CVE-2010-3962: Yet Another Zero-Day Vulnerability Plagues IE
Nowadays, cybercriminals are prone to using zero-day vulnerabilities as part of their typical attack pattern. The software of known IT companies such as Microsoft and Adobe are likely targets of cybercriminals because they know that their products are not only installed into almost every desktop or laptop computer; these products are also widely and heavily used by computer users. In the white paper "2009's Most Persistent Malware Threats," which was released in March of 2010, TrendLabsSM categorized zero-day exploitation as one of the many prevailing threats in the Web to date. Furthermore, the white paper also mentioned several commonly targeted software like Internet Explorer (IE), Adobe Reader, and Adobe Acrobat.
Just recently, IE has once more become a target of a script exploit that took advantage of the way this browser handled invalid flag references. If left unpatched, IE could allow a remote malicious user to infiltrate a system without the user's knowledge.
How do users get this Web threat?
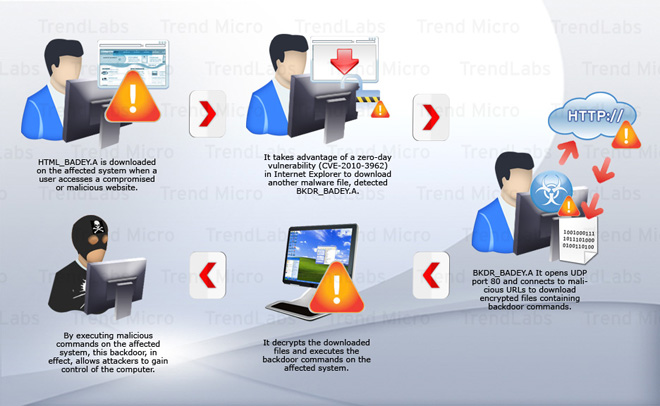
Users may acquire the exploit script code that targets this vulnerability by visiting Web pages that host it.
What happens once the threat gets inside computers?
After accessing a malicious Web page, the script searches for the vulnerability in IE. Once the vulnerability is spotted, the infected system attempts to connect to a URL to download a malicious file that Trend Micro detects as BKDR_BADEY.A. This backdoor program also connects to other URLs to download encrypted files. These files, when decrypted, contain commands that the backdoor program is capable of performing.
What is the driving force behind this threat?
The main purpose of HTML_BADEY.A in this attack is to penetrate a system by targeting an inherent vulnerability in IE in order to drop a backdoor program. Backdoor programs are normally installed onto systems for a number of reasons, the most common of which is to allow a remote malicious user to take control of an infected system in order to run codes on the system that aim to make it do whatever the malicious user wishes it to. Routines may range from downloading other malicious files onto infected systems to taking complete control of them.
What versions of IE are affected by the exploit?
The zero-day vulnerability is inherently found in the following versions:
- IE 6
- IE 7
- IE 8
How do affected users remove this threat?
Users are advised to refer to the following manual cleanup solutions for the related malware that exploit this vulnerability:
Are Trend Micro users protected from this threat?
Yes. Solutions supported by the Trend Micro™ Smart Protection Network™ detect and prevent the execution of the malicious files HTML_BADEY.A and BKDR_BADEY.A via file reputation technology. It also protects users by blocking access to malicious sites via the Web reputation technology as well as phone-home attempts wherein an infected computer tries to upload stolen data to or to download additional malware from command-and-control (C&C) servers.
Trend Micro clients using OfficeScan with Intrusion Defense Firewall (IDF) plug-in are already protected from this Web threat since rule identifier number 1004496. An updated version of the said rule has been included in IDF pattern 10-035.
What can users do to prevent this threat from entering computers?
Microsoft users can download the patch for this vulnerability in this Web page:
From the Field: Expert Insight
Roland Dela Paz, one of our threat analysts, has this to say about how in-demand exploits are in the underground market: "Undeniably, [exploiting] zero-day vulnerabilities is one of the most effective approaches in proliferating malware. In the underground, it is a growing industry where cybercriminals sell exploits that target inherent software vulnerabilities in the form of pay-per-install (PPI) services, exploit kits, or even the exploit concept/idea itself to other cybercriminals. There is money on exploits, as they say in the underground."