most popular communication app during the pandemic, it’s not the only one that cybercriminals have abused. We found evidence of attacks that integrate other communication services — specifically Slack and Discord — into their routines.
Slack has earned a loyal following over the years, with over 10 million daily active users as of 2019. However, we also found evidence of malicious actors making use of some of its features.
We recently found a ransomware variant (Ransom.Win32.CRYPREN.C) that, on the surface, seems fairly standard in terms of capabilities. It encrypts files with the following extensions (after which it will append the .encrypted suffix):
- .bmp
- .doc
- .docx
- .gif
- .jpeg
- .jpg
- .m2ts
- .m4a
- .mkv
- .mov
- .mp3
- .mp4
- .mpeg
- .mpg
- .png
- .ppt
- .pptx
- .txt
- .xls
- .xlsx
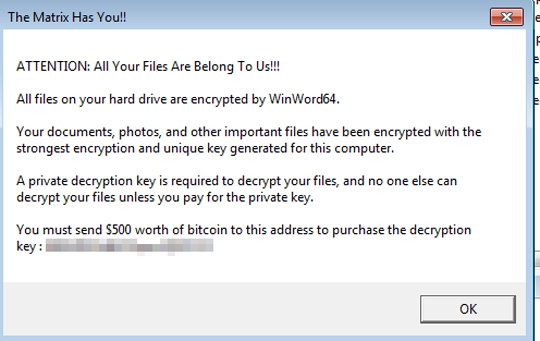
Figure 3. The ransom note for the Crypren ransomware
What makes Crypren interesting is its use of Slack webhooks to report its victims’ encryption status back to its command-and-control (C&C) server — a technique we haven’t encountered before.
Currently, it only sends back a minimal amount of data, namely computer and user names, the number of infected files, and the infection timestamp — indicating that the use of Slack for infection status reporting might still be in its testing phase.
Discord is another communication software that shares similar features with Slack (while also being notable for its widespread use in gaming communities). We found samples that show how malicious actors are using Discord as part of a campaign involving malicious spam emails that eventually end in an AveMaria or AgentTesla malware infection. We first observed the use of malicious spam to deliver these malware families in 2019 — however, the addition of Discord as part of its attack routine is relatively recent.
The malicious emails are typically either postal delivery notifications or invoices with an included DHL or TNT-themed attachment: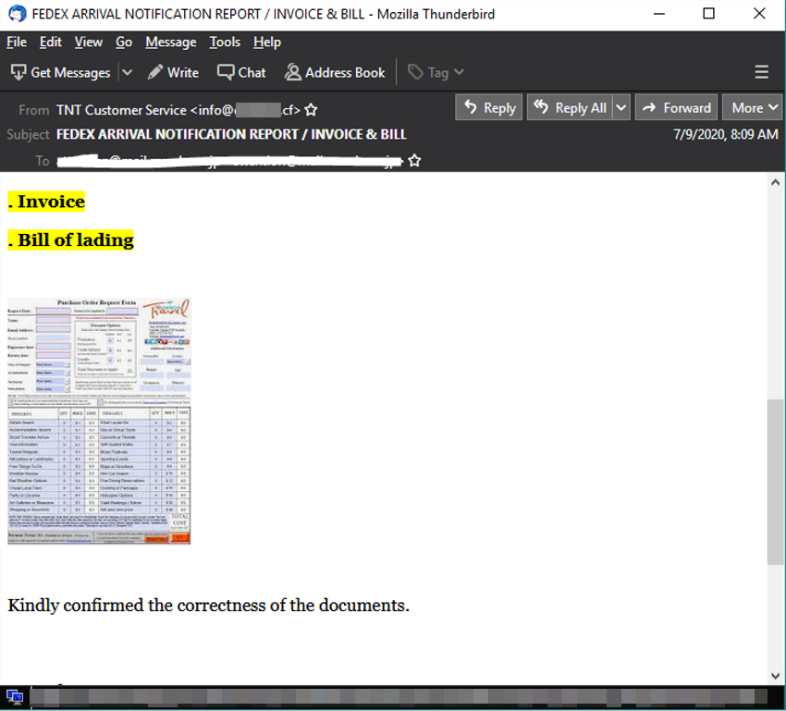
Figure 4. Spam mail sample
These emails come with embedded links — either in the images or the text — that point to a Discord URL with the following format: hxxps://cdn[.]discordapp[.]com/attachments/{ChannelID}/{AttachmentID}/example[.]exe. These URLs are used to host AveMaria and AgentTesla, which will then infect the users’ machines once they click on the executable.
The use of legitimate apps such as Slack and Discord as part of an attack may come down to a few simple reasons: they’re well-known, widely used, free, and provide some form of anonymity. Furthermore, users are not even required to have the apps installed to download files from them, making the process streamlined and efficient. Another possible reason that explains these programs' use is that they can pass off as normal legitimate network communication. Their popularity also amounts to a high chance that employees and end-users are already using these services.
Defending against attacks that abuse communication apps
Fortunately, defending against these types of attacks is relatively straightforward. In the case of the Zoom installers, the commonality between the attacks is that they are downloaded from places other than the official Zoom download page. The simplest way to avoid infection is to download communications apps (and all apps in general) only from official channels. This will ensure that the software is free from tampering.
Users should also avoid clicking on any links or downloading attachments from suspicious or unverified emails. If unsure, it would be a good idea to double-check with the alleged sender to confirm if they were the ones who sent the email.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks