Coinminers Exploit SaltStack Vulnerabilities CVE-2020-11651 and CVE-2020-11652
 By Govind Sarda and Suraj Sahu, Threat Researchers
By Govind Sarda and Suraj Sahu, Threat Researchers
Recently, researchers from F-Secure disclosed two high-severity vulnerabilities in SaltStack Salt: CVE-2020-11651, an authentication bypass vulnerability, and CVE-2020-11652, a directory traversal vulnerability. These can be exploited by remote, unauthenticated attackers, and all versions of SaltStack Salt before 2019.2.4 and 3000 before 3000.2 are affected. SaltStack also released a bulletin regarding these vulnerabilities. We have witnessed attacks exploiting these vulnerabilities, notably those using the cryptocurrency miners detected as Coinminer.Linux.KINSING.A, Coinminer.Linux.KINSING.B, Coinminer.Linux.KINSING.C, Coinminer.Linux.MALXMR.SMDSL64, and Coinminer.Linux.MALXMR.UWEKP.
SaltStack Salt is a Python-based, open-source software for event-driven IT automation, remote task execution, and configuration management. Its management framework is used in data centers and cloud servers. It is also an infrastructure as code (IaC) solution and is used in DevOps. We analyzed the critical vulnerabilities affecting Salt, their patches, and some threats exploiting them.
[Read: Security risks and best practices for using IaC tools and templates.]
CVE-2020-11651 and CVE-2020-11652
CVE-2020-11651 allows remote user access, and CVE-2020-11652 permits arbitrary directory access. We can take a look at Salt’s architecture to understand the vulnerabilities. Salt has a master-slave model where the master is called the salt master and the slaves are salt minions. The salt master is used to send commands and configurations to the salt minions. A single master can manage multiple minions.
Figure 1. Command execution model between the salt master and salt minions
In CVE-2020-11651, the salt master process, ClearFuncs, does not validate method calls properly. This class exposes two methods:
- _prep_auth_info() method, which returns the user token (Root Key). Attackers can use the token to bypass authentication, resulting in remote command execution within the context of the Salt process on both the master and minions.
- _send_pub() method, which can be used to queue messages directly on the master publish server. Such messages can be used to trigger minions to run arbitrary commands as root.
To summarize, this vulnerability allows access to some methods without requiring authentication. This then can be used to retrieve user tokens from the salt master and run commands on salt master and salt minions.
CVE-2020-11652 is also related to the salt master process ClearFuncs; this time, it allows access to some methods that improperly sanitize paths. The salt wheel module contains commands used to read and write files under specific directory paths. The get_token()method of the salt.tokens.localfs fails to sanitize the token input parameter, which is then used as a filename, allowing insertion of ".." path elements and thus reading of files outside of the intended directory. This occurs due to the failure to correctly sanitize the token input parameter, which is used as a filename with the only restriction is that the file has to be deserializable by salt.payload.Serial.loads(). This gives attackers a chance to rewrite path elements.
Patch Analysis
To fix the CVE-2020-11651 vulnerability, SaltStack has defined exposed methods that the user can specify in the cleartext messages. This is done through a new function called get_method()
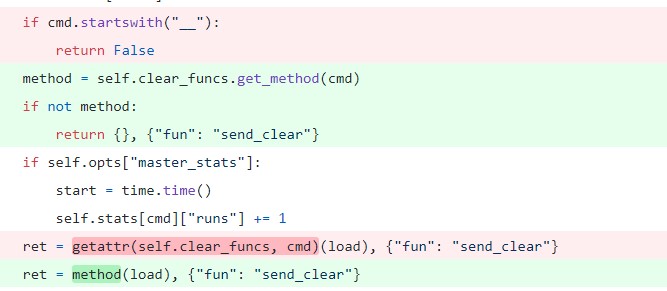
Figure 2. Use of new function get_method()
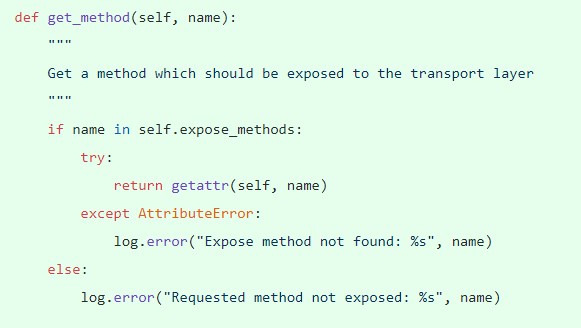
Figure 3. The function get_method() checks exposed methods
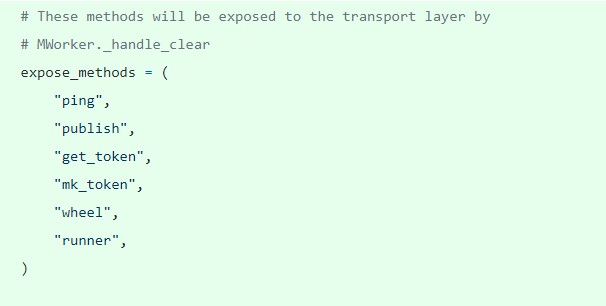
Figure 4. Methods exposed to transport layer
To fix the CVE-2020-11652 vulnerability, SaltStack has sanitized paths in ClearFuncs methods provided by the salt master. This ensures that access to unintended files and directories are not allowed. They added two new functions: _realpath() to resolve any filesystem links, and clean_path() to verify paths.
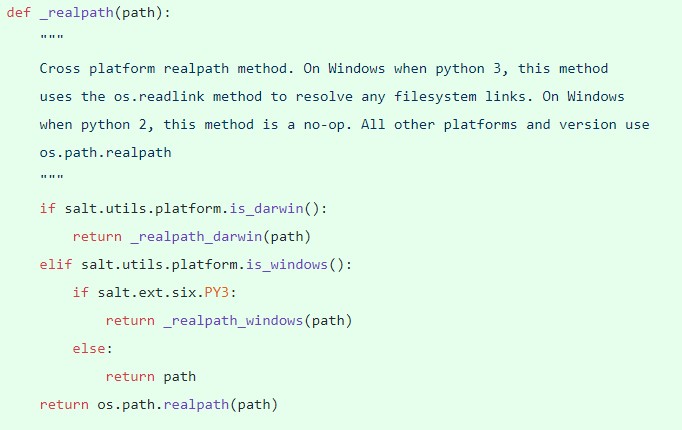
Figure 5. The new _realpath() function, which resolves any filesystem links
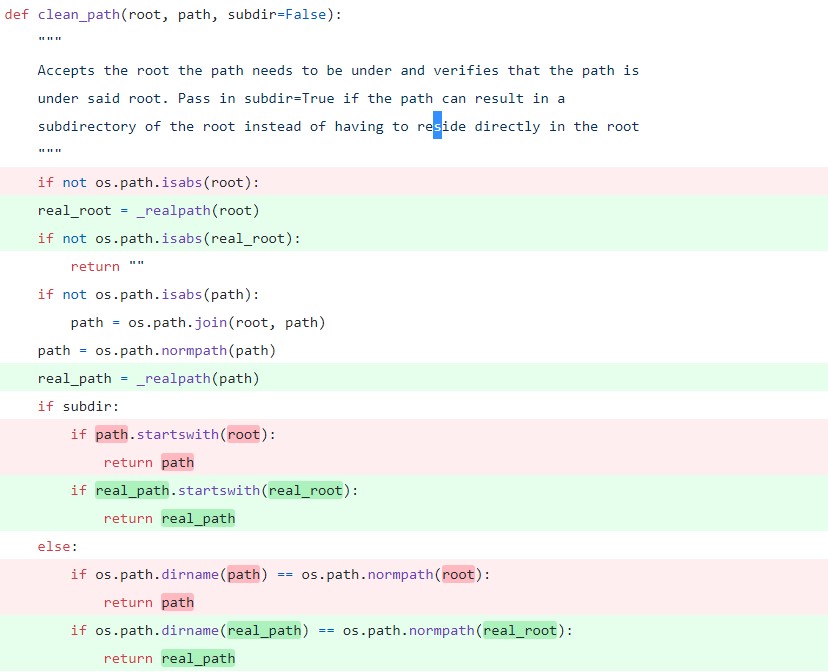
Figure 6. The clean_path() function verifies that the path is under the said root
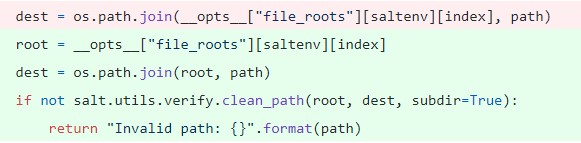
Figure 7. Use of the clean_path()function to verify the path
Threats Exploiting CVE-2020-11651 and CVE-2020-11652
We have spotted coinminers actively exploiting CVE-2020-11651 and CVE-2020-11652, which we detect as follows:
- Coinminer.Linux.KINSING.A
- Coinminer.Linux.KINSING.B
- Coinminer.Linux.KINSING.C
- Coinminer.Linux.MALXMR.SMDSL64
- Coinminer.Linux.MALXMR.UWEKP
The tables below show data we recorded from May 3, only a few days after the vulnerability was disclosed. The File full path column pertains to the path where the malware is being dropped, process full path means the path of the binary file of the process execution, and platform count is the number of machines reported in this detection.
The file full path is either /tmp/salt-minions or /var/tmp/salt-store, while while the process full path was any of the following:
- [salt-store]
- /usr/bin/bash
- /usr/bin/md5sum
- /usr/bin/python2.7
- /usr/bin/wget
- /var/tmp/salt-store
Red Hat Enterprise Linux Server release 7.2 (Maipo) had the highest number of recorded detections at 315,265.
| OS Name | File Full Path | Process Full Path | Number of Instances | Total Detection |
| Red Hat Enterprise Linux Server release 7.2 (Maipo) |
/tmp/salt-minions |
/var/tmp/salt-store
|
185
|
315,265 |
| CentOS Linux release 7.5.1804 (Core) |
/tmp/salt-minions | /var/tmp/salt-store |
75 | 117,453 |
| CentOS Linux release 7.7.1908 (Core) | /tmp/salt-minions | /var/tmp/salt-store | 2 | 5,194 |
| CentOS Linux release 7.4.1708 (Core) | /tmp/salt-minions | /var/tmp/salt-store | 1 | 2,192 |
| CentOS Linux release 7.6.1810 (Core) | /tmp/salt-minions | /var/tmp/salt-store | 1 | 2,114 |
| Red Hat Enterprise Linux Server release 7.2 (Maipo) | /tmp/salt-minions | [salt-store] | 1 | 1 |
Figure 8. Detections with /tmp/salt-minions as file full path
| OS Name | File Full Path | Process Full Path | Number of Instances | Total Detection |
| Red Hat Enterprise Linux Server release 7.2 (Maipo) |
/var/tmp/salt-store |
/usr/bin/md5sum
|
120
|
1,357 |
| Red Hat Enterprise Linux Server release 7.2 (Maipo) |
/var/tmp/salt-store | /usr/bin/bash |
113 | 900 |
| Red Hat Enterprise Linux Server release 7.2 (Maipo) | /var/tmp/salt-store | /usr/bin/wget |
84 | 680 |
| CentOS Linux release 7.5.1804 (Core) | /var/tmp/salt-store | /usr/bin/md5sum |
36 | 440 |
| CentOS Linux release 7.5.1804 (Core) | /var/tmp/salt-store | /usr/bin/bash | 34 | 289 |
| CentOS Linux release 7.5.1804 (Core) | /var/tmp/salt-store | /usr/bin/wget | 28 | 221 |
| CentOS Linux release 7.7.1908 (Core) | /var/tmp/salt-store | /usr/bin/md5sum | 1 | 19 |
| CentOS Linux release 7.6.1810 (Core) | /var/tmp/salt-store | /usr/bin/md5sum | 1 | 17 |
| CentOS Linux release 7.7.1908 (Core) | /var/tmp/salt-store | /usr/bin/bash | 1 | 12 |
| CentOS Linux release 7.6.1810 (Core) | /var/tmp/salt-store | /usr/bin/bash | 1 | 10 |
| CentOS Linux release 7.6.1810 (Core) | /var/tmp/salt-store | /usr/bin/wget | 1 | 10 |
| CentOS Linux release 7.7.1908 (Core) | /var/tmp/salt-store | /usr/bin/wget | 1 | 10 |
| CentOS Linux release 7.3.1611 (Core) | /var/tmp/salt-store | /usr/bin/md5sum | 1 | 1 |
| CentOS Linux release 7.4.1708 (Core) | /var/tmp/salt-store | /usr/bin/python2.7 | 1 | 1 |
| CentOS Linux release 7.5.1804 (Core) | /var/tmp/salt-store | [salt-store] | 1 | 1 |
Figure 9. Detections with /var/tmp/salt-store as file full path
Recommendations
Cybercriminals will always look for vulnerabilities to exploit. Vulnerabilities in one system can also be used to compromise other connected systems; for example, vulnerabilities in Salt may also expose the data stored in data centers and cloud servers to risk. Users should patch vulnerabilities in platforms and devices as soon as they can to strengthen security. Security solutions can also help defend against related threats.
The following Deep Security rulesprotect users from threats exploiting these vulnerabilities:
- 1010265 - SaltStack Salt Authorization Weakness Vulnerability (CVE-2020-11651)
- 1010266 - SaltStack Vulnerabilities Exploitation Detected
- 1010267 - SaltStack Salt Directory Traversal Vulnerability (CVE-2020-11652)
Below are the applicable Tipping Point rules:
- 37032 - HTTP: Backdoor.Linux.Kinsackor.A Runtime Detection
- 37750 - TCP: SaltStack Salt Authentication Bypass Vulnerability (CVE-2020-11651)
- 37782 - TCP: SaltStack Salt Directory Traversal Vulnerability (CVE-2020-11652)
For hybrid cloud environments, the Trend Micro™ Hybrid Cloud Security solution offers automated security within the DevOps pipeline. It is empowered by multiple XGen™ threat defense techniques for protecting runtime physical, virtual, and cloud workloads.
We also recommend Trend Micro Cloud One™ solutions, which help users simplify their hybrid and multi-cloud security. They can address workload, container, file object storage, serverless and application, and network security, along with security posture management. Trend Micro Cloud One™ – Workload Security secures modern data centers, including physical servers and software, virtual servers, and desktop. Trend Micro Cloud OneTM Network Security inspects network traffic without disrupting business operations, providing network layer protection and disruption for the multi-cloud environment.
Indicators of Compromise
| SHA-256 | Trend Micro Pattern Detection |
| 81909cf7d6c7427d87c8f45f3a056d0186d931126655d4963b1bb2c8147d083f | |
| 837d768875417578c0b1cab4bd0aa38146147799f643bb7b3c6c6d3d82d7aa2a | Coinminer.Linux.KINSING.B |
| 98d3fd460e56eff5182d5abe2f1cd7f042ea24105d0e25ea5ec78fedc25bac7c | Coinminer.Linux.KINSING.C |
| 9fbb49edad10ad9d096b548e801c39c47b74190e8745f680d3e3bcd9b456aafc | Coinminer.Linux.KINSING.A |
| b618781f971528796dc5aa1030987b9112a544b7dc5b3bd0f818cc105142d717 | Coinminer.Linux.MALXMR.UWEKP |
| cf0c05027f7ae00f3e5406ed49c952a575aaee9e55d9d4737be365bcf4cdb16d | Coinminer.Linux.MALXMR.SMDSL64 |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks