RANSOM64_POSIONFANG.THGAOAH
Trojan.Ransom.PoisonFang.A (Bitdefender), Trojan-Ransom.PoisonFang (Ikarus)
Windows


Threat Type: Ransomware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This Ransomware arrives via removable drives. It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It disables antivirus services. This is done to allow this malware to perform its routines, avoiding removal from the system.
It uses the system's central processing unit (CPU) and/or graphical processing unit (GPU) resources to mine cryptocurrency.
TECHNICAL DETAILS
Arrival Details
This Ransomware arrives via removable drives.
It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Installation
This Ransomware drops the following files:
- %Windows%\fang.ico
- %Windows%\P0150N\AngleSharp.dll
- %Windows%\P0150N\Bunifu_UI_v1.5.3.dll
- %Windows%\P0150N\EntityFramework.dll
- %Windows%\P0150N\EntityFramework.SqlServer.dll
- %Windows%\P0150N\NamedPipeWrapper.dll
- %Windows%\P0150N\Newtonsoft.Json.dll
- %Windows%\P0150N\PoisonBrowserExtractor.exe (detected as RANSOM_POSIONFANG.THGAOAH)
- %Windows%\P0150N\PoisonfangService.exe (also detected as RANSOM64_POSIONFANG.THGAOAH)
- %Windows%\P0150N\PoisonfangUI.exe (also detected as RANSOM64_POSIONFANG.THGAOAH)
- %Windows%\P0150N\System.Data.SQLite.dll
- %Windows%\P0150N\System.Data.SQLite.EF6.dll
- %Windows%\P0150N\System.Data.SQLite.Linq.dll
- %Windows%\P0150N\x64\SQLite.Interop.dll
- %Windows%\P0150N\x86\SQLite.Interop.dll
(Note: %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
It creates the following folders:
- %Windows%\P0150N
(Note: %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
Autostart Technique
This Ransomware adds and runs the following services:
- Poisonfang (%Windows%\P0150N\PoisonfangDropper.exe)
(Note: %Windows% is the Windows folder, where it usually is C:\Windows on all Windows operating system versions.)
Other System Modifications
This Ransomware modifies the following registry entries:
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows\OneDrive
DisableFileSyncNGSC = 1
HKEY_CLASSES_ROOT\.fang\DefaultIcon
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows NT\SystemRestore
DisableSR = 1
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows NT\SystemRestore
DisableConfig = 1
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
services\Poisonfang
DelayedAutostart = 0x00000000
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
services\Poisonfang
ErrorControl = 0x00000001
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
services\Poisonfang
ImagePath = "%Windows%\P0150N\PoisonfangService.exe"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
services\Poisonfang
ObjectName = LocalSystem
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
services\Poisonfang
Start = 0x00000002
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
services\Poisonfang
Type = 0x00000010
Propagation
This Ransomware drops the following copy(ies) of itself in all removable drives:
- drop.exe
- autorun.inf (drop file for automatic execution)
- [autorun]
- UseAutoPlay=1
- open=drop.exe
- shell\open\command=drop.exe
- shell\explore\command=drop.exe
Process Termination
This Ransomware terminates the following services if found on the affected system:
- [Disables Other Security Components & Event Logs]
- wscsvc (Windows Security Center Service)
- wuauserv (Windows Update AutoUpdate Service)
- BITS (Background Intelligent Transfer Service)
- WerSvc (Windows Error Reporting Service)
- EventSystem (Supports System Event Notification Service)
- EventLog (Windows Event Log Service)
It disables antivirus services by terminating the following services if found on the affected system:
- SepMasterService (Symantec Endpoint Protection)
- SmcService (Symantec Management Client)
- SNAC (Symantec Network Access Control)
- mcshield (McAfee On-Access Antivirus Scanner)
- windefend (Microsoft Windows Defender)
- msmpsvc (Microsoft Protection Service)
- msmpeng (Windows Defender Core Service)
- savservice (Sophos Antivirus)
- aveservice (Avira GmbH AntiVir AVE Service)
- \"avast! antivirus\" (Avast Antivirus)
- immunetprotect (Immunet Antivirus)
- fsma (Fsecure)
- antivirservice (Antivir Service)
- avguard (Avira Free Antivirus)
- fpavserver (F-PROT Antivirus system service)
- pshost (Panda Host Service)
- pavsrv (Panda Antivirus Service)
- bdss (Bitdefender Scan Server)
- abmainsv (ArcaBit Main Service)
- ikarus-guardx (Ikarus Antivirus)
- ekrn (Eset Nod32)
- avkproxy (G Data AntiVirus Proxy)
- klblmain (Kaspersky Anti-Virus Service)
- vbservprof (VirusBuster)
- clamav (ClamAV antivirus)
- SBAMSvc (Sunbelt Software Anti Malware Service)
- navapsvc (Norton AntiVirus Auto-Protect Service)
- AVP (Kaspersky Internet Security)
- bdagent (Bitdefender Agent)
- bdwxtag (bitdefender wallet agent)
Download Routine
This Ransomware connects to the following URL(s) to download its component file(s):
- https://victimblob.blob.core.{BLOCKED}s.net/poisondrop/Poisondrop.zip
- https://victimblob.blob.core.{BLOCKED}s.net/poisondrop/drop (removable drive spreader)
- https://tinyurl.com/{BLOCKED}lu (malicious link that will be sent to the victim's facebook friends)
Other Details
This Ransomware connects to the following URL(s) to check for an Internet connection:
- http://clients3.google.com/generate_204
It encrypts files with the following extensions:
- .123
- .3dm
- .3ds
- .3g2
- .3gp
- .602
- .7z
- .ARC
- .PAQ
- .accdb
- .aes
- .ai
- .asc
- .asf
- .asm
- .asp
- .avi
- .backup
- .bak
- .bat
- .bmp
- .brd
- .bz2
- .cgm
- .class
- .cmd
- .cpp
- .crt
- .csr
- .csv
- .db
- .dbf
- .dch
- .der
- .dif
- .dip
- .djvu
- .doc
- .docb
- .docm
- .docx
- .dot
- .dotm
- .dotx
- .dwg
- .edb
- .eml
- .fla
- .flv
- .frm
- .gif
- .gpg
- .gz
- .hwp
- .ibd
- .iso
- .jar
- .java
- .jpeg
- .jpg
- .js
- .jsp
- .key
- .lay
- .lay6
- .ldf
- .m3u
- .m4u
- .max
- .mdb
- .mdf
- .mid
- .mkv
- .mml
- .mov
- .mp3
- .mp4
- .mpeg
- .mpg
- .msg
- .myd
- .myi
- .nef
- .odb
- .odg
- .odp
- .ods
- .odt
- .onetoc2
- .ost
- .otg
- .otp
- .ots
- .ott
- .p12
- .pas
- .pem
- .pfx
- .php
- .pl
- .png
- .pot
- .potm
- .potx
- .ppam
- .pps
- .ppsm
- .ppsx
- .ppt
- .pptm
- .pptx
- .ps1
- .psd
- .pst
- .rar
- .raw
- .rb
- .rtf
- .sch
- .sh
- .sldm
- .sldx
- .slk
- .sln
- .snt
- .sql
- .sqlite3
- .sqlitedb
- .stc
- .std
- .sti
- .stw
- .suo
- .svg
- .swf
- .sxc
- .sxd
- .sxi
- .sxm
- .sxw
- .tar
- .tbk
- .tgz
- .tif
- .tiff
- .txt
- .uop
- .uot
- .vb
- .vbs
- .vcd
- .vdi
- .vmdk
- .vmx
- .vob
- .vsd
- .vsdx
- .wav
- .wb2
- .wk1
- .wks
- .wma
- .wmv
- .xlc
- .xlm
- .xls
- .xlsb
- .xlsm
- .xlsx
- .xlt
- .xltm
- .xltx
- .xlw
- .zip
- .c
- .py
- .st
It does the following:
- It removes the following folders from the system so that the victim would not be able to access it anymore:
- CommonDesktopDirectory
- CommonDocuments
- CommonMusic
- CommonPictures
- CommonVideos
- Desktop
- DesktopDirectory
- Favorites
- UserProfile
- Personal
- MyComputer
- MyMusic
- MyPictures
- MyVideos
- [PoisonBrowserExtractor.exe]
- It extracts the credentials from the browser.
- It attempts to gather the password from the Login Data (SQLite) file of google chrome and create the tempDb in %temp%
- It attempts to transfer the data through Pipe Channel in JSON format
- [PoisonfangService.exe]
- It tries to spread itself via facebook by hacking the facebook credentials, getting the list of all the connected users and send the messages with time interval.
- It spreads in removable drive.
- It has ransomware capabilities and mining capabilities.
- It collects the geolocation and IP address of the victim.
- It uses the following details for its coin mining routine:
- pool: mine.p2pool.com:9332
- wallet: Jtjoy2VeFRtseq4mTyHgtisaEqAT4Sidw
- It kills the backup process by:
- Executing the command: taskkill /f /im OneDrive.exe
- Disables the file sync process
- Attempts to uninstall OneDrive using the command: %System Root%\OneDriveSetup.exe /uninstall
- It deletes the Volume Shadow Copies by executing the following commands:
- vssadmin.exe Delete Shadows /All /Quiet
- WMIC.exe shadowcopy delete /nointeractive
- It disables the system restore point from the system by executing the command: %System Root%\bcdedit.exe /set {default} recoveryenabled No
- It tries to suppress failures during boot by executing the command: %System Root%\bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
It uses the system's central processing unit (CPU) and/or graphical processing unit (GPU) resources to mine cryptocurrency. This behavior makes the system run abnormally slow.
Ransomware Routine
This Ransomware avoids encrypting files found in the following folders:
- $Recycle.Bin
- Special Folders (System.Environment.SpecialFolder)
It appends the following extension to the file name of the encrypted files:
- .fang
NOTES:
It executes %Windows%\P0150N\PoisonfangUI.exe which shows the following ransom notes:
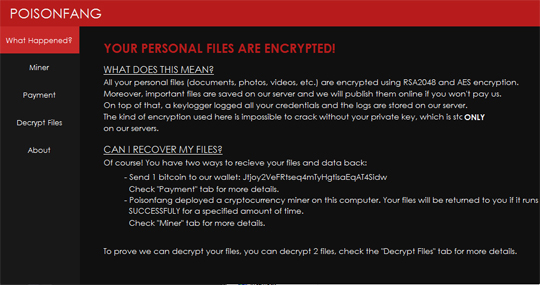
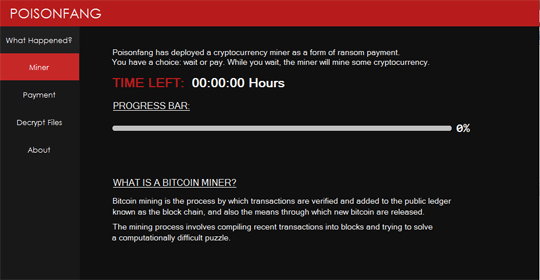
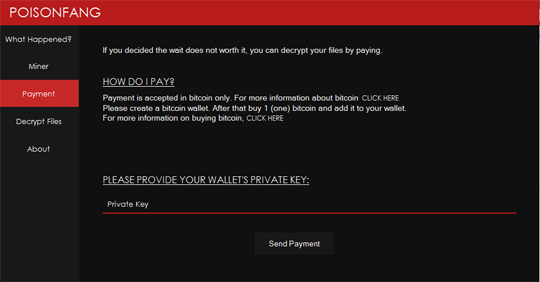
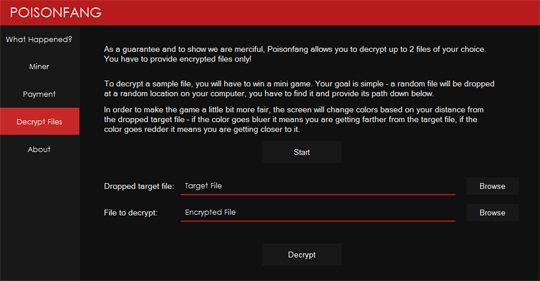
It also changes the encrypted file's icon as seen in the image below:

SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Restart in Safe Mode
Step 4
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\OneDrive
- DisableFileSyncNGSC = 1
- HKEY_CLASSES_ROOT\.fang\DefaultIcon
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\SystemRestore
- DisableSR = 1
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\SystemRestore
- DisableConfig = 1
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- DelayedAutostart = 0x00000000
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- ErrorControl = 0x00000001
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- ImagePath = "%Windows%\P0150N\PoisonfangService.exe"
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- ObjectName = LocalSystem
- Start = 0x00000002
- Type = 0x00000010
- HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\OneDrive
- DisableFileSyncNGSC = 1
- HKEY_CLASSES_ROOT\.fang\DefaultIcon
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\SystemRestore
- DisableSR = 1
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\SystemRestore
- DisableConfig = 1
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- DelayedAutostart = 0x00000000
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- ErrorControl = 0x00000001
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- ImagePath = "%Windows%\P0150N\PoisonfangService.exe"
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- ObjectName = LocalSystem
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- Start = 0x00000002
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Poisonfang
- Type = 0x00000010
Step 5
Search and delete this folder
- %Windows%\P0150N
Step 6
Search and delete these files
- %Windows%\fang.ico
- {Removable Drive Letter}:\drop.exe
- {Removable Drive Letter}:\autorun.inf
Step 7
Restart in normal mode and scan your computer with your Trend Micro product for files detected as RANSOM64_POSIONFANG.THGAOAH. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 8
Restore encrypted files from backup.
NOTES:
Enabling Volume Shadow Service
- Run the command prompt (cmd.exe) as administrator.
- Enable Volume Shadow Service by typing the following command:
net start vss
Enabling Windows Error Recovery
- Run the command prompt (cmd.exe) as administrator.
- Enable Windows Error Recovery Screen on Startup use the following command:
bcdedit /set {default} bootstatuspolicy displayallfailures
Enabling Startup Repair
- Run the command prompt (cmd.exe) as administrator.
- Enable Startup Repair use the following command:
/bcedit /set {default} recoveryenabled Yes
Did this description help? Tell us how we did.



