TROJ_CRYPLOCK
Windows


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It connects to certain websites to send and receive information.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Trojan drops the following copies of itself into the affected system:
- %All Users Profile%\Application Data\{random folder name}\01000000
- %Windows%\{random 8 letters}.exe
(Note: %All Users Profile% is the All Users folder, where it usually is C:\Documents and Settings\All Users on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\ProgramData on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.. %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
It drops the following file(s)/component(s):
- %All Users Profile%\Application Data\{random folder name}\00000000
- %All Users Profile%\Application Data\{random folder name}\02000000
- %All Users Profile%\Application Data\{random folder name}\03000000 - copy of ransom note
- %All Users Profile%\Application Data\{random folder name}\04000000
(Note: %All Users Profile% is the All Users folder, where it usually is C:\Documents and Settings\All Users on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\ProgramData on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
It adds the following processes:
- explorer.exe
It creates the following folders:
- %All Users Profile%\Application Data\{random folder name}
(Note: %All Users Profile% is the All Users folder, where it usually is C:\Documents and Settings\All Users on Windows 2000, Windows Server 2003, and Windows XP (32- and 64-bit); C:\ProgramData on Windows Vista (32- and 64-bit), Windows 7 (32- and 64-bit), Windows 8 (32- and 64-bit), Windows 8.1 (32- and 64-bit), Windows Server 2008, and Windows Server 2012.)
It injects codes into the following process(es):
- created explorer.exe
Autostart Technique
This Trojan adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
{random 8 letters} = "%Windows%\{random 8 letters}.exe"
Information Theft
This Trojan gathers the following data:
- Machine GUID
- Computer name
Other Details
This Trojan connects to the following website to send and receive information:
- js-static.ru:443/topic.php
It encrypts files with the following extensions:
- 3ds
- 3fr
- 3pr
- 7z
- ab4
- ac2
- accdb
- accde
- accdr
- accdt
- acr
- adb
- agd1
- ai
- ait
- al
- apj
- arw
- asm
- asp
- awg
- backup
- backupdb
- bak
- bdb
- bgt
- bik
- bkp
- blend
- bpw
- cdf
- cdr
- cdr3
- cdr4
- cdr5
- cdr6
- cdrw
- cdx
- ce1
- ce2
- cer
- cfp
- cgm
- cib
- cls
- cmt
- cpi
- cpp
- cr2
- craw
- crt
- crw
- csh
- csl
- css
- csv
- dac
- db
- db-journal
- db3
- dbf
- dc2
- dcr
- dcs
- ddd
- ddoc
- ddrw
- der
- design
- dgc
- djvu
- dng
- doc
- docm
- docx
- dot
- dotm
- dotx
- drf
- drw
- dwg
- dxb
- erbsql
- erf
- exf
- fdb
- ffd
- fff
- fh
- fhd
- fpx
- fxg
- gray
- grey
- gry
- hbk
- hpp
- ibank
- ibd
- ibz
- idx
- iiq
- incpas
- jpeg
- jpg
- js
- kc2
- kdbx
- kdc
- kpdx
- lua
- mdb
- mdc
- mef
- mfw
- mmw
- moneywell
- mos
- mpg
- mrw
- myd
- ndd
- nef
- nop
- nrw
- ns2
- ns3
- ns4
- nsd
- nsf
- nsg
- nsh
- nwb
- nx1
- nx2
- nyf
- odb
- odf
- odg
- odm
- odp
- ods
- odt
- orf
- otg
- oth
- otp
- ots
- ott
- p12
- p7b
- p7c
- pat
- pcd
- pef
- pem
- pfx
- php
- pl
- pot
- potm
- potx
- ppam
- pps
- ppsm
- ppsx
- ppt
- pptm
- pptx
- ps
- psafe3
- psd
- ptx
- py
- ra2
- raf
- rar
- raw
- rdb
- rtf
- rw2
- rwl
- rwz
- s3db
- sas7bdat
- sav
- sd0
- sd1
- sda
- sdf
- sldm
- sldx
- sql
- sqlite
- sqlite3
- sqlitedb
- sr2
- srf
- srw
- st4
- st5
- st6
- st7
- st8
- stc
- std
- sti
- stw
- stx
- sxc
- sxd
- sxg
- sxi
- sxm
- sxw
- txt
- wb2
- x3f
- xla
- xlam
- xll
- xlm
- xls
- xlsb
- xlsm
- xlsx
- xlt
- xltm
- xltx
- xlw
- xml
- ycbcra
- zip
It renames encrypted files using the following names:
- {original file name and extension}.encrypted
NOTES:
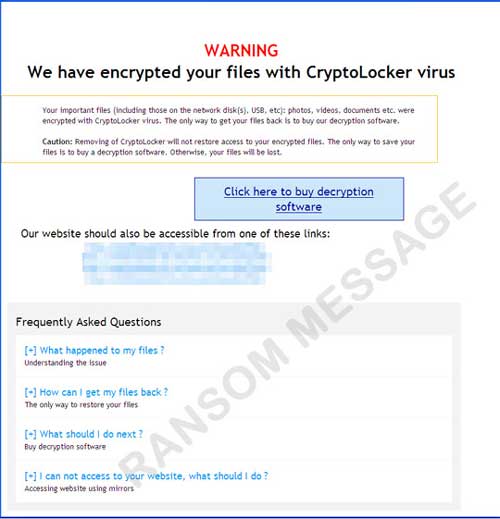
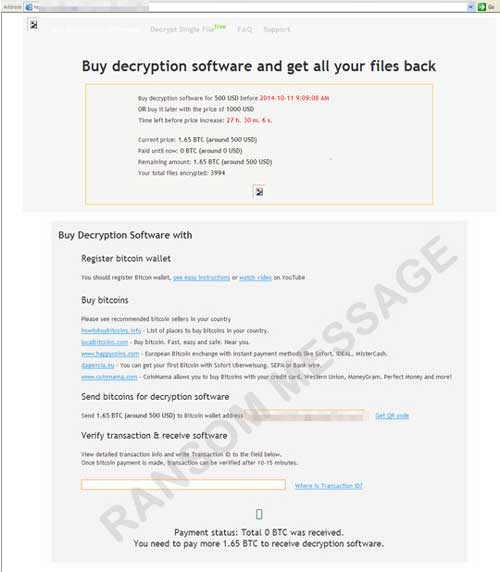
It drops the ransom note, DECRYPT_INSTRUCTIONS.html, to every directory it encrypts.
It deletes shadow copies by executing the following command:
- vssadmin.exe Delete Shadows /All /Quiet
It displays the following ransom message: