The IoT Attack Surface: Threats and Security Solutions
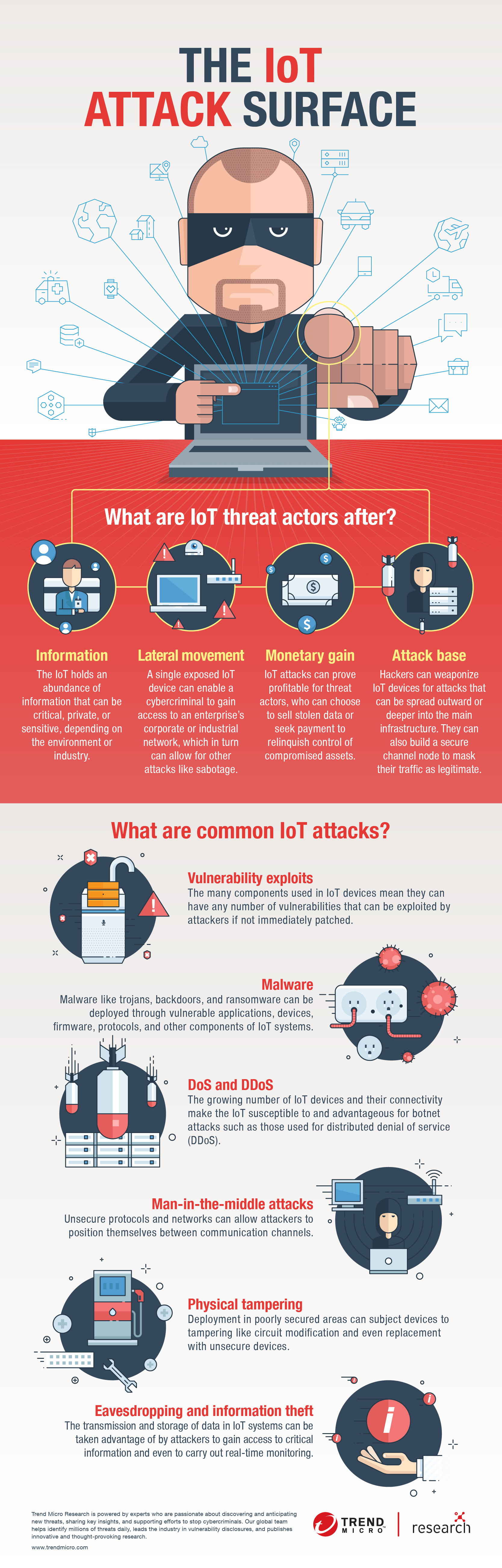
 View Infographic: The IoT Attack Surface
View Infographic: The IoT Attack Surface
The internet of things (IoT) is easily one of the most versatile technologies in existence today. The ubiquity of the internet, the growing capacity of network connection, and the diversity of connected devices make the IoT scalable and adaptable. Food production, manufacturing, finance, healthcare, and energy are just a few of the industries that the IoT has revolutionized — specifically through its extension, the industrial internet of things (IIoT). At the same time, it has also led to the realization of smart homes, buildings, and even cities.
However, the growing reality of the IoT also means recognizing its possible consequences. In an enterprise setting, for example, the IoT is often seen in the office automation (OA) and operational technology (OT) areas. This translates to multiple IoT and IIoT devices deployed within an organization. Such a setup increases the possibility of threats in spaces that had never posed cybersecurity risks before. IoT devices in these common spaces can have an effect on critical systems, like the intranet and database servers, through the IoT systems’ data collection and monitoring capabilities. As a result, even threats that involve seemingly innocuous IoT devices such as smart toilets and smart coffee machines can have a great impact depending on the environment they are set up in.
Part of adopting the IoT, therefore, is anticipating what else the technology brings to the environments it is being applied to — not least of which are security concerns that can give rise to successful attacks on IoT systems and devices.
How does the IoT influence security?
Threats to IoT systems and devices translate to bigger security risks because of certain characteristics that the underlying technology possesses. These characteristics make IoT environments functional and efficient, but they are likely to be abused by threat actors.
These characteristics include:
- Gathering of abundant data. IoT sensors and devices gather highly detailed data from their environments and users. This data is necessary for the IoT environments to function properly. However, this data could mean several cascading negative effects if not secured or if stolen or otherwise compromised.
- Connection of virtual and physical environments. Many IoT devices are capable of functioning on the data they receive from their respective environments. This ability shortens the distance between virtual and physical systems. But while convenient for users, it can allow cyberthreats to translate to physical consequences more quickly, thereby generating a greater impact.
- Creation of complex environments. Complex IoT environments can now be created thanks to the growing availability and diversity of devices. “Complex” in the context of the IoT means that enough devices are working in a single IoT environment that dynamic interactions between its devices are possible. This complexity expands the capabilities of an IoT environment, but at the cost of a wider attack surface.
- Centralization of architecture. Applying a traditional centralized architecture to IoT systems can have a detrimental effect on security. A centralized architecture means that the data gathered by each device and sensor will be communicated to a base station. In an enterprise, the main database could be the very same one used by thousands of devices that gather an astonishing amount of data. This may be less costly than separate databases, but it comes at the risk of a wider attack surface that is intricately connected to a single root.
What are the attack surface areas of the IoT?
As part of its Internet of Things Project, the Open Web Application Security Project (OWASP) has published a detailed draft list of IoT attack surface areas, or areas in IoT systems and applications where threats and vulnerabilities may exist. Below is a summarization of the IoT attack surface areas:
- Devices. Devices can be the primary means by which attacks are initiated. Parts of a device where vulnerabilities can come from are its memory, firmware, physical interface, web interface, and network services. Attackers can also take advantage of unsecure default settings, outdated components, and unsecure update mechanisms, among others.
- Communication channels. Attacks can originate from the channels that connect IoT components with one another. Protocols used in IoT systems can have security issues that can affect the entire systems. IoT systems are also susceptible to known network attacks such as denial of service (DoS) and spoofing.
- Applications and software. Vulnerabilities in web applications and related software for IoT devices can lead to compromised systems. Web applications can, for example, be exploited to steal user credentials or push malicious firmware updates.
How can the IoT be secured?
As can be inferred from the aforementioned IoT attack surface areas, all of the major components of IoT systems can be exploited. Security should therefore be a priority in building and maintaining IoT systems. Regardless of the scale or the type of environment an IoT system is built into, security should be considered from the design phase to better integrate it in every aspect of the system — it should not be a mere accessory. In this way, the IoT system, from its individual devices to its overall configuration, can be tailored to be both functional and secure.
Here are some other security guidelines to consider:
- All data being gathered and information being stored should be accounted for. Every single piece of data and information circulated within an IoT system should be mapped accordingly. This does not only refer to what is gathered by the sensors and devices deployed in the environment, but it also refers to any possible credentials in automation servers or other IoT applications.
- Each device being connected to the network should be configured with security in mind. Secure settings should be ensured before connecting a device to the network. This includes using strong username and password combinations, multifactor authentication, and encryption.
- The organization’s security strategy should be built on the assumption of compromise. Although avoiding breach and compromise is important, acknowledging that there is no perfect defense against evolving threats can help in creating mitigation protocols that can significantly contain and reduce the effects of a successful attack.
- Each device should be physically secured. It is important to also take into account the physical accessibility of IoT devices. If an IoT device itself has no physical safeguards against tampering, it should be kept in a restricted place or secured with the appropriate locks or other tools. IP cameras, for example, can be tampered with directly if a cybercriminal reaches them. They could be implanted with malicious hardware or software that could cause system failures or spread malware.
With additional insights from Ziv Chang and Shin Li
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks