Cerber Ransomware Found on a U.S. Government Website
September 08, 2017
It hasn’t been determined how attackers were able to host the malware on the website and if any visitors were infected. It's possible that the site was hacked, or the site stored archives of email attachments that probably contained a malware-carrying file.
The variant found unwittingly hosted on the website has similarities to Cerber Version 6, the socially engineered spam emails loaded with a zipped attachment that contains a malicious JavaScript file. The various JavaScript files analyzed by Trend Micro revealed a three-pronged approach: directly download and execute its payload, create a scheduled task to run Cerber after two minutes, or run an embedded PowerShell script.
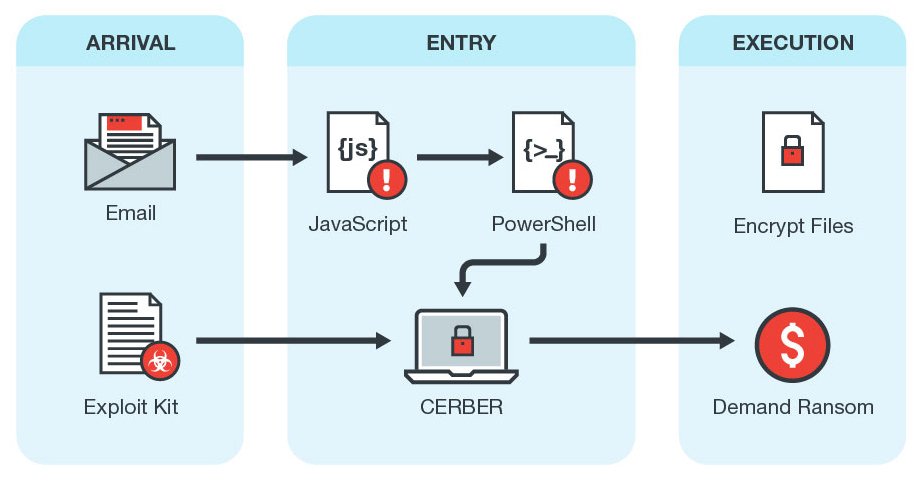
Figure 1. Infection chain of Cerber Version 6
Anubhav tweeted the discovery, and within hours, the link to the malware was taken down.
Every IT/system administrator should adopt these ransomware best practices to defend against threats like Cerber. In addition, an effective multilayered security solution adds to the strong security posture of systems and networks.
Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security can protect users and businesses from ransomware threats by detecting malicious files and spammed messages as well as blocking all related malicious URLs. Trend Micro™ Deep Discovery™ has an email inspection layer that can protect enterprises by detecting malicious attachment and URLs.
Trend Micro OfficeScan™ with XGen™ endpoint security actively detects this Cerber variant. It infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against ransomware and advanced malware. Our machine learning capabilities are tuned to account for attacks using techniques employed by ransomware like Cerber.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Posted in Cybercrime & Digital Threats
Recent Posts
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks