GOLROTED Targets Small and Medium-Sized Businesses

When it comes to cybercrime, it doesn’t matter if the perpetrator/s behind it are groups collaborating or an individual working alone. In the end, users and businesses get victimized, resulting to loss of confidential data and/or money. Recent reports have indicated several solo operators that have significantly affected their targets. For instance, a 20-year old Brazilian with the moniker ‘Lordfenix’ made profit by creating more than fifty online banking malware while the cybercriminal known as Frapster, stole credit card details using malware bought from other cybercriminals.
We also observed two Nigerian scammers run separate operations, which employed a simple keylogger known as Hawkeye that affected small and medium-sized businesses in India, Egypt, and Iran among others. Hawkeye, also known as GOLROTED, was used to obtain information and knowledge about their victims’ partners, affiliates, and business contacts to launch more scams. As such, it enables them to move laterally across larger organizations related to the original victims. For instance, a regional office was initially targeted, to gain entry to the company’s global office.
How does GOLROTED arrive on user systems?
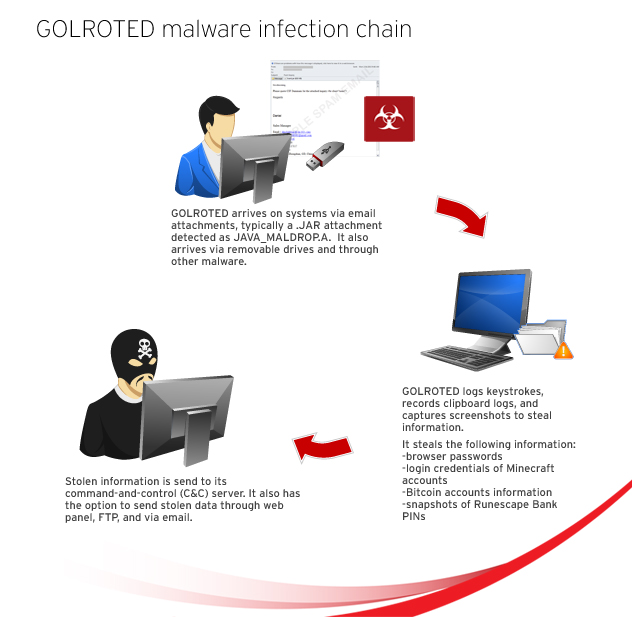
GOLROTED, which is Trend Micro’s detection for both Hawkeye and Predator Pain, arrives on user systems via email attachments. These attachments typically arrive as a .JAR file detected as JAVA_MALDROP.A. GOLROTED may also arrive via removable drives and through other malware.
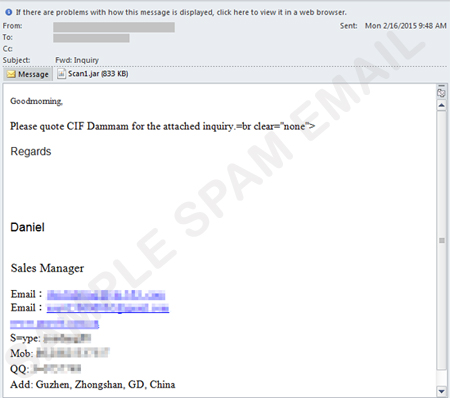
Figure 1. Screenshot of a spammed email with GOLROTED attachment
What are the routines of GOLROTED?
This malware family exhibits various behaviors and routines depending on its variants. In the variants that we analyzed, we observed that a modified copy of Mail PassView is embedded on the malware enabling it to steal passwords from certain email clients. We also saw that the embedded copy of WebBrowserPassView is capable of stealing browser passwords.
Apart from passwords, this malware also gathers login credentials of accounts of the game, Minecraft. In addition, it also gets the STEAM login, typically used when playing DOTA 2. It also obtains data by logging keystrokes, recording clipboard logs, and capturing screenshots. All stolen information is sent to its command-and-control (C&C). It also has the option to send stolen data through web panel. However, using this option may result in GOLROTED’s incapability to send stolen screenshots from the infected systems. Note that only when the malware is preconfigured to send stolen information via FTP and email does the latter routine (take and send screenshots) is performed on the infected system.
When executed on the system, GOLROTED also steals information from Bitcoin accounts. Snapshots of Runescape Bank PINs, a security feature for Runescape accounts, are also sent to the cybercriminals.
Specific variants, however, contain modified versions of ProduKey and SkypeContactsView thus enabling it to gather product keys for MS Office (2003, 2007), Windows Exchange Server (7, Vista), and SQL Server, and Skype contact details.
What makes this threat notable?
GOLROTED is our detection for both Predator Pain and Hawkeye. Both are simple keyloggers capable of stealing a wide array of information of its targets and victims. In the independent operations that used Hawkeye, instead of selling the stolen data in the cybercriminal underground, the cybercriminals used it to know more details about their targets to launch other attacks. It became a stepping stone for bigger prey, expanding their target base. Moreover, this keylogger played a crucial role in change of supplier fraud wherein they hijack transactions in business emails and send alternative payment details. As a result, the payments go straight to the cybercriminals’ pockets.
Both Hawkeye and Predator Pain are commercially available tools in the cybercriminal underground. Hawkeye, for instance, can be bought for only $35. Cracked versions can also be purchased in underground forums. Meanwhile, Predator Pain is sold for the amount of $40 or less. This means that other cybercriminals who may not have enough technical skills can just buy these run-of-the-mill information-stealing malware in order to carry out their own attacks.
Who are the affected entities by this threat?
Based on our Smart Protection Network feedback, Predator Pain and Hawkeye mostly targeted small and medium-sized businesses. Predator Pain is able to gain a whopping amount of $75 million US dollars in six months in targeting businesses in Hong Kong alone. In addition, 5% of Hawkeye’s victims by country distribution came from Hong Kong.

Figure 2. Predator Pain/Limitless Victims by Country
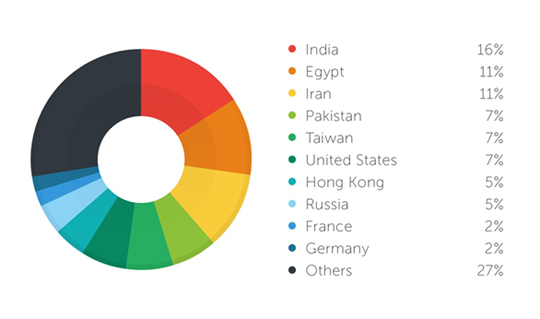
Figure 3. Hawkeye Victims by Country
This highlights the fact that everyone is a potential target and that attackers do not necessary limit their targets to enterprises only. We surmise that SMBs do not have the security technologies that most enterprises have due to limited budget allocation, but they encounter the same security threats and risks as enterprises do.
Are Trend Micro users protected?
Yes. Trend Micro secures user systems from GOLROTED via its Trend Micro Custom Defense that detects and blocks email messages with malicious attachments and links that contained GOLROTED variants. As such, it protects even before reaching its intended targets and opening the email messages, which can start the whole infection chain.
Small businesses can employ Trend Micro Worry-Free™ Business Security that has anti-malware technology that can detect GOLROTED variants and web reputation that blocks all related URLs and IPs. It also protects data by blocking threats and via content filtering of email messages.
What can users and organizations do to protect their systems?
Apart from installing security solutions that has file, web, and email reputation technologies to detect and block GOLROTED, users and organizations are recommended to delete suspicious emails even though it came from seemingly known sources. It is also best to keep abreast with the knowledge on the latest security threats that can pose risks to your organization. These days, whether it’s a cybercrime enterprise or solo venture in cybercriminal operations, you can be a potential target, no matter the size of your company.