HKTL_RADMIN.GA
RemAdm-RemoteAdmin. (McAfee); Trojan.Win32.Generic!BT (Sunbelt); TR/Virtl.9946 (Avira); Riskware/RAdmin (Fortinet)
Windows


Threat Type: Hacking Tool
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This hacking tool arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites. It arrives as a component bundled with malware/grayware packages.
It listens on ports. It executes commands from a remote malicious user, effectively compromising the affected system.
TECHNICAL DETAILS
Arrival Details
This hacking tool arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It arrives as a component bundled with malware/grayware packages.
Other System Modifications
This hacking tool adds the following registry keys:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\iplist
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
It adds the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\iplist
{number} = {hex string}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
Prot = {hex value}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
Timeout = {hex value}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
EnableLogFile = {0 or 1}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
LogFilePath = {full path of the log file, default is "c:\logfile.txt"}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
FilterIp = {0 or 1}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
DisableTrayIcon = {0 or 1}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
AutoAllow = {0 or 1}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
AskUser = {0 or 1}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
EnableEventLog = {0 or 1}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
NTAuthEnabled = {0 or 1}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
MSDTC\Parameters
Para = {hex string}
Backdoor Routine
This hacking tool listens on the following ports:
- 4899 (default)
It executes the following commands from a remote malicious user:
- Logs user on/off
- Captures screen changes
- Transfer files
- Shut down
- Mouse and keyboard control
Dropping Routine
This hacking tool drops the following files:
- {variable path and filename, default is "c:\logfile.txt"}
NOTES:
This hacking tool allows remote user full control of the system.
It accepts the following parameters:
- /setup -shows windows dialog box with setup settings (install/remove driver, password, port number)
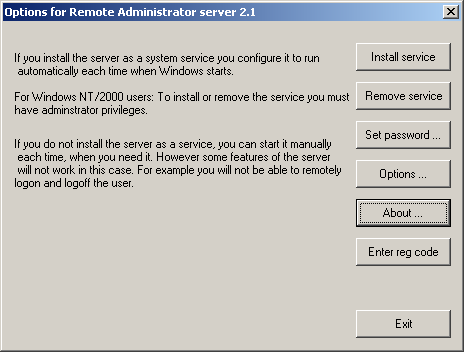
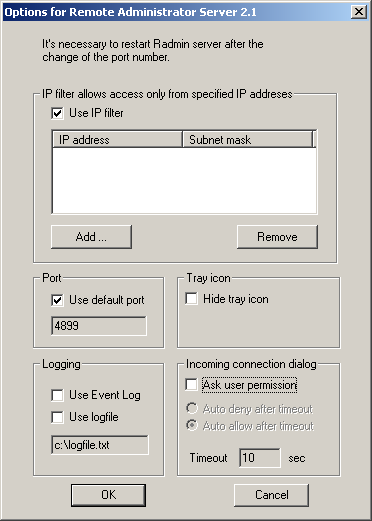
- /pass:xxxxx - specify a password
- /port:xxxxx - specify a port number
- /save - save password and port number and/or password when used with /pass and/or /port. When used without /pass and /port, default port and empty password will be saved.
- /install - installs the service and driver. The driver raddrv.dll is required for this to work.
- /uninstall - uninstalls the service and driver, if present
- /installservice - installs the service only
- /uninstallservice - uninstalls service only
- /installdrv - installs the driver
- /uninstalldrv - uninstalls the driver
- /silence - don't show message boxes, in /install, /uninstall or /save commands.
- /unregister - delete a registered key
- /?, /help, /h - help screen
- /intsetup - initialize set-up, displays the following dialog box:
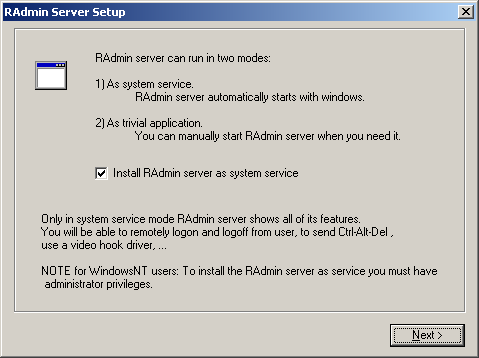
- /start - starts the hacktool
- /stop - stops the hacktool
- /intuninstall - uninstalls the hacktool
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Identify and terminate files detected as HKTL_RADMIN.GA
- Windows Task Manager may not display all running processes. In this case, please use a third-party process viewer, preferably Process Explorer, to terminate the malware/grayware/spyware file. You may download the said tool here.
- If the detected file is displayed in either Windows Task Manager or Process Explorer but you cannot delete it, restart your computer in safe mode. To do this, refer to this link for the complete steps.
- If the detected file is not displayed in either Windows Task Manager or Process Explorer, continue doing the next steps.
Step 4
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\iplist
- {number} = {hex string}
- {number} = {hex string}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- Prot = {hex value}
- Prot = {hex value}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- Timeout = {hex value}
- Timeout = {hex value}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- EnableLogFile = {0 or 1}
- EnableLogFile = {0 or 1}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- LogFilePath = {full path of the log file, default is "c:\logfile.txt"}
- LogFilePath = {full path of the log file, default is "c:\logfile.txt"}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- FilterIp = {0 or 1}
- FilterIp = {0 or 1}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- DisableTrayIcon = {0 or 1}
- DisableTrayIcon = {0 or 1}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- AutoAllow = {0 or 1}
- AutoAllow = {0 or 1}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- AskUser = {0 or 1}
- AskUser = {0 or 1}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- EnableEventLog = {0 or 1}
- EnableEventLog = {0 or 1}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- NTAuthEnabled = {0 or 1}
- NTAuthEnabled = {0 or 1}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC\Parameters
- Para = {hex string}
- Para = {hex string}
Step 5
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC
- iplist
- iplist
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSDTC
- Parameters
- Parameters
Step 6
Search and delete this file
- {variable path and filename, default is "c:\logfile.txt"}
Step 7
Scan your computer with your Trend Micro product to delete files detected as HKTL_RADMIN.GA. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


