Trojan.Win32.INJECTOR.EPLCRM
Trojan.PSW.Maran (IKARUS)
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan adds the following folders:
- %User Temp%\is-{Another Random Characters}.tmp → deleted afterwards
- %User Temp%\is-{Random Characters}.tmp → deleted afterwards
- %User Temp%\is-{Another Random Characters}.tmp\_isetup → deleted afterwards
- %ProgramData%\MyGuard
- %ProgramData%\MyGuard\Log
- %ProgramData%\MyGuard\Log\Cryptor Plus
- %Program Files%\CryptorPlus
- %Common Programs%\Cryptor Plus
- %System%\CPTEMP
- %System%\CPTEMP\CryptorPlus → deleted afterwards
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %ProgramData% is a version of the Program Files folder where any user on a multi-user computer can make changes to programs. This contains application data for all users. This is usually C:\ProgramData on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit), or C:\Documents and Settings\All Users on Windows Server 2003(32-bit), 2000(32-bit) and XP.. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Common Programs% is the folder that contains common program groups for all users, which is usually C:\Documents and Settings\All Users\Start Menu\Programs on Windows 2000, XP, and Server 2003, or C:\ProgramData\Microsoft\Windows\Start Menu\Programs on Windows Vista, 7, and 8.. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
It drops the following files:
- %ProgramData%\MyGuard\Log\Cryptor Plus\{Date that the malware was executed}.log
- %ProgramData%\MyGuard\CryptorTmp\20220803181356737331\System.zip
- %ProgramData%\MyGuard\SetupTmp.exe → originally dropped as %ProgramData%\MyGuard\SetupTmp.exe.tmp
- %System%\is-{Random Characters}.tmp\SetupTmp.tmp → deleted afterwards
- %User Temp%\is-{Another Random Characters}.tmp\_isetup\_RegDLL.tmp → deleted afterwards
- %User Temp%\is-{Another Random Characters}.tmp\_isetup\_shfoldr.dll → deleted afterwards
- %Program Files%\CryptorPlus\unins000.dat
- %Program Files%\CryptorPlus\unins000.exe → originally dropped as %Program Files%\CryptorPlus\is-{Random Characters}.tmp
- %System%\msvcr100.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\msvcp100.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ptrwide.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\fmsysotn.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\DeElev.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\elenon.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\MGCrypto.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\DrvOTInj32.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\DrvOTInj64.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\DllOTinj32V2.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ClipLDR32.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\DeShFile.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\GetOPath.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\GetOpath.sys → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\OpenList.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTAPI.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTAPI64.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ClipOTPS.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ClipOTPS64.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTCopy.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTCopy64.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTPrn.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTPrn64.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTPrev.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTPrev64.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTFileHelper.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTFile.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\HKOTFile64.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ClipOTPrn.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ItlsHKOT.Sys → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ItlsHKOT64.sys → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ItlsHKOTO.sys → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ItlsHKOT64O.sys → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\FilesOTUse.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ItlsOTN.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\ItlsinstdrvOT.exe → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\itlsNUOT.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\drivers\ItlsOTN.sys → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\URLGrab.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\MDIOTHook.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\miscfunc.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\AgentComMod.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\Exfn.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %System%\MgCryptoSHA.dll → originally dropped as %System%\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\CPManager.exe → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\Ionic.zip.dll → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\MgNetLib.dll → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\MgNetLog.dll → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\Interop.SHDocVw.dll → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\Interop.TaskScheduler.dll → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\System.Net.Json.dll → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\CPLng.Dat → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Program Files%\CryptroPlus\MyGuardTray.exe → originally dropped as %Program Files%\CryptroPlus\is-{Random Characters}.tmp
- %Common Programs%\Cryptor Plus\CPManager.lnk
- %Common Programs%\Cryptor Plus\unins000.lnk
(Note: %ProgramData% is a version of the Program Files folder where any user on a multi-user computer can make changes to programs. This contains application data for all users. This is usually C:\ProgramData on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit), or C:\Documents and Settings\All Users on Windows Server 2003(32-bit), 2000(32-bit) and XP.. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.. %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Common Programs% is the folder that contains common program groups for all users, which is usually C:\Documents and Settings\All Users\Start Menu\Programs on Windows 2000, XP, and Server 2003, or C:\ProgramData\Microsoft\Windows\Start Menu\Programs on Windows Vista, 7, and 8.)
It adds the following processes:
- "%ProgramData%\MyGuard\SetupTmp.exe" /Silent
- "%User Temp%\is-{Random Characters}.tmp\SetupTmp.tmp" /SL5="${Random Numbers},{Random Numbers},{Random Numbers},%ProgramData%\MyGuard\SetupTmp.exe" /Silent
- "cacls" "%ProgramData%\MyGuard" /T /C /E /P Everyone:F
- "cacls" "%ProgramData%\CryptorPlus" /T /C /E /P Everyone:F
- "%System%\instdrvOT.Exe"
- "%Program Files%\CryptorPlus\CPManager.exe"
- "%Program Files%\CryptorPlus\CPManager.exe" CPEXE
- "%System%\ClipLDR32.exe "
- "%Windows%\explorer.exe" %Program Files%\CryptorPlus\MyGuardTray.exe
- "%System%\DrvOTInj32.Exe" LItlsHKOT/ITLSHKOT.sys/ItlsHKOT64.sys/HKOTAPI.DLL/HKOTAPI64.DLL/*/svchost.exe/
(Note: %ProgramData% is a version of the Program Files folder where any user on a multi-user computer can make changes to programs. This contains application data for all users. This is usually C:\ProgramData on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit), or C:\Documents and Settings\All Users on Windows Server 2003(32-bit), 2000(32-bit) and XP.. %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.. %Program Files% is the default Program Files folder, usually C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- CPExe Check Mutex
It is injected into the following processes running in memory:
- explorer.exe
- other running Non-System Applications
Autostart Technique
This Trojan registers as a system service to ensure its automatic execution at every system startup by adding the following registry keys:
HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\
services\ItlsOTN\Instances
Altitude = 145600.4
HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\
services\ItlsOTN\Instances
Flags = 0
HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\
services\ItlsHKOT
Type = 1
HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\
services\ItlsHKOT
ErrorControl = 0
HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\
services\ItlsHKOT
Start = 4
HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\
services\ItlsHKOT
ImagePath = \??\%System%\ITLSHKOT.sys
HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\
services\ItlsOTN\Instances
DefaultInstance = ItIsOTN Instance
Other System Modifications
This Trojan deletes the following files:
- %User Temp%\is-{Random Characters}.tmp\SetupTmp.tmp
- %User Temp%\is-{Another Random Characters}.tmp\_isetup\_RegDLL.tmp
- %User Temp%\is-{Another Random Characters}.tmp\_isetup\_shfoldr.dll
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).)
It deletes the following folders:
- %User Temp%\is-{Another Random Characters}.tmp\
- %User Temp%\is-{Another Random Characters}.tmp\_isetup\
- %System%\CPTEMP\CryptorPlus
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000(32-bit), XP, and Server 2003(32-bit), or C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %System% is the Windows system folder, where it usually is C:\Windows\System32 on all Windows operating system versions.)
It adds the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
.cpd
" " = cpdfile
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
cpdfile\shell\cpdopen\
command
" " = %Program Files%\CryptorPlus\CPManager.exe %1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\msvcr100.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\msvcp100.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ptrwide.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\fmsysotn.exe = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\DeElev.exe = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\elenon.dll = 2
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\MGCrypto.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\DrvOTInj32.exe = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\DrvOTInj64.exe = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\DeShFile.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\GetOPath.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\GetOpath.sys = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\OpenList.exe = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTAPI.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTAPI64.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ClipOTPS.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ClipOTPS64.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTCopy.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTCopy64.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTPrn.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTPrn64.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTPrn64.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTPrev64.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTFileHelper.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTFile.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\HKOTFile64.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ClipOTPrn.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ItlsHKOT.Sys = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ItlsHKOT64.Sys = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ItlsHKOTO.sys = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\ItlsHKOT64O.sys = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\FilesOTUse.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\FilesOTUse.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\URLGrab.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\MDIOTHook.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\MDIOTHook.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%System%\MgCryptoSHA.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
Program Files%\CryptroPlus\CPManager.exe = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\Ionic.zip.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\MgNetLib.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\MgNetLog.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\Interop.SHDocVw.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\Interop.TaskScheduler.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\System.Net.Json.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
MyGuard Cryptor PLUS
Templateever = 4.0.1.9
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
Inno Setup: Setup Version = 5.2.3
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
InstallLocation = %Program Files%\CryptorPlus\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
Inno Setup: Icon Group = Cryptor Plus
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
Inno Setup: User = {User name}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
DisplayIcon = %Program Files%\CryptorPlus\CPManager.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
UninstallString = %Program Files%\CryptorPlus\unins000.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
QuietUninstallString = "%Program Files%\CryptorPlus\unins000.exe" /SILENT
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
Publisher = INZENT, Inc.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
URLInfoAbout = http://www.inzent.com/
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
NoModify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
NoRepair = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall
InstallDate = {Date Malware Installed}
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
MyGuard Client
SetupTmpVersion = 4.0.1.9
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
MyGuard Client
HKOTAPI.DLL = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\System.Net.Json.dll = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
%Program Files%\CryptroPlus\MyGuardTray.exe = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\SharedDLLs
Inno Setup: App Path = %Program Files%\CryptorPlus
It deletes the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
services\ItlsHKOT
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
services\ItlsHKOT\Enum
Other Details
This Trojan adds the following registry keys:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
.cpd
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
cpdfile
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
cpdfile\shell
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
cpdfile\shell\cdpopen
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
cpdfile\shell\cdpopen\
command
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
MyGuard Client
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
MyGuard Cryptor PLUS
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
OtherInfo
HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
OtherInfo\Injection
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
MyGuard CryptorPlus-Install-Unicode_is1
It connects to the following website to send and receive information:
- http://t2.{BLOCKED}b.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQwF4prw9S7mCbCEHD%2Fyl6nWPkczAQUe1tFz6%2FOy3r9MZIaarbzRutXSFACEHGgtzaV3bGvwjsrmhjuVMs%3D
- http://tl.{BLOCKED}d.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFBjxN%2BWY73bfUnSOp7HDKJ%2Fbx0wQUV4abVLi%2BpimK5PbC4hMYiYXN3LcCEEGrqHASLczL8h4qpdWGdb0%3D
- http://t1.{BLOCKED}b.com/ThawtePCA.crl
- http://t1.{BLOCKED}b.com/tl.crl
It does the following:
- It will only proceed with its routine if run as administrator.
- It sends the gathered information to the following URL:
- http://cowork.{BLOCKED}m.com/cp/approval.do?mod=authUser&{Stolen Information}
- IP Address
- Mac Address
- Workgroup
- Work type
- Country/Language
- Computer Name
- User Name
- Executed Malware Filename
- Malware Execution Time
- It displays the following during execution:
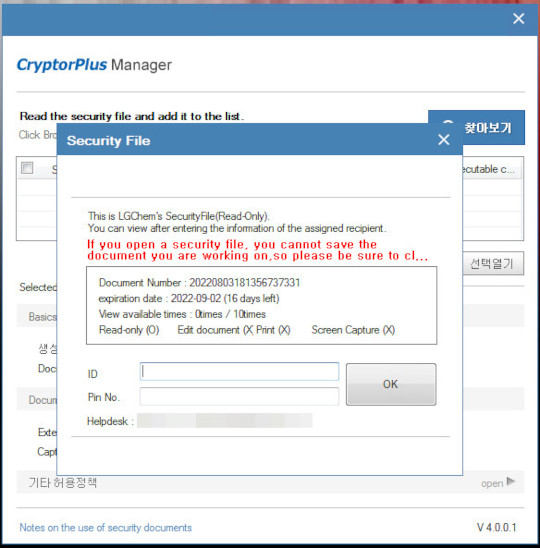
SOLUTION
Step 1
Trend Micro Predictive Machine Learning detects and blocks malware at the first sign of its existence, before it executes on your system. When enabled, your Trend Micro product detects this malware under the following machine learning name:
- TROJ.Win32.TRX.XXPE50FSX025
Step 2
Before doing any scans, Windows 7, Windows 8, Windows 8.1, and Windows 10 users must disable System Restore to allow full scanning of their computers.
Step 3
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 4
Restart in Safe Mode
Step 5
Restart in Safe Mode, and then delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\services\ItlsOTN\Instances
- DefaultInstance = ItIsOTN Instance
- DefaultInstance = ItIsOTN Instance
- In HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\services\ItlsOTN\Instances
- Altitude = 145600.4
- Altitude = 145600.4
- In HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\services\ItlsOTN\Instances
- Flags = 0
- Flags = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\services\ItlsHKOT
- Type = 1
- Type = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\services\ItlsHKOT
- ErrorControl = 0
- ErrorControl = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\services\ItlsHKOT
- Start = 4
- Start = 4
- In HKEY_LOCAL_MACHINE\SOFTWARE\ControlSet001\services\ItlsHKOT
- ImagePath = \??\%System%\ITLSHKOT.sys
- ImagePath = \??\%System%\ITLSHKOT.sys
Step 6
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.cpd
- " " = cpdfile
- " " = cpdfile
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\cpdfile\shell\cpdopen\command
- " " = %Program Files%\CryptorPlus\CPManager.exe %1
- " " = %Program Files%\CryptorPlus\CPManager.exe %1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\msvcr100.dll = 1
- %System%\msvcr100.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\msvcp100.dll = 1
- %System%\msvcp100.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ptrwide.dll = 1
- %System%\ptrwide.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\fmsysotn.exe = 1
- %System%\fmsysotn.exe = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\DeElev.exe = 1
- %System%\DeElev.exe = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\elenon.dll = 2
- %System%\elenon.dll = 2
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\MGCrypto.dll = 1
- %System%\MGCrypto.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\DrvOTInj32.exe = 1
- %System%\DrvOTInj32.exe = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\DrvOTInj64.exe = 1
- %System%\DrvOTInj64.exe = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\DeShFile.dll = 1
- %System%\DeShFile.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\GetOPath.dll = 1
- %System%\GetOPath.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\GetOpath.sys = 1
- %System%\GetOpath.sys = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\OpenList.exe = 1
- %System%\OpenList.exe = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTAPI.dll = 1
- %System%\HKOTAPI.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTAPI64.dll = 1
- %System%\HKOTAPI64.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ClipOTPS.dll = 1
- %System%\ClipOTPS.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ClipOTPS64.dll = 1
- %System%\ClipOTPS64.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTCopy.dll = 1
- %System%\HKOTCopy.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTCopy64.dll = 1
- %System%\HKOTCopy64.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTPrn.dll = 1
- %System%\HKOTPrn.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTPrn64.dll = 1
- %System%\HKOTPrn64.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTPrev.dll = 1
- %System%\HKOTPrev.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTPrev64.dll = 1
- %System%\HKOTPrev64.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTFileHelper.dll = 1
- %System%\HKOTFileHelper.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTFile.dll = 1
- %System%\HKOTFile.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\HKOTFile64.dll = 1
- %System%\HKOTFile64.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ClipOTPrn.dll = 1
- %System%\ClipOTPrn.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ItlsHKOT.Sys = 1
- %System%\ItlsHKOT.Sys = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ItlsHKOT64.Sys = 1
- %System%\ItlsHKOT64.Sys = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ItlsHKOTO.sys = 1
- %System%\ItlsHKOTO.sys = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ItlsHKOT64O.sys = 1
- %System%\ItlsHKOT64O.sys = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\FilesOTUse.dll = 1
- %System%\FilesOTUse.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\ItlsOTN.sys = 1
- %System%\ItlsOTN.sys = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\URLGrab.dll = 1
- %System%\URLGrab.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\MDIOTHook.dll = 1
- %System%\MDIOTHook.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\Exfn.dll = 1
- %System%\Exfn.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %System%\MgCryptoSHA.dll = 1
- %System%\MgCryptoSHA.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\CPManager.exe = 1
- %Program Files%\CryptroPlus\CPManager.exe = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\Ionic.zip.dll = 1
- %Program Files%\CryptroPlus\Ionic.zip.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\MgNetLib.dll = 1
- %Program Files%\CryptroPlus\MgNetLib.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\MgNetLog.dll = 1
- %Program Files%\CryptroPlus\MgNetLog.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\Interop.SHDocVw.dll = 1
- %Program Files%\CryptroPlus\Interop.SHDocVw.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\Interop.TaskScheduler.dll = 1
- %Program Files%\CryptroPlus\Interop.TaskScheduler.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\System.Net.Json.dll = 1
- %Program Files%\CryptroPlus\System.Net.Json.dll = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\CPLng.Dat = 1
- %Program Files%\CryptroPlus\CPLng.Dat = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs
- %Program Files%\CryptroPlus\MyGuardTray.exe = 1
- %Program Files%\CryptroPlus\MyGuardTray.exe = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\MyGuard Cryptor PLUS
- Templateever = 4.0.1.9
- Templateever = 4.0.1.9
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- Inno Setup: Setup Version = 5.2.3
- Inno Setup: Setup Version = 5.2.3
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- Inno Setup: App Path = %Program Files%\CryptorPlus\
- Inno Setup: App Path = %Program Files%\CryptorPlus\
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- InstallLocation = %Program Files%\CryptorPlus\
- InstallLocation = %Program Files%\CryptorPlus\
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- Inno Setup: Icon Group = Cryptor Plus
- Inno Setup: Icon Group = Cryptor Plus
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- Inno Setup: User = {User name}
- Inno Setup: User = {User name}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- DisplayIcon = %Program Files%\CryptorPlus\CPManager.exe
- DisplayIcon = %Program Files%\CryptorPlus\CPManager.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- UninstallString = %Program Files%\CryptorPlus\unins000.exe
- UninstallString = %Program Files%\CryptorPlus\unins000.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- QuietUninstallString = "%Program Files%\CryptorPlus\unins000.exe" /SILENT
- QuietUninstallString = "%Program Files%\CryptorPlus\unins000.exe" /SILENT
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- Publisher = INZENT, Inc.
- Publisher = INZENT, Inc.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- URLInfoAbout = http://www.inzent.com/
- URLInfoAbout = http://www.inzent.com/
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- NoModify = 1
- NoModify = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- NoRepair = 1
- NoRepair = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyGuard CryptorPlus-Install-Unicode_is1
- InstallDate = {Date Malware Installed}
- InstallDate = {Date Malware Installed}
- In HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\MyGuard Client
- SetupTmpVersion = 4.0.1.9
- SetupTmpVersion = 4.0.1.9
- In HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\OtherInfo\Injection
- HKOTAPI.DLL = 1
- HKOTAPI.DLL = 1
Step 7
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
- .cpd
- .cpd
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\cpdfile\shell\cdpopen\
- command
- command
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\cpdfile\shell\
- cdpopen
- cdpopen
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\cpdfile\
- shell
- shell
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
- cpdfile
- cpdfile
- In HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
- MyGuard Client
- MyGuard Client
- In HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
- MyGuard Cryptor PLUS
- MyGuard Cryptor PLUS
- In HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\OtherInfo\
- Injection
- Injection
- In HKEY_LOCAL_MACHINE\SOFTWARE\ITM System\
- OtherInfo
- OtherInfo
- In HKEY_LOCAL_MACHINE\SOFTWARE\
- ITM System
- ITM System
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\
- MyGuard CryptorPlus-Install-Unicode_is1
- MyGuard CryptorPlus-Install-Unicode_is1
Step 8
Search and delete these files
- %ProgramData%\MyGuard\Log\Cryptor Plus\{Date that the malware was executed}.log
- %ProgramData%\MyGuard\CryptorTmp\20220803181356737331\System.zip
- %ProgramData%\MyGuard\SetupTmp.exe
- %Program Files%\CryptorPlus\unins000.dat
- %Program Files%\CryptorPlus\unins000.exe
- %System%\msvcr100.dll
- %System%\msvcp100.dll
- %System%\ptrwide.dll
- %System%\fmsysotn.exe
- %System%\DeElev.exe
- %System%\elenon.dll
- %System%\MGCrypto.dll
- %System%\DrvOTInj32.exe
- %System%\DrvOTInj64.exe
- %System%\DllOTinj32V2.exe
- %System%\ClipLDR32.exe
- %System%\DeShFile.dll
- %System%\GetOPath.dll
- %System%\GetOpath.sys
- %System%\OpenList.exe
- %System%\HKOTAPI.dll
- %System%\HKOTAPI64.dll
- %System%\ClipOTPS.dll
- %System%\ClipOTPS64.dll
- %System%\HKOTCopy.dll
- %System%\HKOTCopy64.dll
- %System%\HKOTPrn.dll
- %System%\HKOTPrn64.dll
- %System%\HKOTPrev.dll
- %System%\HKOTPrev64.dll
- %System%\HKOTFileHelper.dll
- %System%\HKOTFile.dll
- %System%\HKOTFile64.dll
- %System%\ClipOTPrn.dll
- %System%\ItlsHKOT.Sys
- %System%\ItlsHKOT64.sys
- %System%\ItlsHKOTO.sys
- %System%\ItlsHKOT64O.sys
- %System%\FilesOTUse.dll
- %System%\ItlsOTN.dll
- %System%\ItlsinstdrvOT.exe
- %System%\itlsNUOT.dll
- %System%\drivers\ItlsOTN.sys
- %System%\URLGrab.dll
- %System%\MDIOTHook.dll
- %System%\miscfunc.dll
- %System%\AgentComMod.dll
- %System%\Exfn.dll
- %System%\MgCryptoSHA.dll
- %Program Files%\CryptroPlus\CPManager.exe
- %Program Files%\CryptroPlus\Ionic.zip.dll
- %Program Files%\CryptroPlus\MgNetLib.dll
- %Program Files%\CryptroPlus\MgNetLog.dll
- %Program Files%\CryptroPlus\Interop.SHDocVw.dll
- %Program Files%\CryptroPlus\Interop.TaskScheduler.dll
- %Program Files%\CryptroPlus\System.Net.Json.dll
- %Program Files%\CryptroPlus\CPLng.Dat
- %Program Files%\CryptroPlus\MyGuardTray.exe
- %Common Programs%\Cryptor Plus\CPManager.lnk
- %Common Programs%\Cryptor Plus\unins000.lnk
Step 9
Search and delete these folders
- %ProgramData%\MyGuard\Log\Cryptor Plus
- %ProgramData%\MyGuard\Log
- %ProgramData%\MyGuard
- %Program Files%\CryptorPlus
- %Common Programs%\Cryptor Plus
- %System%\CPTEMP
Step 10
Restart in normal mode and scan your computer with your Trend Micro product for files detected as Trojan.Win32.INJECTOR.EPLCRM. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 11
Scan your computer with your Trend Micro product to delete files detected as Trojan.Win32.INJECTOR.EPLCRM. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check the following Trend Micro Support pages for more information:
Did this description help? Tell us how we did.


