Holiday Hazards: Thanksgiving and Black Friday Cyberthreats
 As people prepare for Thanksgiving meals and Black Friday deals, cybercriminals are also prepping to take advantage of the holidays to spread malware — and not holiday cheer — to unsuspecting victims. The holiday season brings with it a spam campaign with a malicious payload (detected by Trend Micro TROJAN.W97M.POWLOAD.NSFGAICM)that takes advantage of Thanksgiving Day to spread malware via doc file attachments. Meanwhile, a Black Friday scam is also out to fool Amazon customers via the messaging platform WhatsApp, luring them with big discounts and directing them to a bogus phishing website.
As people prepare for Thanksgiving meals and Black Friday deals, cybercriminals are also prepping to take advantage of the holidays to spread malware — and not holiday cheer — to unsuspecting victims. The holiday season brings with it a spam campaign with a malicious payload (detected by Trend Micro TROJAN.W97M.POWLOAD.NSFGAICM)that takes advantage of Thanksgiving Day to spread malware via doc file attachments. Meanwhile, a Black Friday scam is also out to fool Amazon customers via the messaging platform WhatsApp, luring them with big discounts and directing them to a bogus phishing website.
On November 19, we saw emails under the guise of Thanksgiving Day e-cards being pushed by cybercriminals in a spam campaign.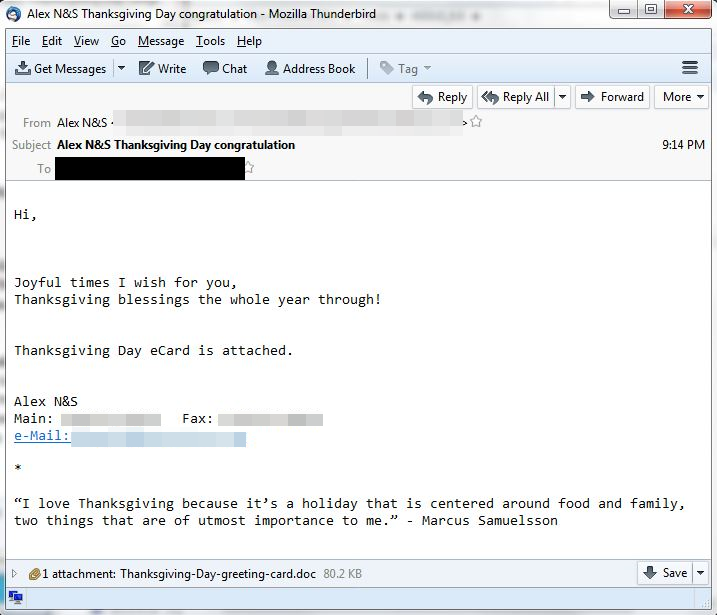
Figure 1. A sample of a spam Thanksgiving Day e-card
According to other security researchers, this spam email campaign may be delivering the modular malware Emotet to users. We also saw a spike in Emotet-laden spam emails using filenames that contain “Thanksgiving Day wishes” or “greetings” on November 21.
Trend Micro researchers also learned that cybercriminals use this malware sample in other non-Thanksgiving Day campaigns written in other languages, which could indicate that it is part of a bigger spam campaign.
[READ: Exploring Emotet: Examining Emotet’s Activities, Infrastructure]
Figure 2. An email
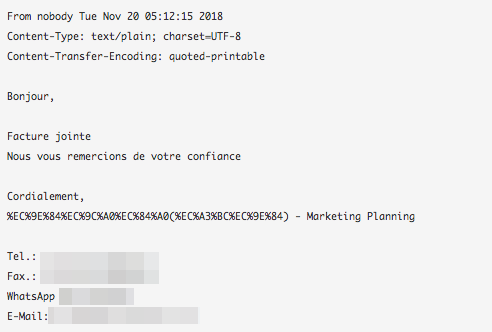
Figure 3. Another email belonging to the same spam campaign, this time, a fake invoice written in French
As spam campaigns become more believable, the need for a multilayered cybersecurity defense — one that has machine learning technology that helps catch spam campaigns from even reaching the user’s network let alone endpoint — has become more vital.
Meanwhile, another scheme that takes advantage of the gift-buying season is an Amazon discount scam hosted on popular messaging platform WhatsApp. Scammers have been sending spam WhatsApp messages offering massive discounts on items sold on the online retail giant to users in an attempt to trick them into clicking on a malicious URL to get.
According to a report published by The UK Mirror, links in the spam email redirects users to a phony Amazon page with products listed at extremely discounted prices, prompting users to click on one of them. Once a product is clicked, the fake Amazon site will then ask for a user’s personal information, including name and address.
Before a user gets to order the selected products on the fake Amazon site, a pop-up message that tells the user to forward the phishing message to 10 other WhatsApp users will then show.
The legitimate-looking link sent via this phishing campaign may be hard to spot, especially by untrained eyes or just overly eager shoppers scrambling for a great deal. However, smarter machine learning technology can detect these using vast amounts of training data from previous scams of similar nature.
[READ: Online Shopping Trends and Threats]
Defense against Phishing and Spam
To protect users against spam, enterprises can take advantage of Trend Micro™ endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free™ Business Security. Both solutions protect users and businesses from threats by detecting malicious files and spammed
The use of artificial intelligence (AI) and machine learning in Trend Micro™ email security products enhances overall cyberdefense against BEC, EAC, phishing, and other advanced threats. Trend Micro’s anti-phishing technology combines the knowledge of a security expert with a self-learning mathematical model to identify fake emails by looking at both behavioral factors and the intention of an email.
Trend Micro has also introduced FraudBuster, which analyzes the contents of an email, SMS, or chat message from messaging platforms such as WhatsApp, to determine the likelihood of it being a scam. Users are encouraged to check any message using the free
Indicators of Compromise
SHA256
06b7dcb5a08ed82a6182ad36c7e35ae3d81ad9b6fe6ca680fb04c238c4c65174
06c1fedabd752ef45bf35734da85897ef54f190fa0f55d1237120004e09e00c4
0dd63006ea9f148c7a310fc7677d3da51d9b677dc99d6ab84f902c41b36fec95
0e03f25f622017458c02de65506b8e8fb42b62bf6e401823867cd9598f830250
19e792895aa7835226208383d5caa6c9e067ba2ca4f5c21a5059006890f07599
373d40fedd7b44f123f9bdbac7be2598bcabe1cfec11791baae70b22f65e09ab
3ec5ec4634d13040182f50f445536b506960ecc945577e19554ba273d5da3135
5a9a02e35e618cd4e54116d4a92b740a8d5ad4e02ee448f58b94e33b26c6fde2
7ecf4a01520a75371bd5e10c65128b26411d2af54768abc0b85882f78c5ee102
82f879769ae7ac5be14de12680cb00cfab9d0501cf9679b546c9e6dcb3a5f870
a622796460072d842226d23be56d6f88490459f1af200ae34ec7bdce95207e77
b537766706d224dc704870c5bb393b0b73529793999fb19b67cf3ed2e89280cc
b755fef3f2df6a4474d1cf723c530371201ab87f171b8b89e45408649c48fea5
b7d529e8a412b5b680f36c64ed2c7e9f34f8106bb83ddccdec82337120726d36
da7e56efabcc602eb0433d106dcbf706bb8d1928a5ac630734f74fded213a52b
e249871dff11114bc166a106bfb84b8200386d6eb53a204dc402f8e391b4e0cb
ed68ff1f66adf3a2b69b29e1f9174bd4e1ae1d60c05e44cf2d5bf77590f50786
f93099bc1e256aed382485ad3dc32d7ebde27b198c6c7befb840e80de608e910
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks