Espionage as a Service: A Means to Instigate Economic Espionage
 View guide: Espionage as a Service
View guide: Espionage as a Service
Countries that spend huge amounts on new product, service, or technology research and development stand to lose billions of dollars to economic espionage attacks each year, according to a Federal Bureau of Investigation (FBI) national awareness campaign. In an effort to address this, United States President Obama and Chinese leader Xi Jinping signed an agreement in September 2015 promising that their countries would not conduct or condone economic espionage in cyberspace against each other.
Sadly, economic espionage should not only concern nation-states; any company, regardless of size, is at risk of losing intellectual property (trade secrets, information on new products and services currently in the works, etc.) to attackers, typically business rivals.
Economic espionage attacks can be aided by espionage-as-a-service offerings that are readily available in cybercriminal underground forums and markets and the Deep Web. Attackers can easily buy the tools they need to spy on and exfiltrate highly confidential corporate data or “company crown jewels” from rivals. They can even hire hackers to do the actual spying for them.
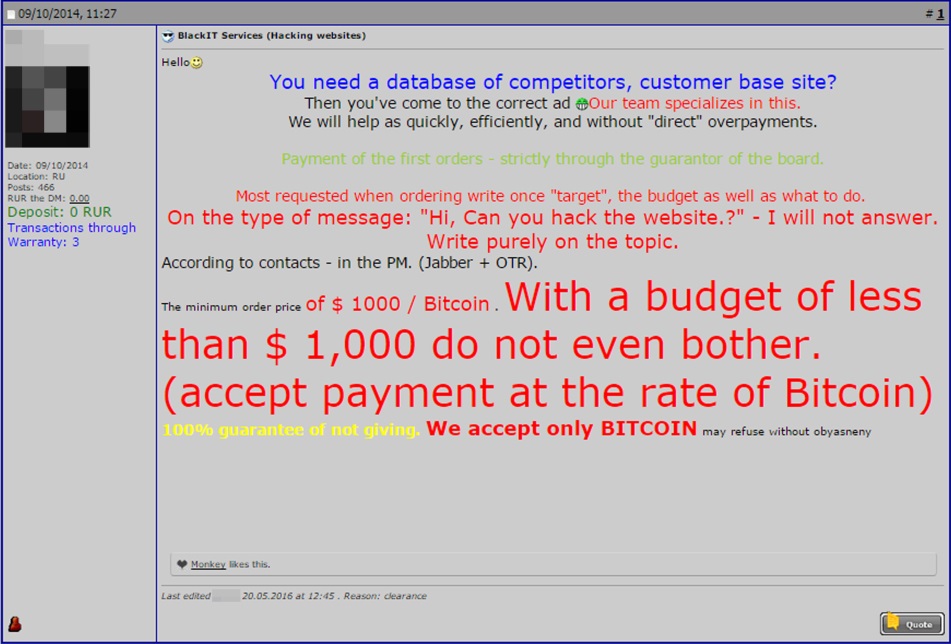 Figure 1: Russian underground forum ad for hacking a company’s database
Figure 1: Russian underground forum ad for hacking a company’s database
[VISIT: Deep Web Threat Intelligence Center]
How do espionage-as-a-service attacks work?
Espionage-as-a-service attacks use the same tools, tactics, procedures, and components as targeted attacks. The only difference? Espionage-as-a-service attacks have an additional component—peddling the stolen data to the highest bidders (typically to the targets’ business rivals) in underground markets or the Deep Web.
[READ: Understanding Targeted Attacks: The Six Components]
Attackers first gather intelligence on the intended target to pinpoint who to bait. Using the intel gathered during reconnaissance, the attackers typically send contextually relevant malware-laden spear-phishing emails to the chosen high-ranking corporate official. This helps ensure they get the credentials with the highest level of access required to infiltrate systems where company crown jewels are stored. Network command and control (C&C) is then established aided by backdoors, remote access Trojans (RATs), or other malware. Attackers then move laterally across the network to seek out top-secret data. The data is then exfiltrated to a site that only the attackers have access to for selling to the highest bidders or delivery to the individual or company that hired them.
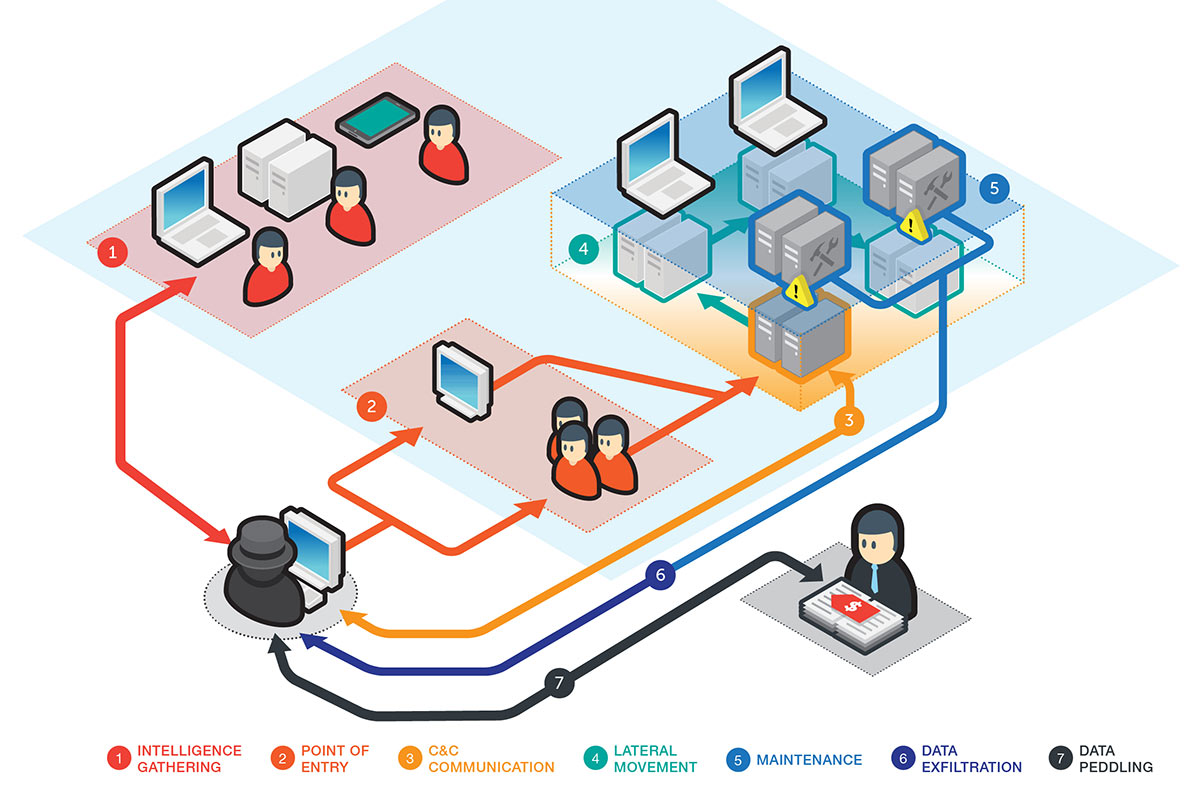 Figure 2: Espionage-as-a-service attack chain
Figure 2: Espionage-as-a-service attack chain
Espionage-as-a-service attacks affect a company’s bottom line. Data loss is, of course, an imminent risk, with other damaging effects like loss of competitive edge over rivals, damage to brand and reputation, and financial loss (potential profits, attack-recovery expenditures, etc.).
How can enterprises fight against espionage-as-a-service and related attacks?
Securing data and the network perimeter should always be the first steps in protecting against any kind of attack. The same is true when battling espionage-as-a-service and related attacks.
Companies are urged to classify the data they keep according to their level of confidentiality. They should segment their networks and limit who can access systems that hold top-secret data. They are also encouraged to train their employees to spot signs of attacks, thwarting them before they can progress and put their organizations’ bottom lines in great peril.
Employing a connected threat defense strategy that protects networks and systems through a wide mix of security technologies that work hand-in-hand is crucial. Companies should use next-generation security that provides maximum protection for endpoints with minimum impact.
[READ: XGen™ Endpoint Security]
For more in-depth information on and strategies to mitigate and/or address espionage-as-a-service and related attacks—what espionage as a service is, how it affects enterprises, and how to defend against it—read our latest executive brief, “Espionage as a Service."
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks