Old Cybercrime Tactics Come into Play with New Malware
December 17, 2012
Cybercriminals employ various methods for stealing information, with social engineering and malware infection being the most common. We see especially successful ones in the form of survey scams on social networking sites, phishing mails for corporate employees, and fake links on search results. Just when you think people are starting to evade these old tactics, cybercriminals spice it up on different planes.
What is this threat about?
A slew of notable malware have been using the same old recipes, except, with definite twists. These new threats have nuanced differences that make them volatile once in contact with significant pieces of information. They are:
- The targeted WORM_NARILAM.A and WORM_NARILAM.B;
- Highly damaging BKDR_MAKADOCS.JG; and
- Password- and file- stealing TSPY_PASSTEAL.A and TSPY_PIXSTEAL.A
How do these threats arrive and propagate?
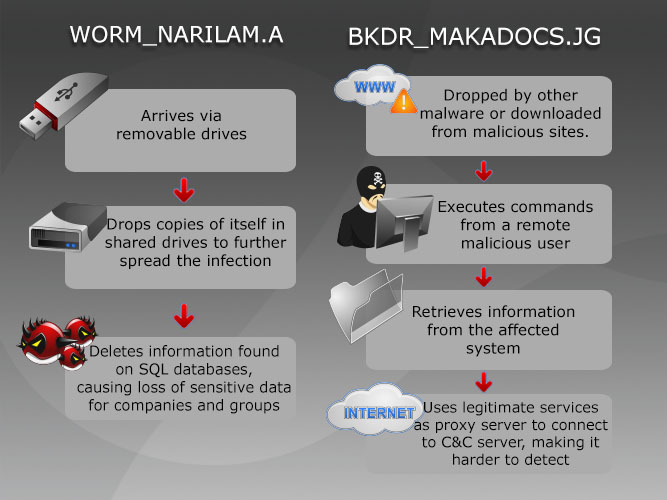
WORM_NARILAM.A and WORM_NARILAM.B may be downloaded from removable drives or shared on a network of unsuspecting users. It then goes on to copy itself on the system. BKDR_MAKADOCS.J uses Microsoft Word documents that can either be downloaded directly from the Internet or dropped by other malware. The malware can detect if the target system is running on Windows 8, which is a relatively new addition to their target operating systems. It can then spread through compromised networks or sites, and system vulnerabilities.
Users can download TSPY_PASSTEAL.A and TSPY_PIXSTEAL.A when visiting malicious sites. It is also dropped by other malware. Searching for illegal files such as pirated software, pirated e-books and license key generators can lead to the software packaged with the malware. PASSTEAL has already infected 400 systems. Read more about PASSTEAL and PIXSTEAL here: PIXSTEAL and PASSTEAL Sport New Ways To Steal Data.
What happens when users execute these threats on their systems?
WORM_NARILAM.A and WORM_NARILAM.B
- The worm drops copies of itself in shared drives.
- It deletes information in SQL databases by doing the following: a.Updates random records from several tables, b. Deletes random records from several tables, and c. Deletes tables and stored procedures.
- This backdoor remotely executes these commands: terminate itself, download and execute files, change IP, and open command line.
- It continues by stealing information from the target, such as domain name, GUID, host name, user name, Windows version, and more.
- It then uses legitimate site, http://docs.google.com as its proxy server to communicate with its C&Cs, thus avoiding detection.
- This info-stealing malware steals account login credentials using password recovery apps in browsers, such as PasswordFox in Firefox. Details about the extraction routine are found here.
- It sends the files to FTP site ftp://{BLOCKED}.{BLOCKED}.67.232.
- This spyware copies files with .JPG, .JPEG, and .DMP extensions. Here we explain how it happens.
- It sends the files to FTP site ftp://{BLOCKED}.{BLOCKED}.208.90.
WORM_NARILAM.A and WORM_NARILAM.B are highly destructive malware that destroy databases. BKDR_MAKADOCS.J can open a target system for further malicious attacks. Depending on the affected target, these threats can have a wide range of effects. Financial loss can be a primary concern for individuals and big companies. In the same way, cybercriminals can use TSPY_PASSTEAL.A and TSPY_PIXSTEAL.A to spy on or infect other computers. The keylogging techniques of PASSTEAL put sensitive information and data privacy at risk. The data gathered from users can be used for blackmail or theft, making them more vulnerable.
Why are these threats notable?
WORM_NARILAM.A and WORM_NARILAM.B stand out because of its destructive ability to delete and/or damage databases. This time Middle Eastern corporations were targeted with the intent to sabotage information. The NARILAM worm is a reminder that the threat of losing sensitive information remains. BKDR_MAKADOCS.J, on the other hand, is noted for its method of evasion. Its use of Google Docs to communicate with command-and-control (C&C) servers reminds of how popular services are often abused for malicious purposes. Lastly, TSPY_PASSTEAL.A and TSPY_PIXSTEAL.A both intend to steal user information like keyloggers. TSPY_PASSTEAL.A extracts passwords from browsers through password recovery apps while TSPY_PIXSTEAL.A steals image files.
Are Trend Micro users protected from this threat?
Yes. Trend Micro product users are protected from this threat via the Trend Micro™ Smart Protection Network™, which proactively identifies and mitigates threat incidents such as this. Trend Micro customers receive the Web, Email, and File reputation services, which all work hand in hand in blocking threats.
What can users do to prevent these threats from affecting their computers?
With threats like these that abuse legitimate services, users need to be cautious when using online services and physical drives. Here are some tips and best practices:
- Companies are advised to follow strict protocols in employee use of flash drives that may be infected with malware like the destructive NARILAM worm strains.
- Refrain from searching for illegal or pirated software, and downloading applications from untrustworthy sources. These actions may lead to malware like MAKADOCS, PIXSTEAL, and PASSTEAL.
- Practice safe browsing habits like disabling browser scripts. Don’t save passwords on browsers, and regularly clear your cookies/cache.
- Be aware of social engineering tactics, like how MAKADOCS was packaged into Microsoft Word documents. Be familiar with the popular services and searches cybercriminals use.
- Take advantage of two-factor authentication (TFA) offered by online services like Google, Dropbox, and Facebook to secure your account further.