Falling victim to a business email compromise (BEC) scam has long been touted as a problem that generally arises from human negligence. The human factor combined with the seeming immunity of scam emails to cybersecurity solutions’ detection methods make BEC a persistent threat that users and organizations must continue to take seriously.
According to the Federal Bureau of Investigation (FBI), this scheme has already caused US$12.5 billion losses to companies as of 2018. This shows that BEC scams, while usually technically simple, are highly effective. We actively track BEC attempts and recorded 9,291 BEC attempts in 2018 Q1-Q3, a 46-percent increase from last year’s 6,342 in the same period. In our data, the U.S., Australia, and the U.K emerged as the top three countries most targeted by scammers.
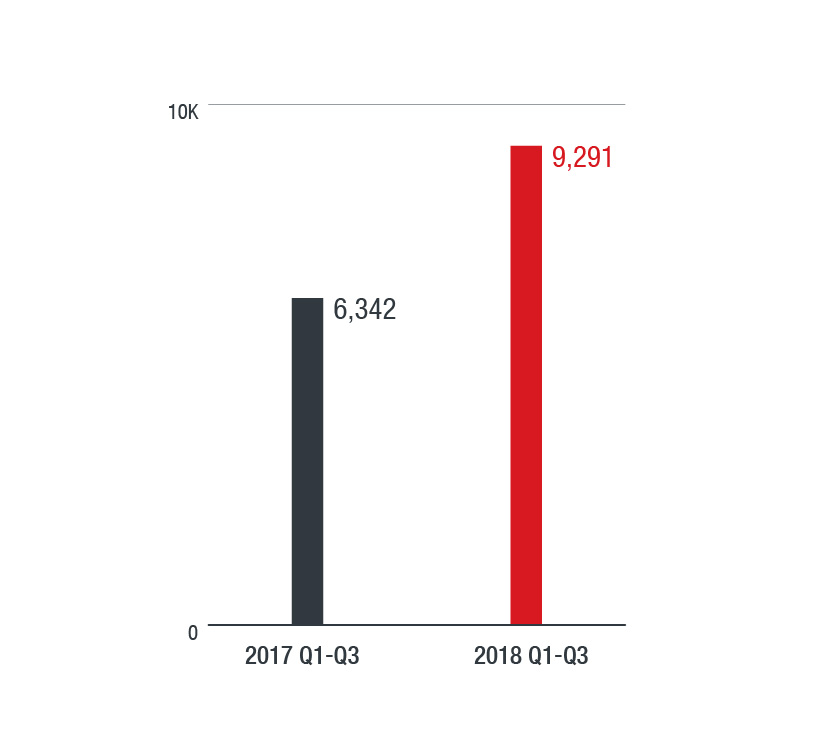
Trend Micro recorded 9,291 BEC attempts in 2018 Q1-Q3
— a 46-percent increase from 2017 Q1-Q3
I
nstead of relying on high-skill technical methods, BEC scammers bank heavily on social engineering schemes, exploiting human nature to yield hefty gains. While the ubiquity of tech services in enterprise environments has prompted BEC scammers to impersonate Microsoft and Amazon in their display name deception tactics, they have continued to imitate high-ranking members of a company to intercept or divert money transfers. For 2018, data from Trend Micro™ Smart Protection Network™ security infrastructure shows that CEOs and Managing Directors/Directors are the most-spoofed executives.
To keep abreast of the landscape that BEC scammers are operating in, we look back on some of the noteworthy incidents and trends that made BEC a headline staple this year.
Pathé, a popular French film production and distribution company, found itself in a situation fit for a legal drama movie when a former employee filed a lawsuit citing unfair dismissal. A BEC scam that cost Pathé more than US$21 million was believed to be the trigger for the dismissal of its Amsterdam-based financial director.
On March 8, scammers sent a BEC email to the Amsterdam branch managing director. The email, which impersonated Pathé’s chief executive, asked the managing director to make a confidential payment of over US$900,000. Although the managing director forwarded the email to an assistant and discussed it with the finance director, the email was not spotted as a scam and eventually led to five consecutive money transfers to scammers in less than a month. Pathé’s losses due to the scam may be the biggest reported stolen amount from a single company for this year.
On top of losses due to the theft, Pathé incurred losses due to the legal dispute with the finance director. The former won and the court demanded Pathé to pay compensation, gross pension, and other emoluments.
T
he Australian Competition and Consumer Commission’s (ACCC) Scamwatch reported that the number of BEC scam incidents has increased by a third in 2018, with reported losses reaching AU$2.8 million dollars. The ACCC Deputy Chair noted that there is a misconception that BEC scammers target only small businesses, one that is debunked by the fact that Australian medium-sized businesses constituted the biggest numbers in reports and losses in the commission’s data.
Various organizations can be affected, from charities and local sporting clubs to real estate agents and the construction industry, with one losing more than AU$300,000.
BEC accounts for 63 percent of business losses reported to ACCC — a troubling figure that has prompted the commission to encourage Australian businesses to immediately review their process of verifying and paying accounts and invoices.
In September, CNBC reported about the unfortunate experience of two anonymous fraud victims who lost not just six-figure sums but also their dream houses and, for one individual, majority of his/her life savings. Theirs was not an isolated case. The FBI highlighted in a public service announcement (PSA) in July that there is a trend of BEC scammers targeting people in the real estate sector, for example, buyers, sellers, title companies, law firms, and agents.
The FBI noted that, from 2015 to 2017, there was an increase of over 1,100 percent in the number of victims from real estate transactions. May 2018 saw the highest number of reports of real estate victims while September 2017 had the highest recorded victim loss. Most victims reported being deceived by spoofed emails during real estate transactions, wherein they were directed to send funds to a falsified domestic account.
Scammers are able to worm their way into the digital space of victims by using public information on real estate listing sites. Such information may include for-sale homes, the status of a sale, as well as the real estate agent’s contact information.
C
ybercriminals in Nigeria have been known for posing as people in financial need, online love interests, or generous princes. Now, they appear to be expanding their business by branching out to BEC schemes — a move that can potentially earn them hundreds of millions of dollars a year.
Crowdstrike, which reported on the Black Axe gang, found that targets range from semiconductor makers to U.S. schools. Gang members impersonated executives and lawyers to lure victims into transferring huge sums of money to bank accounts. Their schemes seem to have paid off as they flaunt luxurious lifestyles on social media. Security researchers who have been tracking Nigerian cybercriminal gangs also note the gangs’ focus on social engineering, at times even using video calls. Once transferred, the defrauded money is laundered through bank accounts in China and other Asian countries.
L
aw enforcement agencies worldwide have been keeping a close watch on BEC scams due to the huge losses year on year since the FBI started recording in 2013. A testament to this is Operation WireWire, what is possibly the biggest crackdown on BEC scammers, which culminated in June. The major coordinated law enforcement initiative of the FBI, the Department of Justice, the Department of Homeland Security, the Department of the Treasury, and the U.S. Postal Inspection Service, with the help of partner agencies in multiple countries, led to the arrest of 74 people in the U.S., Nigeria, Canada, Mauritius, and Poland. The operation disrupted fraudulent wire transfers, leading to the recovery of about US$14 million, and seized an additional US$2.4 million.
The FBI Director, Christopher Wray, said the bureau will continue working with law enforcement agencies in other countries to stop fraud schemes like BEC and protect citizens’ assets.
After Operation WireWire, more arrests and indictments were made. In the same month, eight people were arrested for involvement in an Africa-based BEC conspiracy which swindled individuals and companies alike of US$15 million in a span of six years. In August, a man was arrested in Los Angeles for allegedly using six different false identities to open 23 bank accounts for fraudulent wire transfers. In one instance, his accomplice sent spoofed emails to a victim, leading to the transfer of US$531,981 to an account of a woman, who, in turn, transferred $60,000 to one of his fraudulent accounts.
I
n our security predictions for 2019, apart from high-ranking company members, we predict that BEC scammers will target employees further down the company hierarchy, for example, secretaries or executive assistants. Because of its crafty nature — and human nature — usual cybersecurity best practices and solutions may be rendered futile. But there are security technologies available now that can help users and organizations avoid falling for it.
Writing Style DNA, which is used by Trend Micro Cloud App Security™ (CAS) and ScanMail™ Suite for Microsoft® Exchange™ (SMEX), can help detect email impersonation tactics used in BEC and similar scams. It uses artificial intelligence (AI) to recognize the DNA of a user’s writing style based on past emails and then compares it to suspected forgeries. The technology verifies the legitimacy of the email content’s writing style through a machine learning model (ML) that contains the legitimate email sender’s writing characteristics. When an email is suspected of spoofing high-profile users or their subordinates, the writing style is compared to a trained ML model and a warning is sent to the implied sender, the recipient, and the IT department.
To minimize the risk of BEC, addressing the human factor is critical. Cybersecurity awareness training and enforcing best practices against email threats can help stop scammers in their tracks. These, when supported by advanced security technologies (for example, Writing Style DNA) that interoperate with other security layers, build an effective defense against BEC scams and other cyber-enabled threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks