BKDR_REMOSH.IC
Backdoor:Win32/Remosh.gen!A (Microsoft)
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Backdoor
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This backdoor deletes its dropper component after the DLL is installed as service.
Its service name is randomly selected, based on the result of a certain registry query.
Before continuing to execute, it checks a certain signature/configuration at the end of the file. If a match is found, it may do several actions.
In addition, if the connection to the command and control server is successful, it can also do several routines.
However, during testing, the malware fails to decrypt its C&C server from the file.
This backdoor may be downloaded by other malware/grayware/spyware from remote sites. It may be downloaded by other malware/grayware from remote sites.
It bears the file icons of certain applications to avoid easy detection and consequent removal.
TECHNICAL DETAILS
Arrival Details
This backdoor may be downloaded by other malware/grayware/spyware from remote sites.
It may be downloaded by the following malware/grayware from remote sites:
- SWF_AGENT.AA
Installation
This backdoor drops the following component file(s):
- %System%\ati2exx.dll - detected as BKDR_REMOSH.IC
(Note: %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.)
It bears the file icons of the following applications:
- Notepad
Its DLL component is injected to the following process(es):
- svchost.exe
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- pe
Autostart Technique
This backdoor registers as a system service to ensure its automatic execution at every system startup by adding the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{random service name}
NOTES:
It deletes its dropper component after the DLL is installed as service.
Its service name is randomly selected, based on the result of the following registry query:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost\netsvcs
If one of the resulting names does not exist in the following registry, it uses this name to register its DLL component:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
Before continuing to execute, it checks a certain signature/configuration at the end of the file. If a match is found, it may do the following:
- Disable PolicyAgent service
- Connect to a remote server and wait for commands
If the connection to the command and control server is successful, it can do the following routines:
- remotely control the keyboard and mouse
- get drive information
- find / list files
- execute files
- create / delete / move files
- execute commands using CMD
- capture screenshot
However, during testing, the malware fails to decrypt its C&C server from the file.
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Remove malware files dropped/downloaded by BKDR_REMOSH.IC
- SWF_AGENT.AA
Step 3
Scan your computer with your Trend Micro product and note files detected as BKDR_REMOSH.IC
Step 4
Restart in Safe Mode
Step 5
To delete the random service key this malware/grayware created:
- Scan your computer with your Trend Micro product and take note of the name of the malware/grayware/spyware detected.
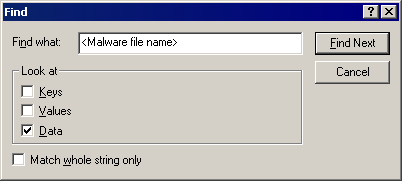
- Open Registry Editor. To do this, click Start>Run, type regedit in the text box provided, then press Enter.
- Press CTRL+F.
- In the Find dialog box, type the file name of the malware detected earlier.
(Note: Make sure that only the data checkbox is selected, then click Find Next.) - Once found, in the right panel, check if the result is the following value-data pair:
ImagePath = {malware/grayware path and file name} - If yes, in the left panel, locate the service where the data is under.
- Right-click on the located service in the left panel and choose Delete.
- Repeat steps 2 to 6 until the Finished searching through the registry dialog box appears.
- Close Registry Editor.
Step 6
Search and delete these files
Step 7
Restart in normal mode and scan your computer with your Trend Micro product for files detected as BKDR_REMOSH.IC. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 8
Scan your computer with your Trend Micro product to delete files detected as BKDR_REMOSH.IC. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.


