5 Facts You Might Have Missed About PoS Attacks of Recent Years

One hack after the next, large-scale data breaches, and high-risk vulnerabilities, are just a few of the many major security issues that have been chronically compromising organizations, users, and other businesses in 2014. Before we look forward to the rest of 2015, here's a recap of last year's biggest security stories—the ones that impacted a large number of users and various industries—so we can learn from past incidents.
1. 2014 was the “Year of PoS RAM Scrapers.”
Indeed, the year 2014 can be described as an explosion of data breaches and PoS RAM scrapers. High –profile targets in various industries, including retail and hospitality were victimized by PoS malware, causing an increase in the number of infected PoS systems in 2014 increased throughout the year.
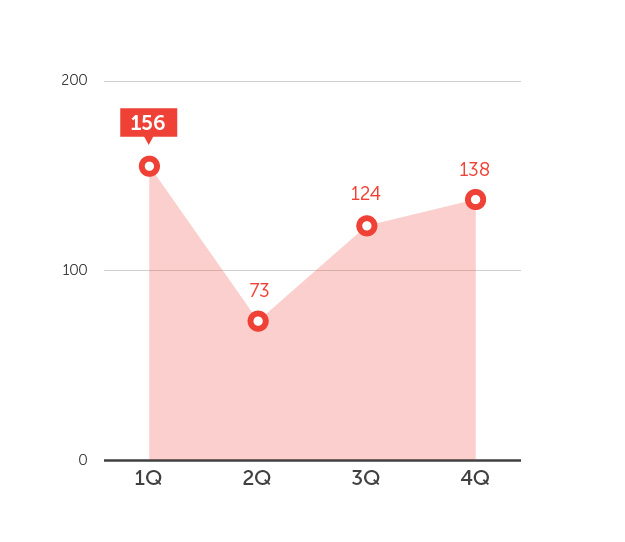
Number of Systems detected with POS Malware in 2014
2. 70 million personal records is the largest reported loss due to a PoS system breach.
In a data breach incident that happened during the holiday season of 2013, major U.S. retailer Target reported losing personal information, including names, mailing addresses, phone numbers or email addresses, of up to 70 million individuals. Other large-scale PoS breaches victimized customers of Home Depot and Kmart.
[Read: 5 Things We Can Learn from 2014 Data Breaches]
3. PoS malware have existed for years.
PoS malware has been in use for years now. Looking back, the earliest evidence of PoS RAM scraping was in Visa’s Data Security Alert issued on October 2, 2008. Senior threat researcher Numaan Huq talked about how PoS RAM scrapers started by installing debugging tools, and has since evolved to include multiple components, single binary packaging, networking, bot or C&C commands, kill switch functions, data encryption, customized binaries, and multiple exfiltration techniques.
[Read: Looking Back (and Forward) at PoS Malware]
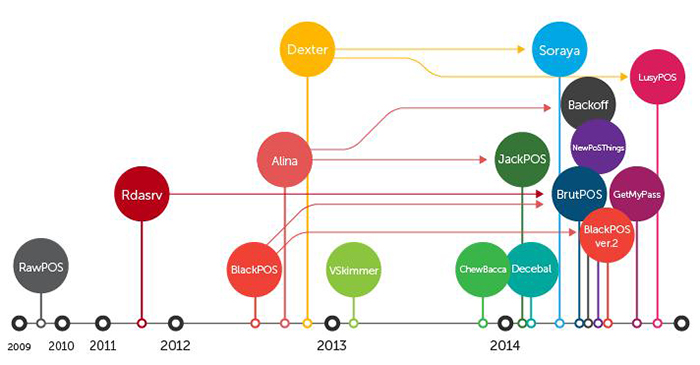
Evolution of Point-of-Sale (PoS) Malware
4. One in three infected PoS systems were found in the United States.
Trend Micro data shows that infected PoS systems in 2014 were evenly distributed across countries. Roughly one in three infected systems can be found in the United States.
[Read: A Year of Destructive Cyber Attacks Highlights the Need for Cyber-Preparedness]
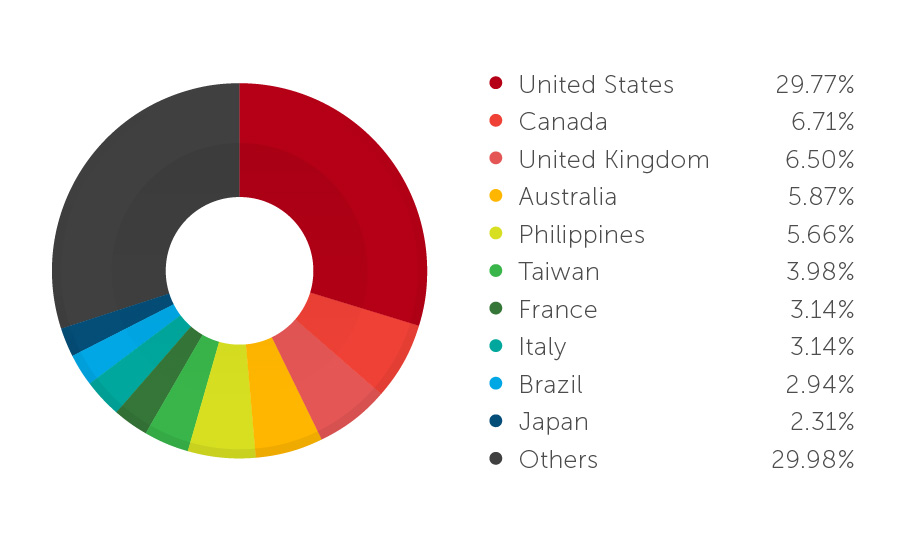
Country Distribution of Systems Where PoS Malware Were Found in 2014
5. BlackPoS is the most used PoS malware family in 2014.
BlackPoS, the popular malware variant that was used to attack Target and Home Depot systems, is the most used PoS malware family in 2014. Since the original version leaked out, this malware had been passed along in underground environments for revisions. Version 2.0 of this malware has been found disguising itself as a known antivirus software to avoid detection.
[Read:New BlackPOS Malware Emerges in the Wild, Targets Retail Accounts]
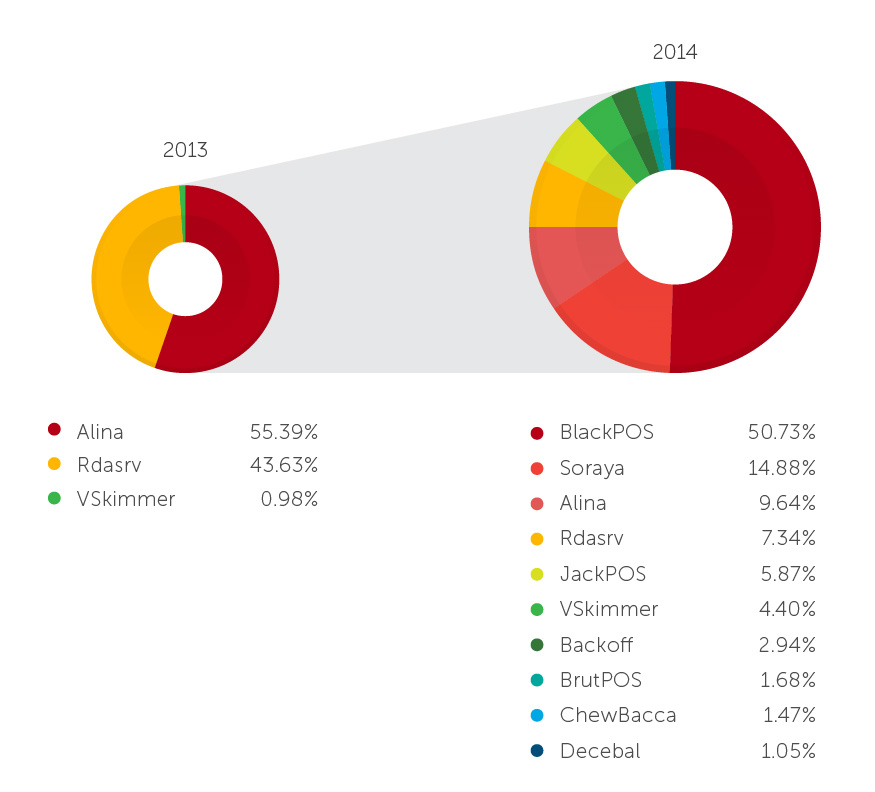
PoS Malware Family Distribution, 2013 vs 2014
2015 and Beyond
Knowing these, companies that use PoS systems should be aware of the various threats that infiltrate their network with the goal of gathering financial information from their clients. PoS systems are generally an easy target considering the wide use of unprotected systems around the world. However, there are advanced security technologies now available, such as application control and advanced network threat detection, which can help detect intrusion in time.
[Read: Defending Against PoS RAM Scrapers: Current Strategies and Next-Gen Technologies]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- LLM as a Judge: Evaluating Accuracy in LLM Security Scans
- The Silent Leap: OpenAI’s New ChatGPT Agent Capabilities and Security Risks
- Trend Micro State of AI Security Report 1H 2025
- The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
- Exploiting Trust in Open-Source AI: The Hidden Supply Chain Risk No One Is Watching
 Trend Micro State of AI Security Report 1H 2025
Trend Micro State of AI Security Report 1H 2025 AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions