TROJ_QDDOS.A
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Trojan launches a denial of service (DoS) attacks against websites under the .kr domain. Once these sites receive a more-than sufficient amount of requests from various sources, these sites may be taken offline. According to media reports, South Korea has raised the cyber alert level following the DoS attacks, which uses this Trojan.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
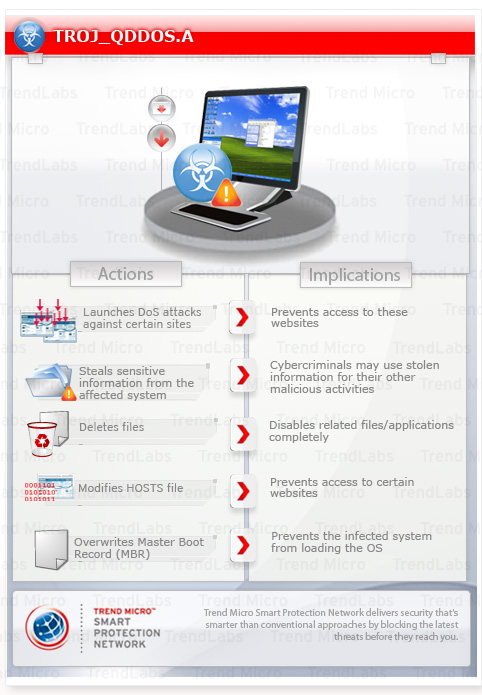
This Trojan deletes files that use certain extensions. It also overwrites the Master Boot Record (MBR), with special conditions depending on the operating system of the affected computer. These routines are triggered by certain conditions regarding the system date of the infected computer.
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
It launches denial of service (DoS) attacks against certain websites. It does the said routine to prevent users from reaching these sites at a given time.
It executes the dropped file(s). As a result, malicious routines of the dropped files are exhibited on the affected system.
TECHNICAL DETAILS
Arrival Details
This Trojan arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Autostart Technique
This Trojan registers itself as a system service to ensure its automatic execution at every system startup by adding the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\SvcHost
m{3 random alphabetic characters}svc = "m{3 random alphabetic characters}svc"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\SvcHost
w{2 random alphabetic characters}csvc = "w{2 random alphabetic characters}csvc"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\SvcHost
s{3 random alphabetic characters}svc = "s{3 random alphabetic characters}svc"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
Type = "20"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
Start = "2"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
ErrorControl = "1"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
ImagePath = "%System Root%\system32\svchost.exe -k m{3 random alphabetic characters}svc"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
DisplayName = "Microsoft DNS resolve Service"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
ObjectName = "LocalSystem"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
Description = "Provides DNS resolve.If this service is stopped, system cannot be well performed"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc\Parameters
ServiceDll = "%System Root%\system32\m{3 random alphabetic characters}svc.dll"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
Type = "20"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
Start = "2"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
ErrorControl = "1"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
ImagePath = "%System Root%\system32\svchost.exe -k s{3 random alphabetic characters}svc"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
DisplayName = "Removal stoarage Service"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
ObjectName = "LocalSystem"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
Description = "Allows Removal stoarage.If this service is stopped, system cannot be well performed"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc\Parameters
ServiceDll = "%System Root%\system32\s{3 random alphabetic characters}svc.dll"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
Type = "20"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
Start = "2"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
ErrorControl = "1"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
ImagePath = "%System Root%\system32\svchost.exe -k w{2 random alphabetic characters}csvc"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
DisplayName = "Windows DNS Security controler Service"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
ObjectName = "LocalSystem"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
Description = "Transmits DNS Security controler.If this service is stopped, system cannot be well performed"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc\Parameters
ServiceDll = "%System Root%\system32\w{2 random alphabetic characters}csvc.dll"
It registers as a system service to ensure its automatic execution at every system startup by adding the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\m{3 random alphabetic characters}svc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\s{3 random alphabetic characters}svc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\w{2 random alphabetic characters}csvc
Denial of Service (DoS) Attack
This Trojan launches DoS attacks against the following websites:
- naver.com
- daum.net
- auction.co.kr
- hangame.com
- dcinside.com
- gmarket.co.kr
- cwd.go.kr
- mofat.go.kr
- nis.go.kr
- unikorea.go.kr
- assembly.go.kr
- korea.go.kr
- dapa.go.kr
- police.go.kr
- nts.go.kr
- customs.go.kr
- mnd.mil.kr
- jcs.mil.kr
- army.mil.kr
- airforce.mil.kr
- navy.mil.kr
- usfk.mil
- dema.mil.kr
- kunsan.af.mil
- kcc.go.kr
- mopas.go.kr
- kisa.or.kr
- ahnlab.com
- fsc.go.kr
- kbstar.com
- wooribank.com
- hanabank.com
- keb.co.kr
- shinhan.com
- jeilbank.co.kr
- nonghyup.com
- kiwoom.com
- daishin.co.kr
- korail.com
- khnp.co.kr
Dropping Routine
This Trojan drops the following files:
- %System%\faultrep.dat - non-malicious file
- %System%\tlntwye.dat - non-malicious file
- %System%\tljoqgv.dat - encrypted list of sites to DDoS; non-malicious file
- %System%\noise03.dat - non-malicious file
(Note: %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.)
It drops the following files:
- %System%\rtdrvupr.exe - also detected as TROJ_QDDOS.A
- %System%\m{3 random alphabetic characters}svc.dll - also detected as TROJ_QDDOS.A
- %System%\w{2 random alphabetic characters}csvc.dll - also detected as TROJ_QDDOS.A
- %System%\s{3 random alphabetic characters}svc.dll - also detected as TROJ_QDDOS.A
(Note: %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.)
It executes the dropped file(s). As a result, malicious routines of the dropped files are exhibited on the affected system.
Download Routine
This Trojan connects to the following URL(s) to download its component file(s):
- {BLOCKED}.{BLOCKED}.11.82 at TCP port 443
- {BLOCKED}.{BLOCKED}.253.166 at TCP port 443
It saves the files it downloads using the following names:
- nt{2 random alphabetic characters}{2 random numeric characters}.dll - also detected as TROJ_QDDOS.A
NOTES:
Information Theft
This Trojan retrieves the following information from the affected system:
- User name of the currently logged on user
- Computer name
- Malware path and file name
- Path and file name of the parent process of the malware
Other Details
This Trojan does the following:
- Connects to the IP addresses where it downloads files also to send and receive information
- Searches files with the following extensions:
- .alz
- .asp
- .aspx
- .c
- .cpp
- .doc
- .docm
- .docx
- .eml
- .gho
- .gul
- .h
- .hna
- .hwp
- .java
- .jsp
- .kwp
- .mdb
- .php
- .ppt
- .pptx
- .pst
- .rar
- .wpd
- .wpx
- .wri
- .xls
- .xlsx
- .zip
- Overwrite files' contents with zeros
- Compress files then changes their extension names to .cab
- Password protect archived files using 8 random character strings
- Avoids searching for file types to delete on the following folders:
- Windows Program Files folder
- Windows folder
- Overwrites the Master Boot Record (MBR). It does this by writing zeros on the first sector of \.\PhysicalDrive0 using the WriteFile API. If the operating system of the infected system runs on Windows Vista or higher, it writes 512 Bytes of zeros. Otherwise, it writes 4,194,304 Bytes. Overwriting the MBR prevents systems from loading the OS.
- Drops %Windows%\KB24919.log when this Trojan is successfully installed on the system
- Deletes the URL, http://sub.{BLOCKED}ox.co.kr/SBUpdate.exe, from the cache
This Trojan's routines of modifying files and deleting the MBR are triggered when the system date of the affected system is earlier than the date specified in its component file, %System%\noise03.dat, or when the said file is not present in the system.
It performs DoS attacks on systems by continuously sending random data at UDP port 80 to the target sites.
SOLUTION
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Identify files detected as TROJ_QDDOS.A, then restore the Master Boot Record and delete malware files using Recovery Console
Step 3
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
- m{3 random alphabetic characters}svc
- m{3 random alphabetic characters}svc
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
- s{3 random alphabetic characters}svc
- s{3 random alphabetic characters}svc
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services
- w{2 random alphabetic characters}csvc
- w{2 random alphabetic characters}csvc
Step 4
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer's registry.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SvcHost
- m{3 random alphabetic characters}svc = m{3 random alphabetic characters}svc
- m{3 random alphabetic characters}svc = m{3 random alphabetic characters}svc
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SvcHost
- w{2 random alphabetic characters}csvc = w{2 random alphabetic characters}csvc
- w{2 random alphabetic characters}csvc = w{2 random alphabetic characters}csvc
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SvcHost
- s{3 random alphabetic characters}svc = s{3 random alphabetic characters}svc
- s{3 random alphabetic characters}svc = s{3 random alphabetic characters}svc
Step 5
Remove these strings added by the malware/grayware/spyware in the HOSTS file
Step 6
Search and delete these files
- %System%\faultrep.dat
- %System%\noise03.dat
- %System%\tlntwye.dat
- %System%\tljoqgv.dat
- %Windows%\KB24919.log
Step 7
Restart in normal mode and scan your computer with your Trend Micro product for files detected as TROJ_QDDOS.A. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 8
Restore files from backup Only Microsoft-related files will be restored. If this malware/grayware also deleted files related to programs that are not from Microsoft, please reinstall those programs on your computer again.
NOTES:
Trend Micro Threat Management Services detects and blocks this Trojan via the Threat Discovery Appliance (TDA). This Trojan is detected in the following TDA patterns:
- Network Content Correlation Pattern (NCCP) 1.10487.00
- Network Content Inspection Pattern (NCIP) 1.10527.00
Did this description help? Tell us how we did.


